Threat actor attribution handbook
Using Kill Chain Analysis in Ransomware Attacks
This post illustrates how kill chain analysis can be used to parse forensic information from ransomware attacks and identify threat actors.

Introduction
The cyber kill chain is an adaptation of the military’s kill chain, which is a step-by-step approach that identifies and stops enemy activity. Originally developed by Lockheed Martin in 2011, the cyber kill chain outlines the various stages of several common cyber attacks.
There are many different ways to divide the steps in a cyber kill chain into steps. In this handbook we focus on four different phases, namely: Access, Persistence,
Discovery, and finally Impact. For each phase I determine what tool the threat actor used to conduct the activity.
The bulk of this handbook is a list of examples of real ransomware incidents with a list of tools used in each phase of the cyber kill chain. Then I examine how to interpret the data and how the cyber kill chain can be used to determine what actually happened in the incident, why it happened and how we in many cases can do attribution to more than one threat actor.
The Examples used are:
- LockBit Affiliate
- Conti
- Emotet and Ryuk
- Sangria Tempest and Ryuk
- Evil Corp and LockBit
- Evil Corp and Cl0p
- TA505 and Cl0p
Throughout the handbook I will primarily be using the name under which a group is most commonly known, but also the Microsoft MSTIC naming convention when applicable.
I hope that these examples taken together can help aspiring threat intelligence analysts understand the sometimes complex analysis involved in threat actor attribution.
Note that none of these examples should be viewed as final. Intelligence analysis is by it’s nature estimative and seldom definitive. I welcome any information that updates or disproves any part of this text.
Example 1 – LockBit Affiliate
This is a typical LockBit ransomware case. The tools used in the cyber kill chain are:
- Access: RDP
- Persistence:
Cobalt Strike - Discovery: Cobalt Strike
- Impact: LockBit ransomware
LockBit is a so-called ransomware-as-a-service syndicate. This means that the LockBit group only maintains the tools used in the ransomware attack. In ransomware-as-a-service schemes the ransomware gang is mostly a silent partner that usually gets around 20% of the ransom for renting the ransomware and other tools. The LockBit syndicate doesn’t get involved in individual attacks unless the independent affiliate needs support. In that case the ransomware group may keep up to 50% of the sum, depending on how much help the affiliate needs. The freelancing affiliate can be either a small team or just a single individual.
In many cases a forensic investigation of a LockBit attack shows that the initial access was a threat actor just logging in via RDP with valid credentials. While investigations seldom get much further due to insufficient logs, the most common reason LockBit affiliates can just log in with valid credentials is that another threat actor, a so-called Initial Access Broker (IAB), has previously managed to steal the credentials and then later sell it to the LockBit affiliate, unless the logs show that the threat actor managed to brute force the password. This could happened weeks or even months before the attack and can be difficult to trace forensically.
This is how the main parts of cyber kill chain should be interpreted:
- An Initial Access Broker (IAB) sends phishing mail that drops an information stealer that steals the victim’s credentials and offers them for sale on a darknet market.
- A LockBit affiliate buys the credentials and use them to login on the victim’s VPN.
- The LockBit affiliate to deploys Cobalt Strike for additional persistence, discovery and privilege escalation.
- The LockBit affiliate conducts data theft, destroys backups and deploys the LockBit ransomware.
