Truesec Expands Service Portfolio with Identity & Access Management (IAM)

A new area of expertise has been added to Truesec’s services through an acquisition of Truesec DK. We’re focusing on Identity & Access Management (IAM) to ensure the security of your organization’s critical data.
Do You Know Who Can Access Your Critical Data?
It might seem like a simple question, but for businesses, it can be complicated and even a bit nerve-wracking during audits.
The threat landscape is evolving. Cybercriminals don’t just breach networks anymore; they target users like employees, contractors, vendors, and even software bots. When a user account is compromised, cybercriminals can access everything that the user has permission to. To prevent breaches, it’s crucial to limit employees’ access to what they need for their jobs.
IAM’s core goal is to ensure the right people have the right access, for the right reasons, at the correct times, with approval from the right authorities in the organization.
Why IAM?
- Automate on- and offboarding of employees and externals to ensure that the right people get access and access is removed when people leave the company.
- Simplify the process of reviewing user access rights, and report on the results for compliance and audit purposes.
- Identify accounts with no owner (orphan accounts) and react.
- Provide self-service to the business and ensure access requests are approved before granted. This efficient user administration and, at the same time, strengthens security around data.
- Secure your data, efficient your user administration, and strengthen your security to prevent breaches.
How We Help You
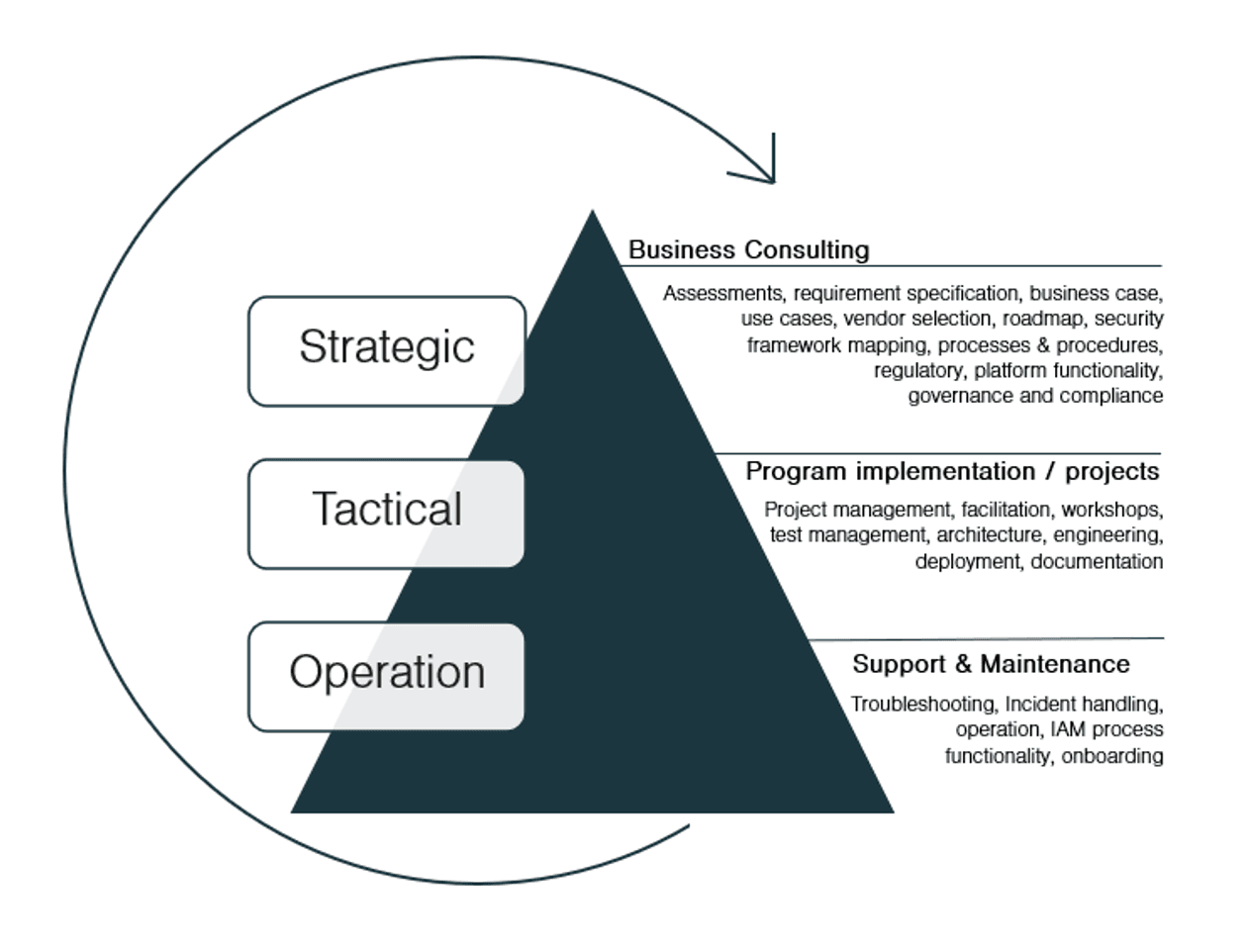
At Truesec, we are a reliable partner, and we help our customers on their IAM journey, regardless of their maturity level and whether the business drivers are focused on efficiency, compliance, and/or security.
