Understanding the Threat: What is Business Email Compromise?
Understanding the Threat: What is Business Email Compromise?
Business email compromise (BEC) stands as one of the most common forms of cyber attacks, with it’s financially driven motives impacting organizations of all sizes. Stolen invoices in combination with a compromised email account are weaponized in the fraud. Resulting in a so called CFO Scam.

The Business Email Compromise attacks typically involve threat actors exploiting compromised mailboxes, such as Microsoft Office365 accounts, to gain access to invoices. The documents are then used to conduct fraud, either targeting the account owner or a business partner. This blog post aims to take a detailed, step-by-step look at this form of cyber attack, and provide useful tips to help mitigate its impact.
Step 1 – Adversary-in-the-Middle (AiTM) Attack
The threat actor gains initial access to the mailboxes through their Microsoft Office 365 identity. Typically this involves a sophisticated Phishing email using the Adversary-in-the-Middle (AiTM) technique. So what is this cyber attack?
An AiTM attack involves a phishing email typically sent from a compromised mailbox. Therefore, this means that the phishing does not come from a spoofed mailbox or an unknown address. Consequently it will bypass most email filtering systems. The threat actor uses a compromised account from one of your business partners.
The phishing email is typically fairly simple, as in it tries to trick the user into clicking on a link. The link typically directs the victim into a legitimate third-party website (Google Docs, Onedrive, Dropbox, etc). On this website the threat actor tricks the victim into clicking on a new link which leads to a malicious credential harvesting website.
Here is an example of a phishing email:
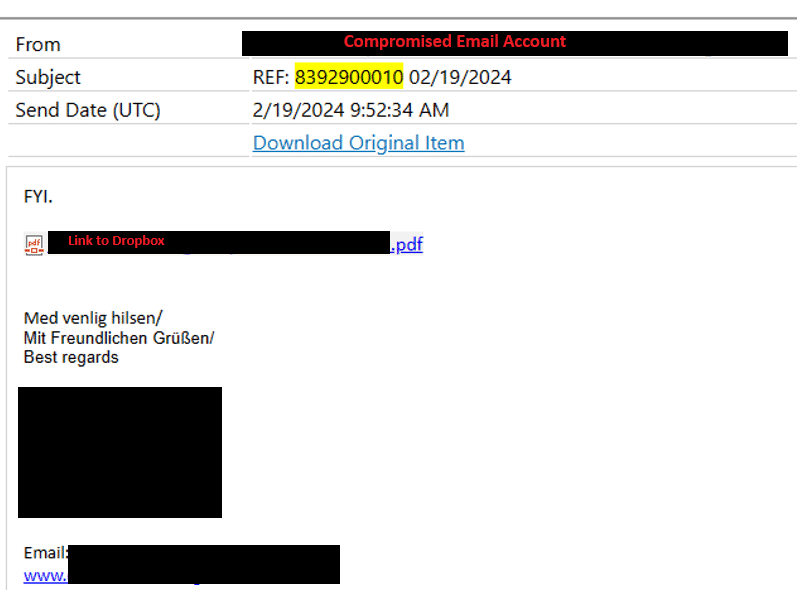
Below is an example of a page you get redirected to after a victim clicks the link.