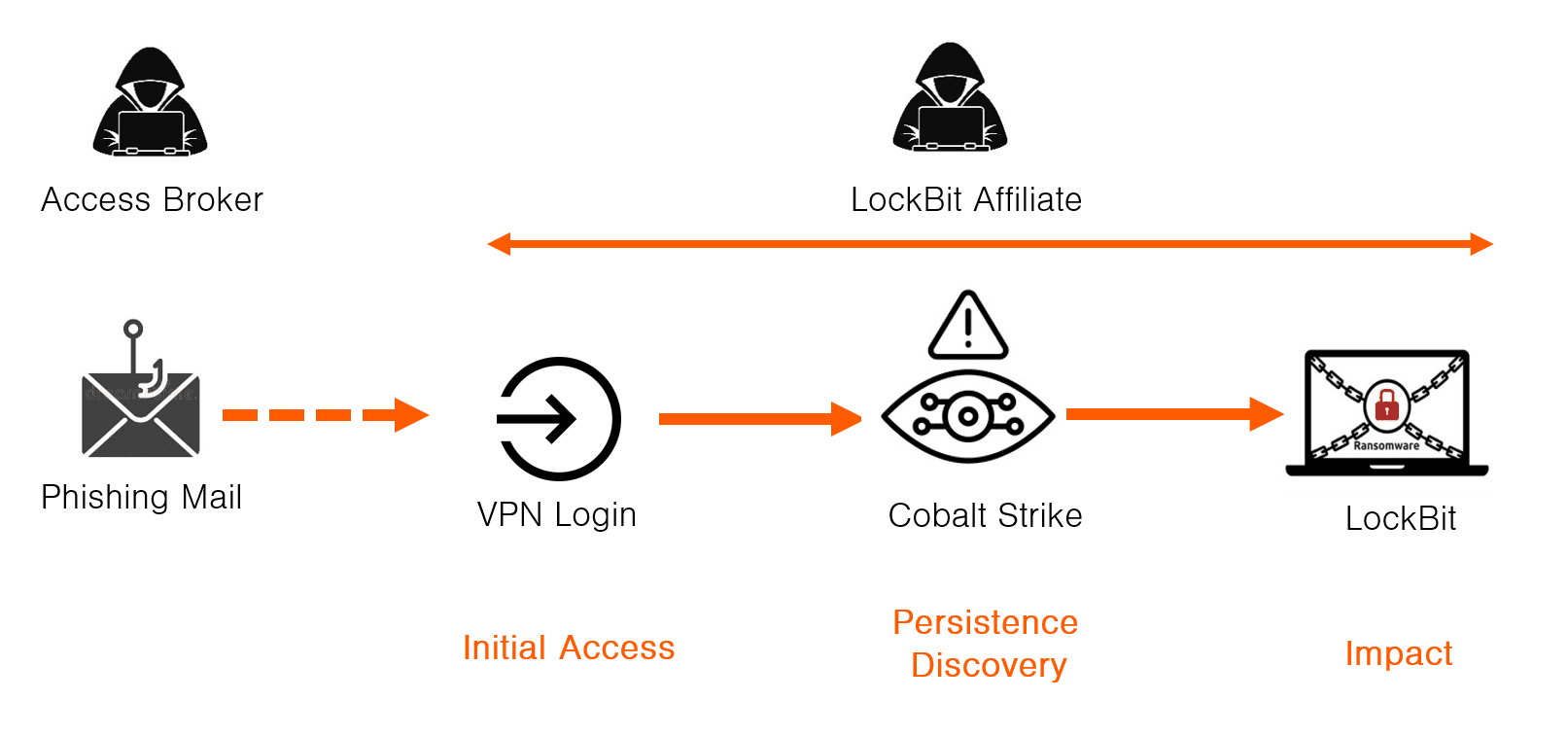
The use of Cobalt Strike is hard to tie to an individual group, as virtually every hacker uses Cobalt Strike today. However, the fact that the threat actor only deploys an openly available tool like Cobalt Strike for both persistence and discovery suggests it is either a lone hacker or possibly a very small team. Some affiliates may deploy commercially available Remote Access Trojans (RATs) for persistence, but most individual hackers seem to be satisfied with Cobalt Strike for persistence.
Example 2 – Conti Ransomware Attack
This is an example of one of series of attacks by the ransomware syndicate known as Pistachio Tempest or FIN12 in the fall of 2021, leading to Conti ransomware. The tools used in the cyber kill chain are:
- Access: ProxyLogon, Phishing mail
- Persistence:
QBot - Discovery: Cobalt Strike
- Impact: Conti ransomware
The business model and ransomware operations of this cybercrime syndicate are organized differently from typical Ransomware-as-a-Service operations, like the LockBit attack in Example 1. The first thing to notice is that the Conti attack used a custom RAT called QBot, or QakBot. The QBot RAT is not sold on the dark market. It is operated exclusively by the QBot team that were affiliated to the Pistachio Tempest (Ryuk/Conti) syndicate.
The fact that it is a custom RAT suggests that the group behind this part of the attack is a relatively large group that has the resources to develop their own custom tools. In 2021 the Pistachio Tempest syndicate’s operation had grown so large that they had incorporated two different teams each with a custom RAT on a semi-permanent basis, the QBot team and the IcedID team.
This is how the main parts of cyber kill chain should be interpreted:
- The Conti syndicate QBot team use the ProxyLogon exploit to take over a mail account.
- The Conti syndicate QBot team use the hijacked mail account to send a phishing mail that leads to QBot being deployed on other victims’ network.
- A Conti syndicate “pentester” working for the QBot team used his access to deploy Cobalt Strike for discovery and privilege escalation.
- One of Conti syndicate’s ransomware teams takes over, conducts data theft, destroys backups and deploys the Conti ransomware.