We partner with the reliable market leader, SailPoint, and are experts in their technologies.
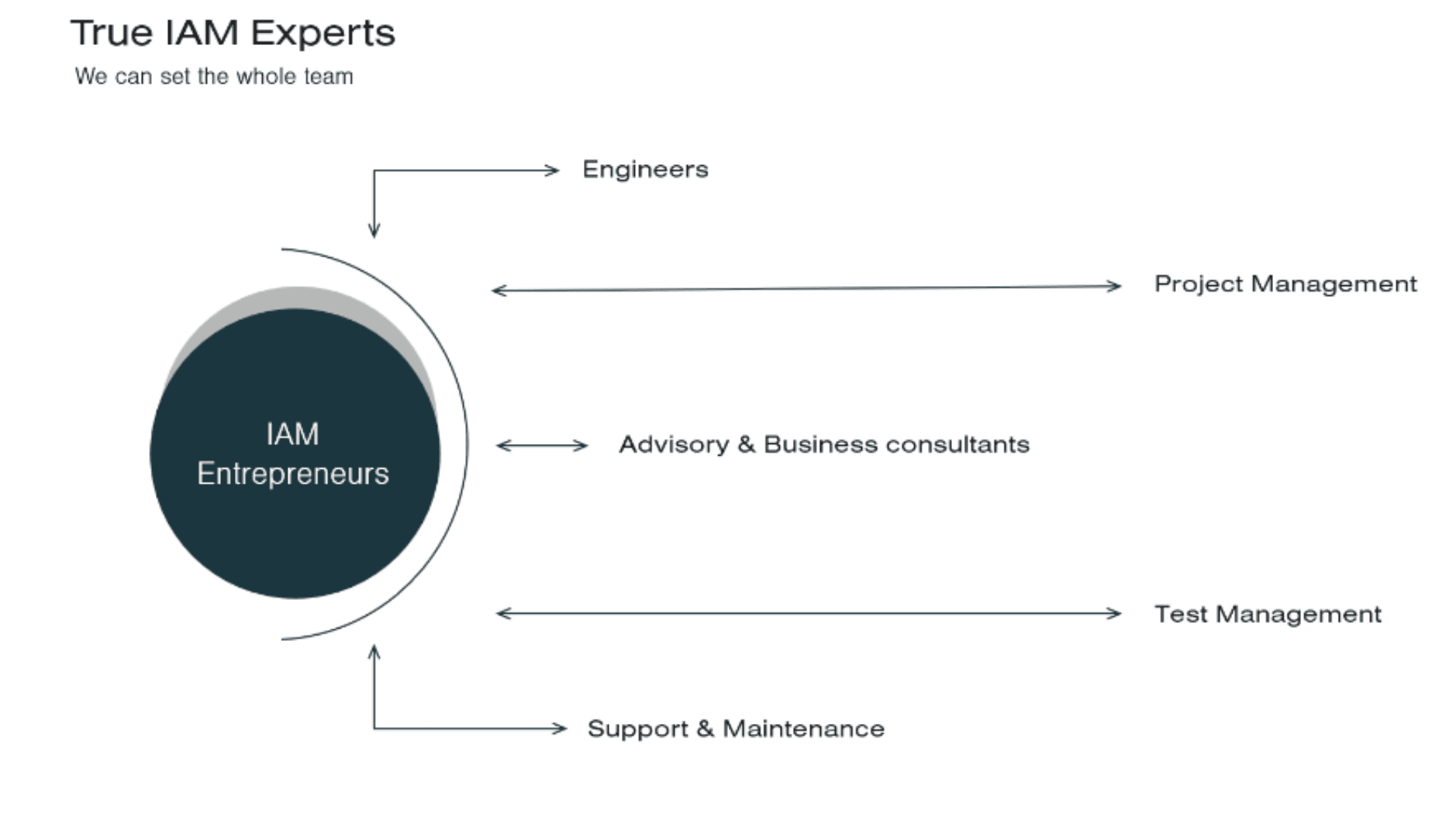
Who We Are
We are an IAM multiskilled team of experts with skillsets that cover all abilities and offerings within the IAM area, ensuring we can scale all solutions ranging from engineering the technical solution to program implementation, training of stakeholders, clarifying and setup processes, ensure governance and compliance, conduct project management, provide functional support, and more.