Ransomware Attacks Linked to Russian Sanctions
Truesec has determined that it’s possible that some ransomware gangs are now coordinating their efforts with the Russian government.

Coincidence or Not?
Truesec is currently assisting a European corporation that has been hit by a ransomware attack. We usually don’t release the details of an attack we’re currently working on until the entire incident has been properly analyzed and some time has passed. This time, however, we have permission to release some important details as a warning to other western organizations.
Until recently, the victim company had conducted business with Russia and sold parts to the Russian government. Initially, after the invasion of Ukraine, the company had explored the possibility of obtaining an exemption from the sanctions regime against Russia but decided not to pursue this option. Instead, the company notified Russian authorities that it would stop all deliveries to Russia until further notice. Within 30 hours of this notification, the company was attacked with ransomware.
Who Is the Threat Actor?
The threat actor is a Russian ransomware gang known as Team Snatch. Team Snatch has been active since early 2019, but according to some sources, they ceased activities in 2020. However, in the autumn of 2021, Team Snatch seems to have returned. We are convinced that Team Snatch is a mostly Russian gang, as they only recruit Russian-speaking hackers, according to a report from Sophos.
In November 2021, the Swedish car company Volvo was reported to have been hacked by Team Snatch. Volvo admits that some R&D data was stolen but claims that Team Snatch did not deploy any ransomware in that attack.
As far as Truesec is aware, Team Snatch is one of the few ransomware gangs that doesn’t run a ransomware-as-a-service (RaaS) operation. However, they do recruit new members to their team, as shown in the report from Sophos. This is probably one reason they are less notorious than other gangs, which depend on media coverage of their heists to increase their popularity among freelance affiliate hackers.
Possible Ties to the War in Ukraine
This is not the only attack attributed to Team Snatch that appears to coincide with sanctions on Russia. On March 25, 2022, the day after the Russian invasion of Ukraine and the West signaled massive sanctions on Russia in return, it was reported that Team Snatch had successfully breached the U.S. fast food company McDonald’s.
A few days after the invasion, Team Snatch also released a now-deleted tweet that appears to indicate support for the Russian war effort, like the FIN12 or Conti syndicate has done.
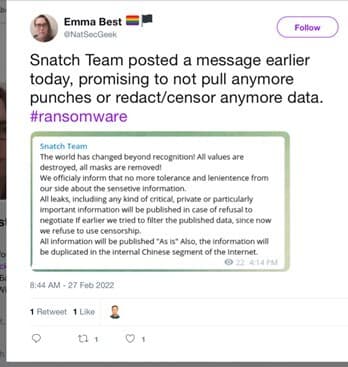
We have previously noted that ransomware gangs that don’t run an RaaS operation appear to be less shy about collaborating with the Russian secret services than those that do.
This may all be a coincidence. It’s also possible that Team Snatch’s decision to strike was based on the victim’s refusal to seek exemption from the sanctions against Russia, possibly even in coordination with the Russian government.