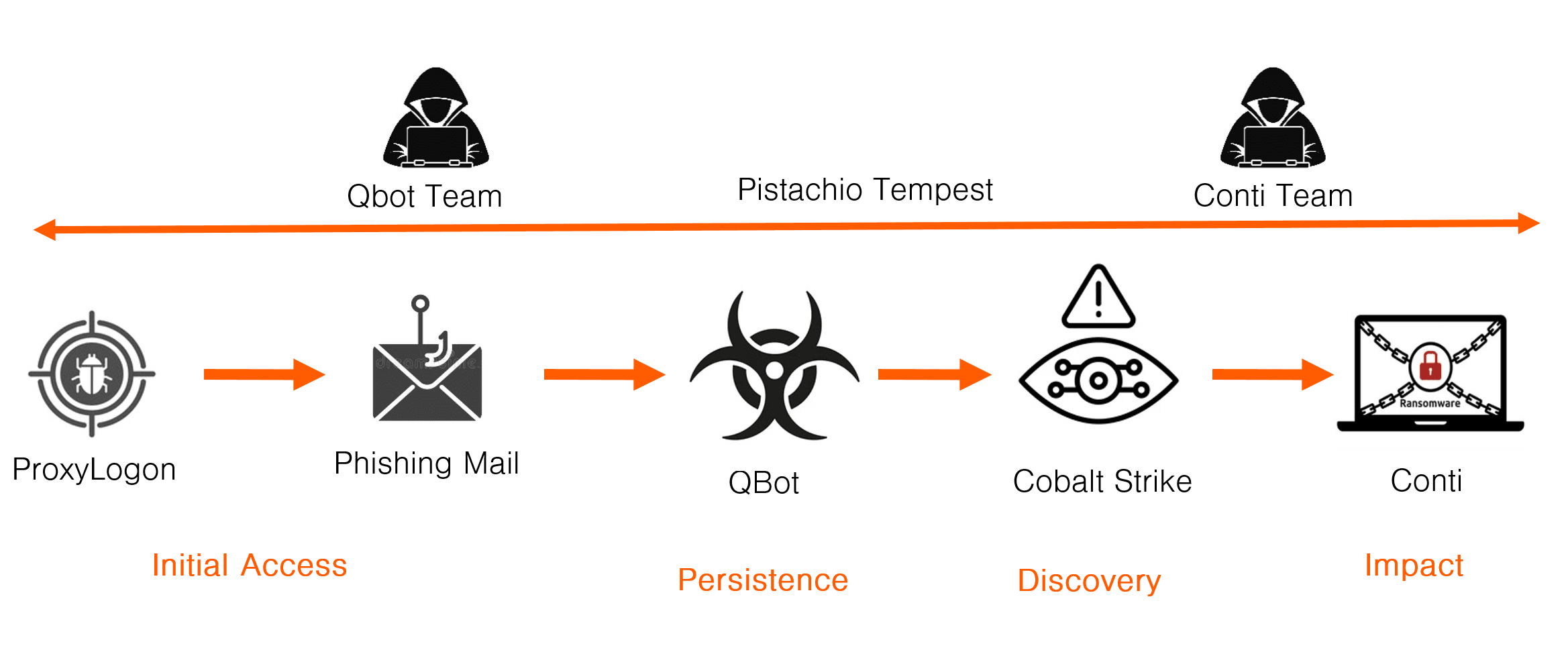
The multi-step method for initial access was probably used to increase the success chance of the phishing attacks, as the mail would come from legitimate email addresses, possibly pulled from the address book of the owner of compromised mailbox
By comparing this attack with others and see the same pattern: QBot-Cobalt Strike-Conti repeated many times, we can deduce that this is an organized operation where the Conti syndicate is an enterprise that employs many hackers who operate as organized teams, rather than affiliates to a Ransomware-as-a-Service gang.
By dividing the attacks into steps where a team of operators follow a standard Modus Operandi, almost like an assembly line, the Conti syndicate can hire lesser skilled, and cheaper, labor working for low salaries, rather than a percentage of the ransom amount, like affiliates of the ransomware-as-a-service gangs. This also makes the use of a custom RAT like QBot advantageous, as they can standardize attack patterns in manuals, and build a management interface where team leaders can supervise their employees in real time. Tracing whether a threat actor uses a custom RAT, a commercially available RAT or only Cobalt Strike for persistence can tell a lot about the threat actor.
Example 3 – Emotet and Ryuk
This example is based on an older incident. A typical Ryuk ransomware incident from 2019. The tools used in the cyber kill chain are:
- Access: Phishing mail
- Persistence:
Emotet, TrickBot - Discovery: Cobalt Strike
- Impact: Ryuk ransomware
This is very similar to the Conti attack above, but in this incident there were two different custom RATs used for persistence. Emotet, the first RAT used for persistence, belonged to the Emotet access broker. This is how the main parts of cyber kill chain should be interpreted:
- The IAB (Emotet group) sends phishing mail that infects the victims with the Emotet RAT.