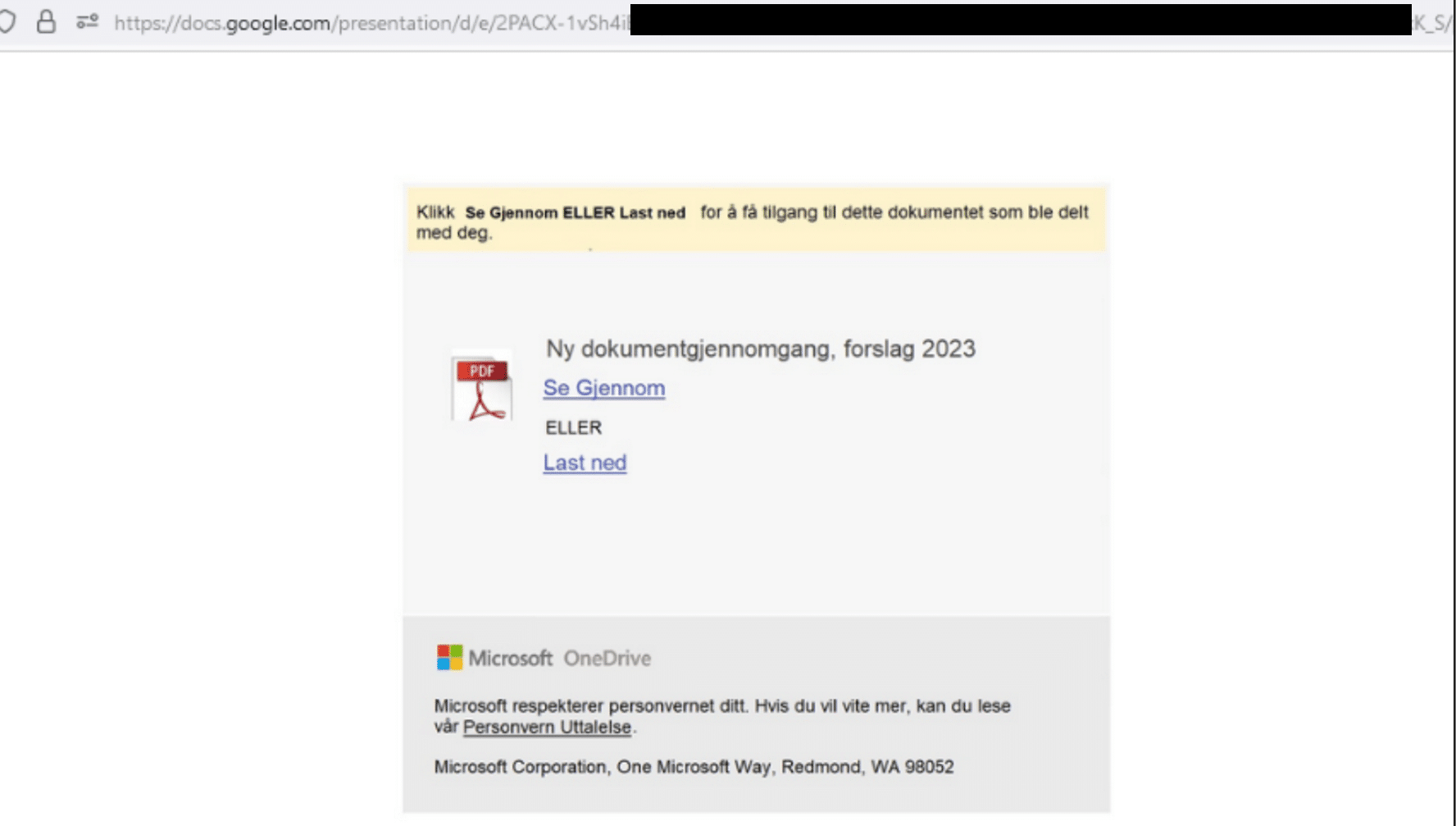
After the victim clicks on the link they get redirected to a faked Microsoft O365 Login page.
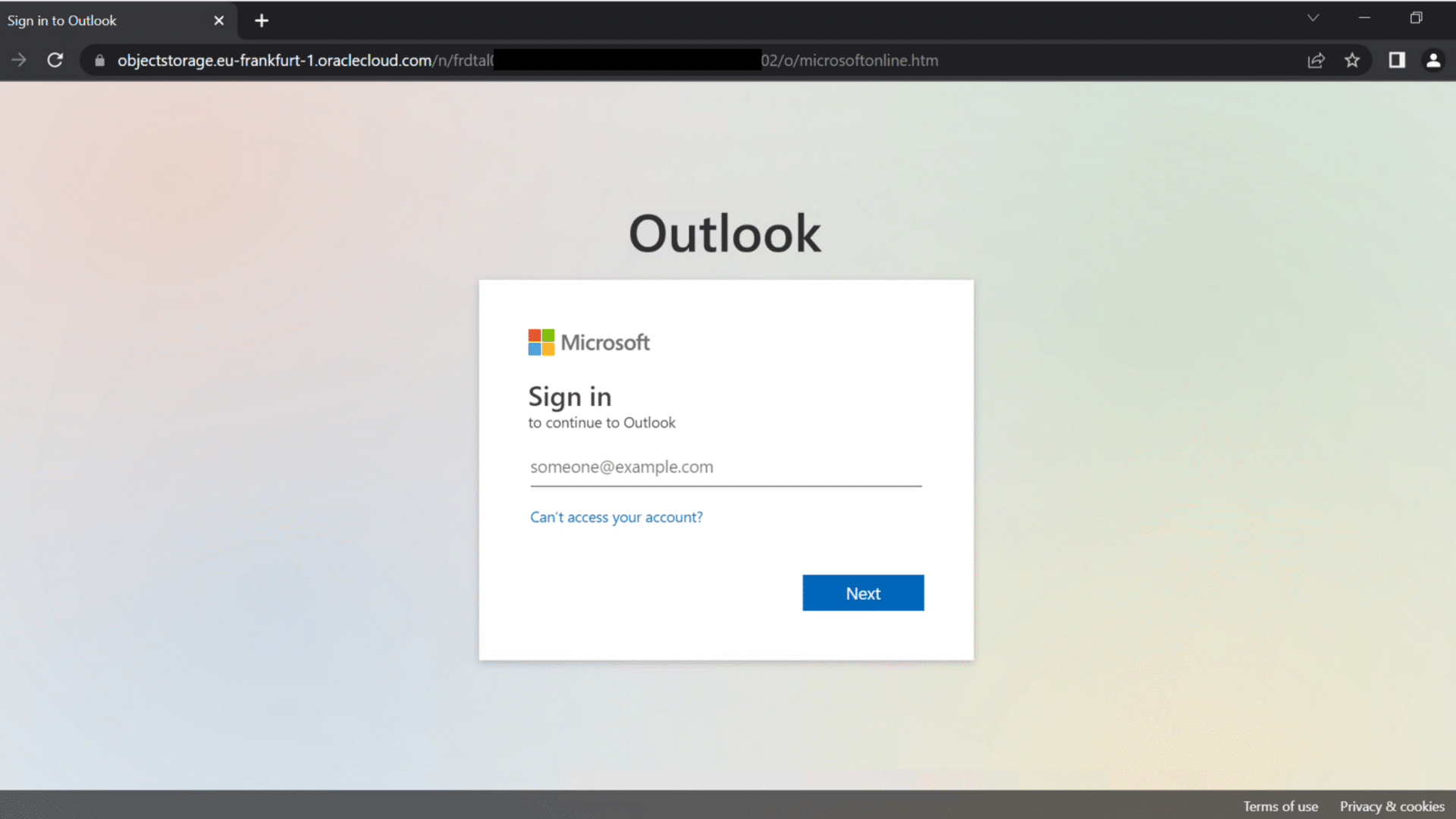
After the victim sign into the faked Microsoft website the threat actor is able to bypass multi-factor authentication. For more details on the how these attacks works on a technical level, there is a great Microsoft blog regarding Adversary in the middle attacks.
Detecting and mitigating a multi-stage AiTM phishing and BEC campaign | Microsoft Security Blog
Step 2 – Persistence
If the comrpomised account has multifactor authentication enabled, the threat actor can add an authentication method to the Office 365 account. This allows them to login even if the stolen session from the AiTM attack gets revoked.
Step 2 – Discovery
The threat actor now has full control of both the compromised mailbox and the Office 365 identity. The latter could allow the threat actor to access SharePoint or shared mailboxes. They use this access to access a large amount of emails related to invoices. They primarily search for large unpaid invoices.
Step 3 – Data Exfiltration
Once the threat actor has found an interesting invoice, they exfiltrate this. This can be done in many different ways. A few examples are:
- Email sent from compromised mailbox directly to threat actor.
- Syncing the mailbox with an email Client (e.g. Outlook).
- Direct file download from SharePoint.
- Using an Enterprise Application.
Step 4 – Crafting the payload
The threat actor then uses a PDF editor to change the bank details of the invoice. They ensure everything else inside the PDF is identical to what it was before. Consequently, they make the email look as legitimate as possible. This means that the reference number, the payment amount, etc. looks legitimate.
