HiveNightmare aka SeriousSam Local Privilege Escalation in Windows – CVE-2021-36934

This means that a regular (non-admin) user can extract data from these files and access system secrets, local users’ hashed passwords, computer account password, service accounts in clear-text (including domain service accounts configured to run services on the system) and other information.
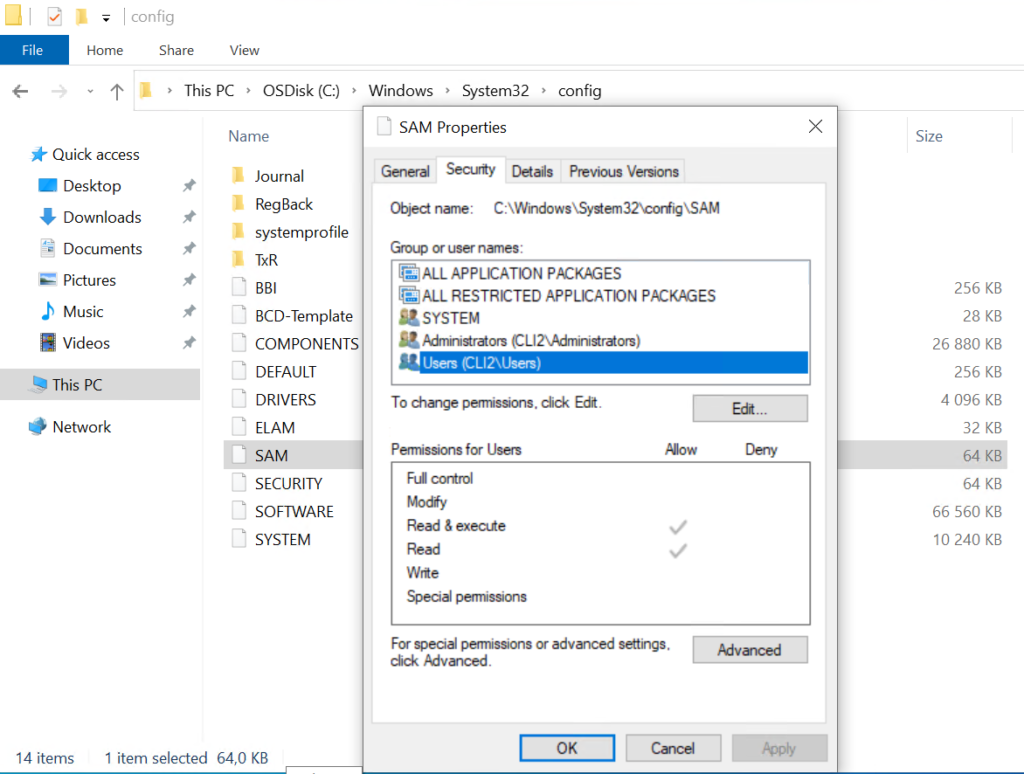
The registry files are normally locked but they can easily be accessed when “System Protection” is enabled by simply accessing the shadow copy of the system drive.
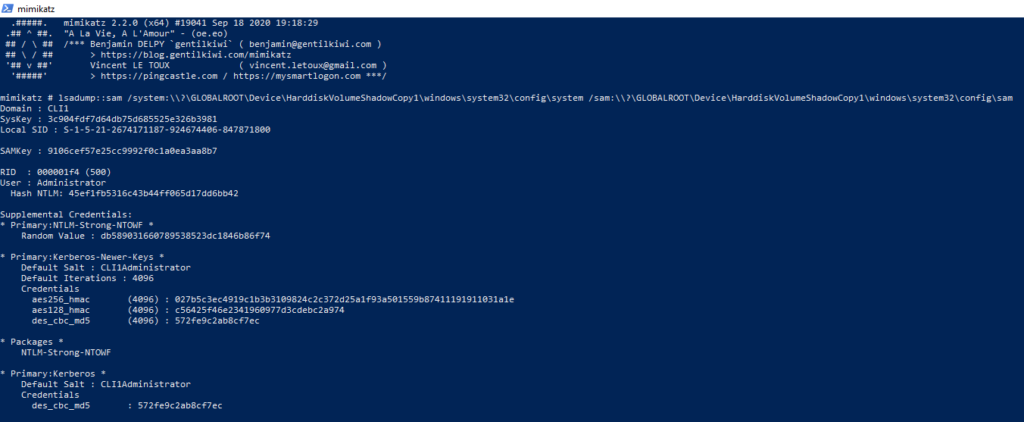
The initial reports say Windows 11 and 10 version 1809 and above are vulnerable.
EDR solutions should already monitor any access to SAM, SYSTEM and other registry files and should already cover this case.
As a shadow copy is needed since the registry files are loaded and locked by the system, to prevent users from accessing these files a short-term workaround is to disable the “System Protection”. This will remove any previous shadow copies from the system. As an additional consequence, it will not be possible to revert to the state of the system before the last upgrade.
NOTE: this will remove the volume shadow copies that were taken by the system protection function (enabled by default on Windows 10 systems with a system drive of 128GB or larger). If you have any other mechanisms creating shadow copies for the affected registry files, you should handle those separately.
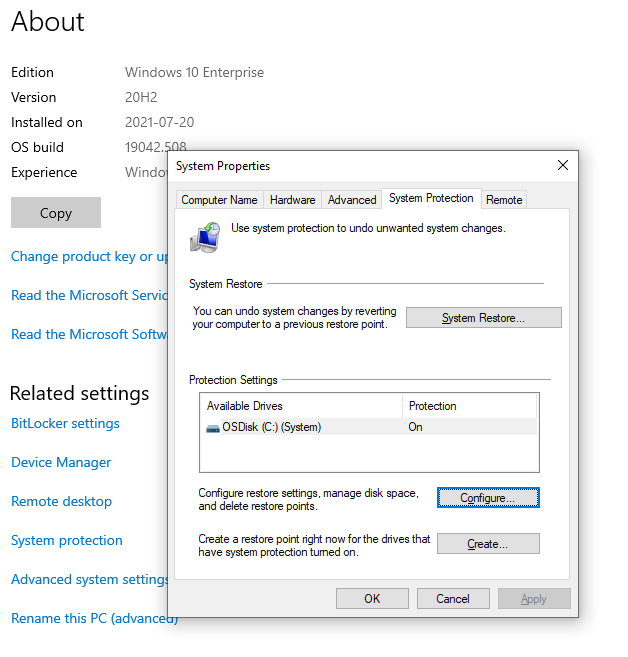
The setting can be disabled from “System Properties” as shown below.
Initial discovery by @jonasLyk
UPDATE JULY 21, 2021
Microsoft has assigned CVE-2021-36934 to this vulnerability and included the following recommended workarounds
Restrict access to the contents of %windir%system32config
- Open Command Prompt or Windows PowerShell as an administrator.
- Run this command:
icacls %windir%system32config*.* /inheritance:e
Delete Volume Shadow Copy Service (VSS) shadow copies
- Delete any System Restore points and Shadow volumes that existed prior to restricting access to %windir%system32config.
- Create a new System Restore point (if desired).
Impact of workaround Deleting shadow copies could impact restore operations, including the ability to restore data with third-party backup applications.
Note You must restrict access and delete shadow copies to prevent exploitation of this vulnerability.