- The IAB sells the access to Pistachio Tempest (Ryuk/Conti syndicate) and uses its own RAT Emotet as a loader to deploy the TrickBot RAT for additional persistence.
- Pistachio Tempest TrickBot team deployed Cobalt Strike for discovery and privilege escalation.
- The TrickBot team hands over to a Ryuk team that conducts data theft, destroys backups and deploys the Ryuk ransomware.
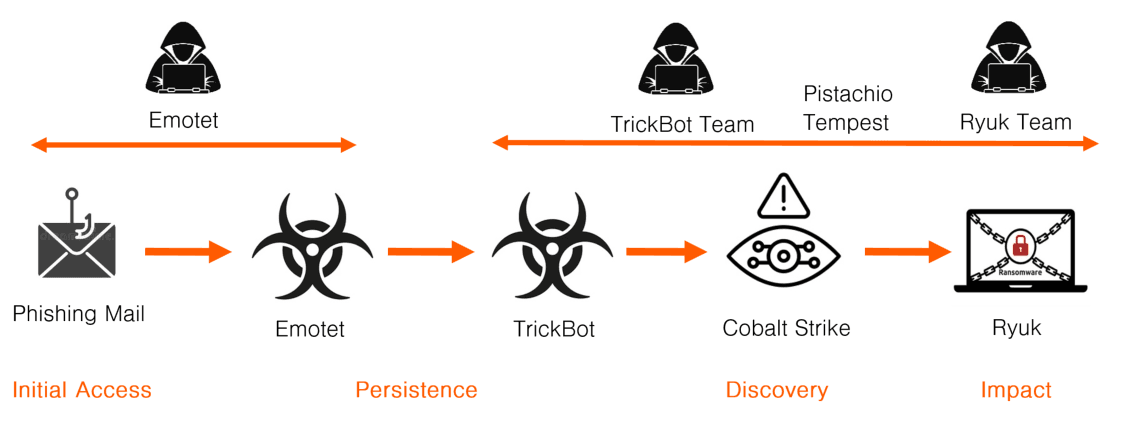
Like Qbot, TrickBot was almost exclusively used in attacks that led to Ryuk and later Conti ransomware, suggesting it is not a commercially available RAT, but a custom RAT used exclusively by one team. The ransomware Ryuk is tied to the same ransomware syndicate as Conti. The ransomware syndicate known as Pistachio Tempest or FIN12, first used Ryuk and then switched to Conti in 2021. This ransomware syndicate where closely affiliated to TrickBot and used them in the same way as they used QBot later. In fact TrickBot, QBot and IcedID appears to all have been part of the Pistachio Tempest syndicate at some point.
The Emotet group was an Initial Access Broker (IAB) that built a large botnet of infected machines and then sold access to other gangs like the Conti syndicate. Instead of stealing credentials they used the RAT, Emotet, they installed as a loader to deploy the ransomware syndicate’s own RAT, TrickBot. The reason they would do so was so each group can maintain control of their botnet, rather than share their internal management tools. When multiple custom RATs are used for persistence in attacks, it is usually an indication that multiple threat actors are involved.
Example 4 – Sangria Tempest and Ryuk
This is another case in which tools associated with two different threat actors are involved. The tools used in the cyber kill chain are:
- Access: Phishing mail
- Persistence:
PowerShell RAT, Carbanak - Discovery: Cobalt Strike
- Impact: BlackBasta ransomware
Sangria Tempest, also known as FIN7, is an old cybercrime group that specialized in POS hacks (hacking payment terminals to steal credit card information). In 2020 however Sangria Tempest begun to also breach networks and deploy ransomware. They apparently never developed their own ransomware but instead worked for other ransomware groups.
Both access and persistence and some discovery was done with tools associated with Sangria Tempest. They are also an established group with their own custom tools, like the TrickBot team, and once they had taken control of the entire network, they handed over to another threat actor that deployed Ryuk ransomware. This is how the main parts of the cyber kill chain should be interpreted:
- Sangria Tempest sends a phishing mail that leads to the deployment of a loader.
- The loader is used to deploy a PowerShell RAT, unique to Sangria Tempest, for persistence.
- Sangria Tempest use the access to deploy Cobalt Strike and conduct discovery until they have taken over the domain controllers.
- Sangria Tempest deploys Carbanak, another RAT unique to the team.
- The Ryuk team takes over, steals data, deletes backups, and deploys the Ryuk ransomware.