Step 5 – Inbox Rules
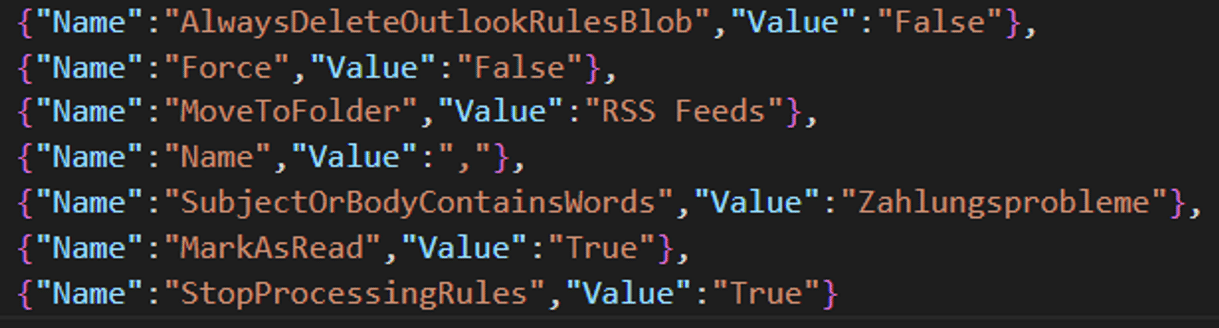
Before the threat actor send any email from a compromised mailbox they make sure that any replies to that email will only be visible for the threat actor and not to the real owner of the mailbox. The threat actors accomplish this using Inbox Rules inside exchange. Typically, they set up a rule that directs any in the incoming email to be marked as read and moved to the RSS feeds folder.
The UnifiedAuditLog in Microsoft Office 365 has an event called New-InboxRule. The screenshot below shows an example from this event, where the threat actor created a rule that matches any email containing the word “Zahlungsprobleme” (eng. Payment Problems) in the subject line.
Step 6 – CFO Scam or Credential Harvesting
If the threat actor successfully found an unpaid invoice they want to use in the attack they have several options to proceed with the fraud. The key takeaway in either of these options it that the threat actor always attempts to trick the victim into changing the bank details of the invoice. Sometimes it evolves spoofed emails and newly created domains. Sometimes it’s long email conversations where the threat actor tricks the victim into change the payment details of an upcoming payment.
This is the stage where Business Email Compromise turns into a CFO Scam.
It’s also important to note that the threat actors are smart here, they spend time inside the compromised domain. Sometimes we’ve seen the threat actor spend months having long conversations on a different language (using ChatGPT for translations). If they succeed, they typically try again with a new invoice.
OPTION 1 – Target the owner of the compromised email
If the threat actor finds unpaid invoices from a supplier in the compromised account they can choose to impose as the supplier. A fake domain is created with a domain name which resembles the real supplier’s. The fraudulent invoice is then sent from this newly created domain. In this scenario, all of the contents of the email (including previous parts of the conversation) is legitimate. However, the email address that the threat actor uses is different. So the approach is not optimal.