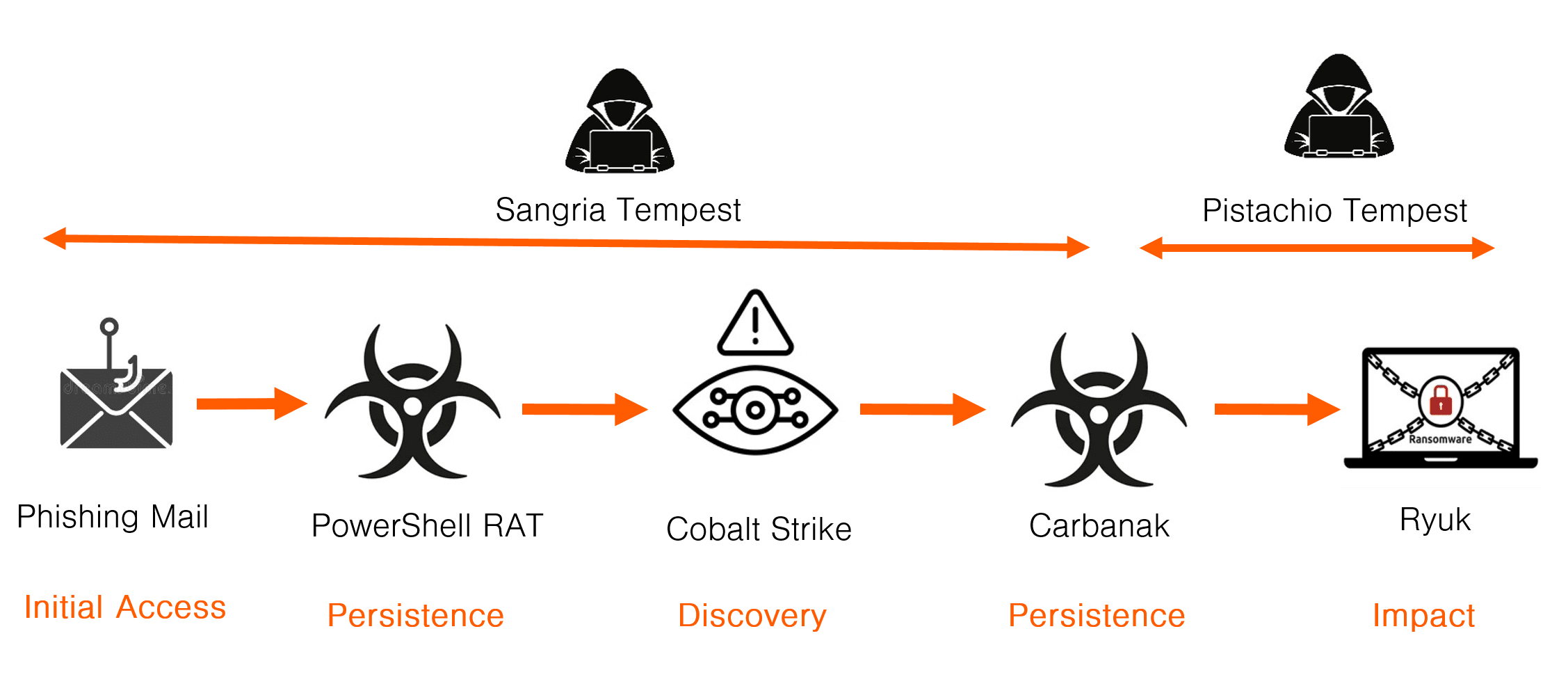
In this case there are also two custom RATs involved, both belonging to Sangria Tempest. The PowerShell RAT was deployed as initial access and Carbanak RAT was deployed after the threat actor had successfully conducted privilege escalation and taken over the domain controllers. So even if both RAT’s are tied to Sangria Tempest, the deployment of the second RAT appears to mark a handover phase from Sangria Tempest to the Ryuk team. Carbanak is an old RAT, and presumably Sangria Tempest didn’t worry about handing over control of it to the Ryuk Team.
As I mentioned before, the Ryuk/Conti syndicate doesn’t run ransomware-as-a-service operations. Their regular method is to partner in more-or-less permanent partnerships with groups like TrickBot and QBot, just as I explained in Example 2 and 3. The whole operation also follows a similar modus as the Conti operation in example 2. The main difference is that the TrickBot groups role is handled by an outsider, in this case Sangria Tempest.
Since then, a report from Mandiant claim that Sangria Tempest has also deployed DarkSide and ALPHV ransomware for the Black Cat ransomware-as-a-Service syndicate. Sangria Tempest is consequently an example of an organized team that can operate both with ransomware-as-a-service affiliates and with “enterprise” ransomware gangs like Conti and Black Basta. It is also worth noting that Sangria Tempest deployed both DarkSide and ALPHV when these ransomware strains were quite new. It’s possible that Black Cat hired Sangria Tempest for some high-profile attacks as they released a new ransomware, to create interest in their new ransomware. There is a lot of competition for affiliates in the ransomware-as-a-service market.
This incident was from 2020, but in 2022 a report from Sentinel Labs claims that Sangria Tempest was involved in a similar ransomware attack involving the Black Basta ransomware. Just like here, Sangria Tempest deployed their PowerShell RAT for persistence, took over the domain controllers and then deplyed additional persistence that they handed over to the Black Basta team. Black Basta is a rebranding of one of the teams behind Conti and, like Conti, they don’t run a ransomware-as-a-service operation. Their regular method is to partner with other parts of the Conti syndicate, like the QBot group.
It’s even possible that the people in the Black Basta team that cooperated with Sangria Tempest in 2022 were the same people who worked in the Ryuk team that had cooperated with Sangria Tempest in 2020. This suggests that it’s possible that Sangria Tempest cooperation both with Conti/Ryuk/Balck Basta and with Black Cat are based on personal relations between one or more key individuals in these groups.
Example 5 – Evil Corp and LockBit
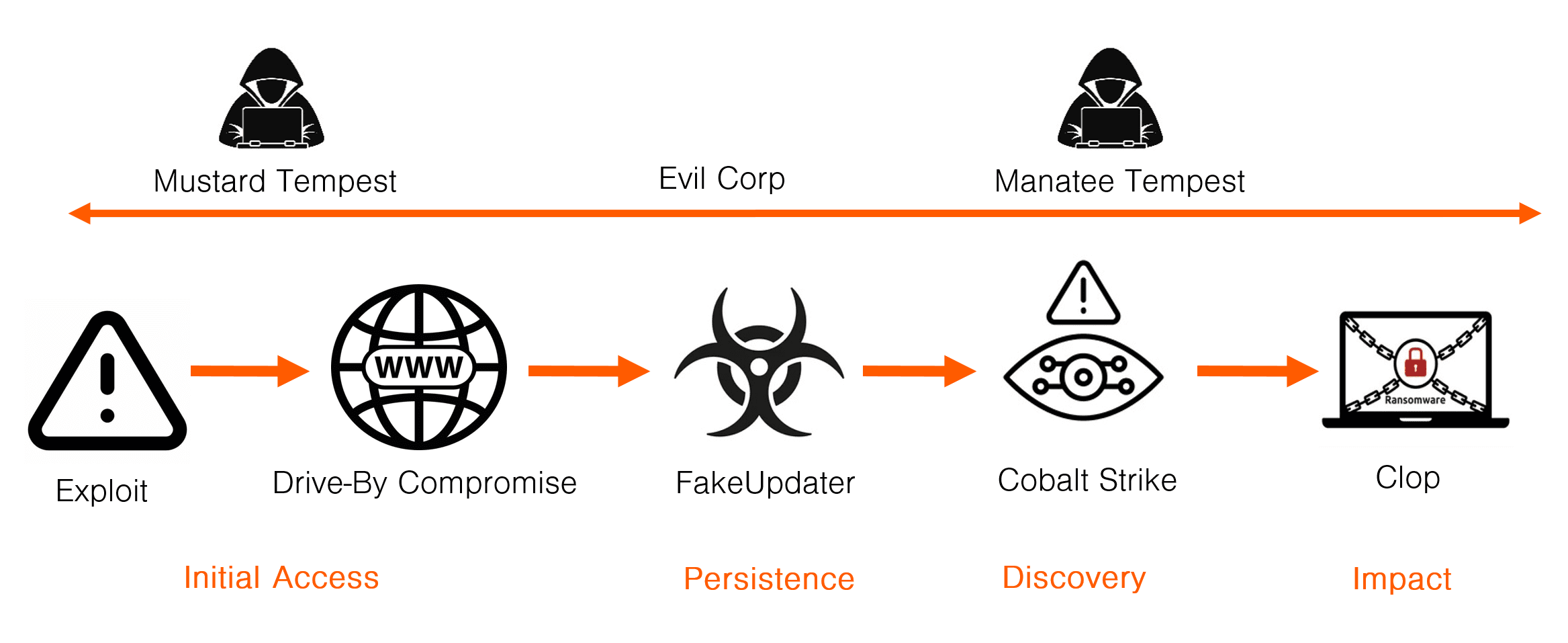
In this example we will look at a LockBit incident involving the infamous ransomware group known as “Evil Corp”. The tools used in the cyber kill chain are:
- Access: Compromised web page with SocGholish framework
- Persistence: FakeUpdater RAT
- Discovery: Cobalt Strike
- Impact: LockBit
Evil Corp is known to use innovative ways to gain initial access. Among other tools they use compromised web sites, so called drive-by-download, to deploy FakeUpdater RAT on potential victims. Mustard Tempest is the team that use FakeUpdater RAT and is likely a subgroup of Evil Corp, in the same way as TrickBot was a semi-permanent part of the Conti syndicate, while Manatee Tempest is the actual ransomware team of Evil Corp.