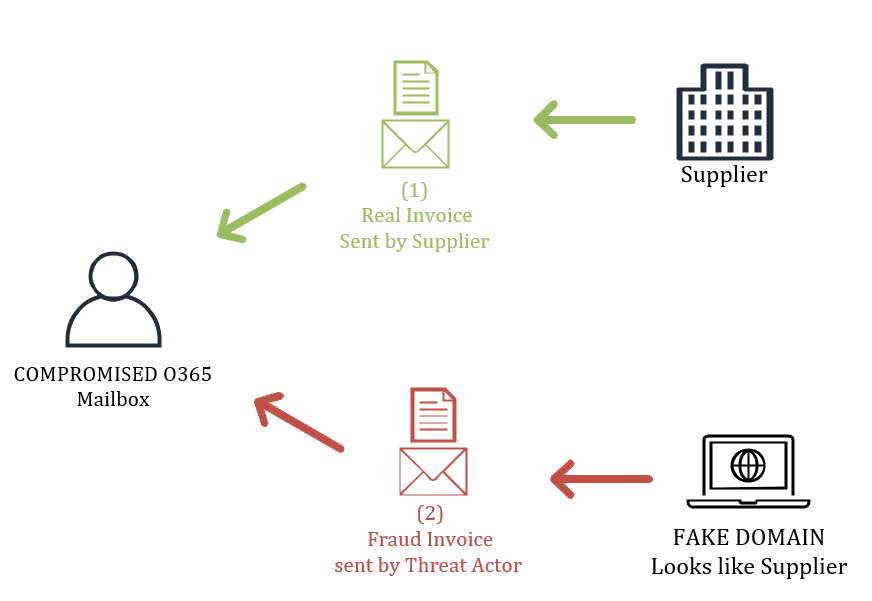
However, imagine if the threat actor also has compromised the supplier and has obtained enough privileges at the compromised O365 Mailbox to approve the fraudulent invoices…
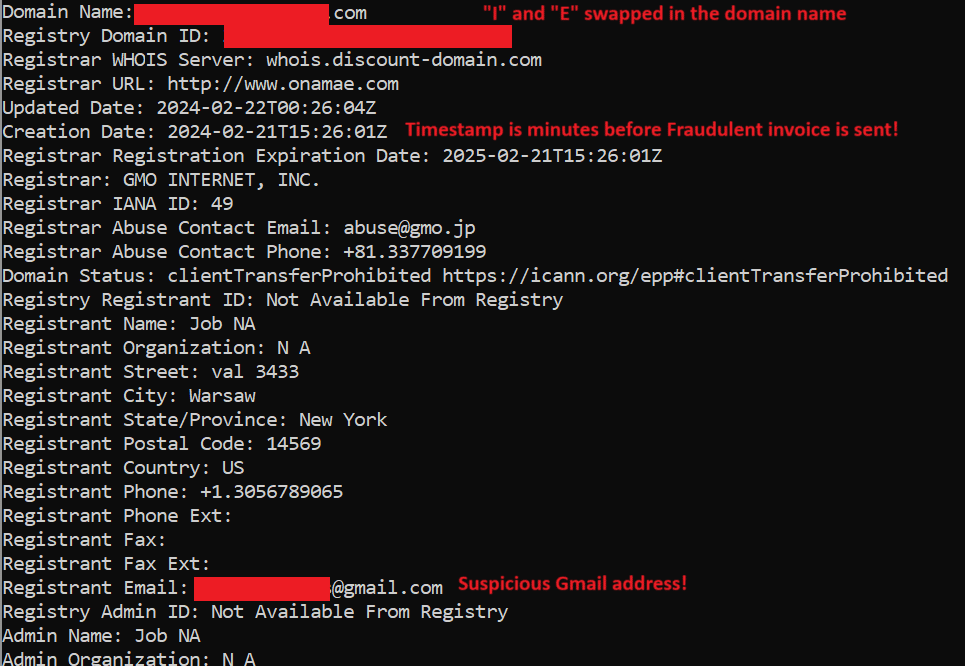
The screenshot below shows the WHOIS lookup for a fake domain used to send the fraudulent invoices to the victims of CFO scams. The domain name was identical to the supplier, however the threat actor swapped the characters “i” and “e” in the name. Additionally, the creation Date was set to minutes before the email was sent to the victim.
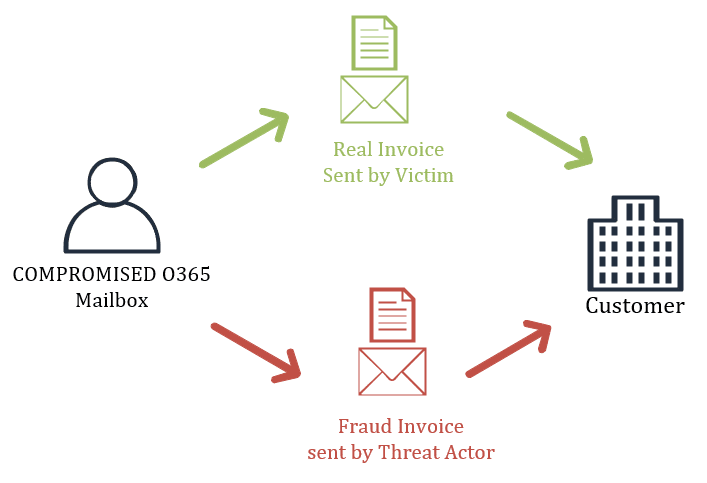
OPTION 2 – Target a customer of the victim
By targeting customers of the victim, the threat actor is able to send fraudulent invoices from a trusted source. Thus, making it very hard for the recipient of the fraudulent invoice to recognize that scam. The key takeaway in this scenario is that the threat actor still has to convince the customer to make the payment to a new bank account. During these types of attacks we often see the threat actor targeting multiple customers at the same time.
OPTION 3 – Credential Harvesting
It the threat actor fails to find an invoice they can manipulate they can default to a Credential harvesting attack. By sending phishing emails from the compromised account (See step 1).
How to protect your organization against Business Email Compromise (BEC) Attacks
- Implement a policy that requires a verification process during the changes of bank details of invoices.
- Implement Multifactor authentication – Although advanced phishing attacks can bypass this, it will drastically lower the risk of being a victim of Business Email Compromise.
- Perform a health check of the Office 365 environment.
- Monitor sign-ins to detect impossible travel and logons from suspicious IPs.
- Monitor the creation of Inbox-Rules.
At Truesec we offer security training in Microsoft Office 365, where you will learn how to protect and defend identities, devices, and data using the latest features in Microsoft 365.