This is how the cyber kill chain in this incident should be interpreted:
- Mustard Tempest (Evil Corp) compromise a web page and installs the SocGholish framework.
- A victim is lured to visit the compromised web page and i prompted to download the FakeUpdater RAT for persistence.
- Manatee Tempest (Evil Corp) use FakeUpdater RAT for initial access and persistence.
- Manatee Tempest deploys Cobalt Strike for discovery and privilege escalation.
- Finally, Manatee Tempest deploys the LockBit 3.0 ransomware, likely paying the LockBit syndicate 15-20% of any ransom money.
To unpack this, we must first understand the nature of Evil Corp. Evil Corp has until recently been a ransomware gang that works on the same model as the Conti syndicate. They hired hackers that work as teams, rather than recruit affiliate freelancers to a ransomware-as-a-service operation. There is in fact some evidence suggesting that the Pistachio Tempest (Ryuk/Conti) syndicate originally started as an offshoot from Evil Corp, as the Ryuk/Conti syndicate initially used the Bugat/Dridex RAT, developed by Evil Corp. The leader of Evil Corp was identified in 2017 as Maksim Yakubets. He is indicted in the USA and FBI has a warrant for his arrest. This means that Evil Corp is under U.S. DOJ OFAC sanctions which makes it harder for them to collect ransoms, as paying ransom to sanctioned criminals is illegal in USA. In 2021 Evil Corp switched ransomware at least 4 or 5 times, but they were always quickly identified.
A report from TrendMicro indicates that a threat actor had begun to use the FakeUpdater RAT to deploy the LockBit ransomware from at least December 2021. This roughly coincides with the last known report of Evil Corp using their own ransomware. It appears that Evil Corp had simply tired of constantly being outed and decided to switch from their traditional business model to become a ransomware affiliate to LockBit. By hiding behind the infamous LockBit name, they could continue their ransomware activities and evade sanctions.
So in this incident the real threat actor is Evil Corp. LockBit is just the Silent partner, as in Example 1. The difference between Evil Corp and regular ransomware affiliates, is that Evil Corp is likely larger and far more organized and efficient than a regular affiliate. Evil Corp is also very innovative in obtaining initial access and doesn’t need the services of an IAB. In fact, the next example suggests Evil Corp may now be turning into a full time IAB themselves.
Example 6 – Evil Corp and CL0P
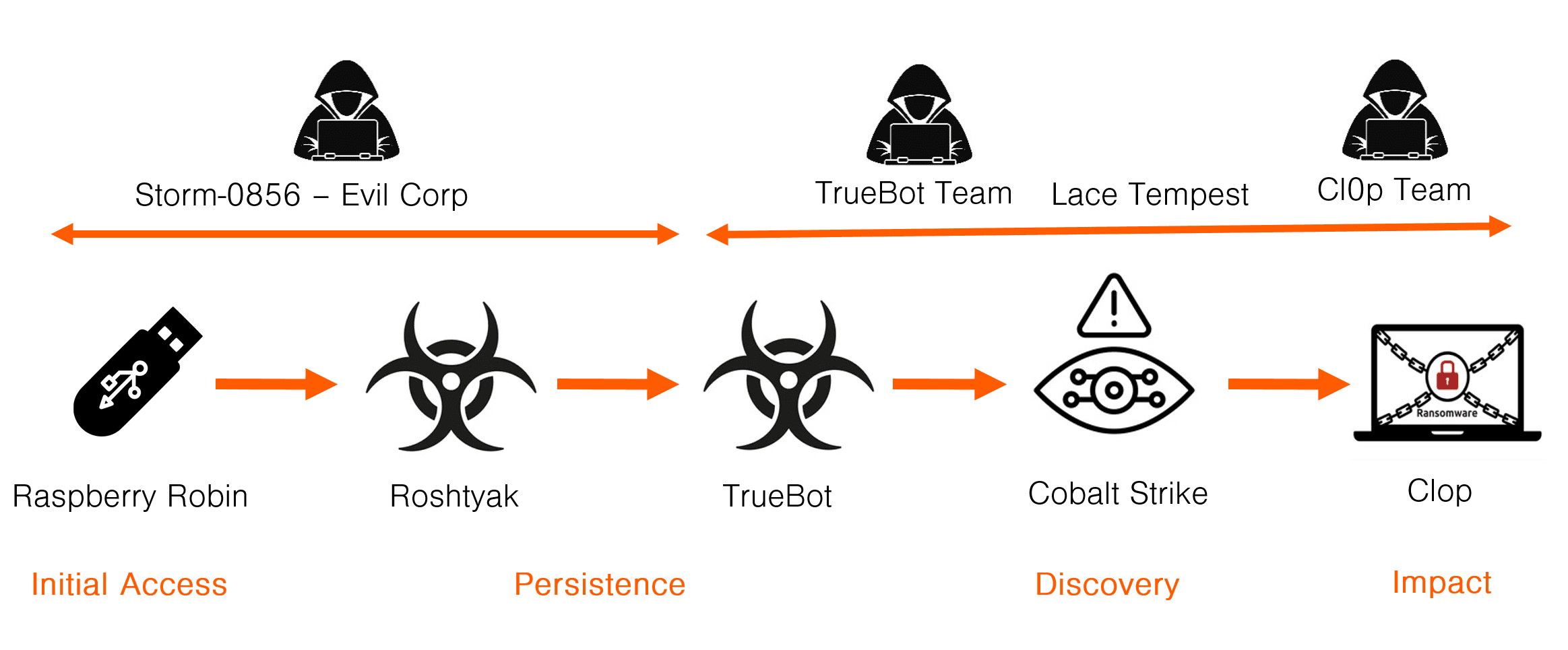
This is another incident where the novel USB worm Raspberry Robin leads to the deployment of the CL0P ransomware. The tools used in the cyber kill chain are:
- Access: USB drive infected with the with Raspberry Robin loader
- Persistence: Roshtyak, TrueBot RAT
- Discovery: Cobalt Strike
- Impact: CL0P
Raspberry Robin is a worm that spreads via USB drives. In an incident in 2022 a Raspberry Robin infection led to the deployment of the FakeUpdater RAT used by Evil Corp. A report by Microsoft describes how artefacts in Raspberry Robin suggests it is also related to the framework used to deploy FakeUpdater RAT from drive-by-downloads.
In the summer of 2022 it was reported that Raspberry Robin would lead to FakeUpdater RAT and then LockBit ransomware, just like with Evil Corp’s drive-by-download attacks in example 5. The threat actor behind Raspberry Robin, known as Storm-0856, is also likely a subgroup of Evil Corp. In this case Raspberry Robin led to Roshtyak, another custom RAT used by Storm-0856/Evil Corp. Roshtyak in turn loaded a second custom RAT, TrueBot, that is associated with the Lace Tempest ransomware group that use the CL0P ransomware.
Note that in this case Evil Corp has scaled down their part in the attack to just playing the part of an Initial Access Broker (IAB). When Raspberry Robin led to LockBit, it only loaded one RAT, FakeUpdater used by Evil Corp. When Raspberry Robin led to CL0P, it loaded two RATs Roshtyak and TrueBot, the latter belonging to Lace TEmpest (CL0P). Just like in example 3, the use of multiple custom RATs for persistence is an indication that there are two threat actors involved, where the owner of the first RAT is an access broker that uses it to deploy the second RAT, that is controlled by the access buyer. This is how the cyber kill chain should be interpreted:
- Storm-0856/Evil Corp spreads Raspberry Robin, and a victim gets their USB drive infected.
- The USB drive is entered to a corporate network and Raspberry Robin loads the Roshtyak RAT on the victim network for persistence.
- Storm-0856/Evil Corp use Roshtyak to deploy the CL0P group’s Truebot RAT for persistence. That way both groups control their respective malware.
- Lace Tempest deploys Cobalt Strike for discovery and privilege escalation.
- Finally, Lace Tempest deploys the CL0P ransomware.
The background here is likely that the novel attack vector used in Raspberry Robin created a lot of media attention to the fact that there where artefacts in the attack chain that tied it to Evil Corp. When the first reports of Raspberry Robin leading to LockBit attacks, it appears LockBit got cold feet and denied any involvement with Evil Corp. LockBit had cultivated their brand for years and probably was worried at being associated with Evil Corp and risk OFAC sanctions. Evil Corp likely decided to further scale back their visibility and simply become Initial Access Brokers (IAB) selling access to groups like CL0P instead.
Example 7 – TA505 and CL0P
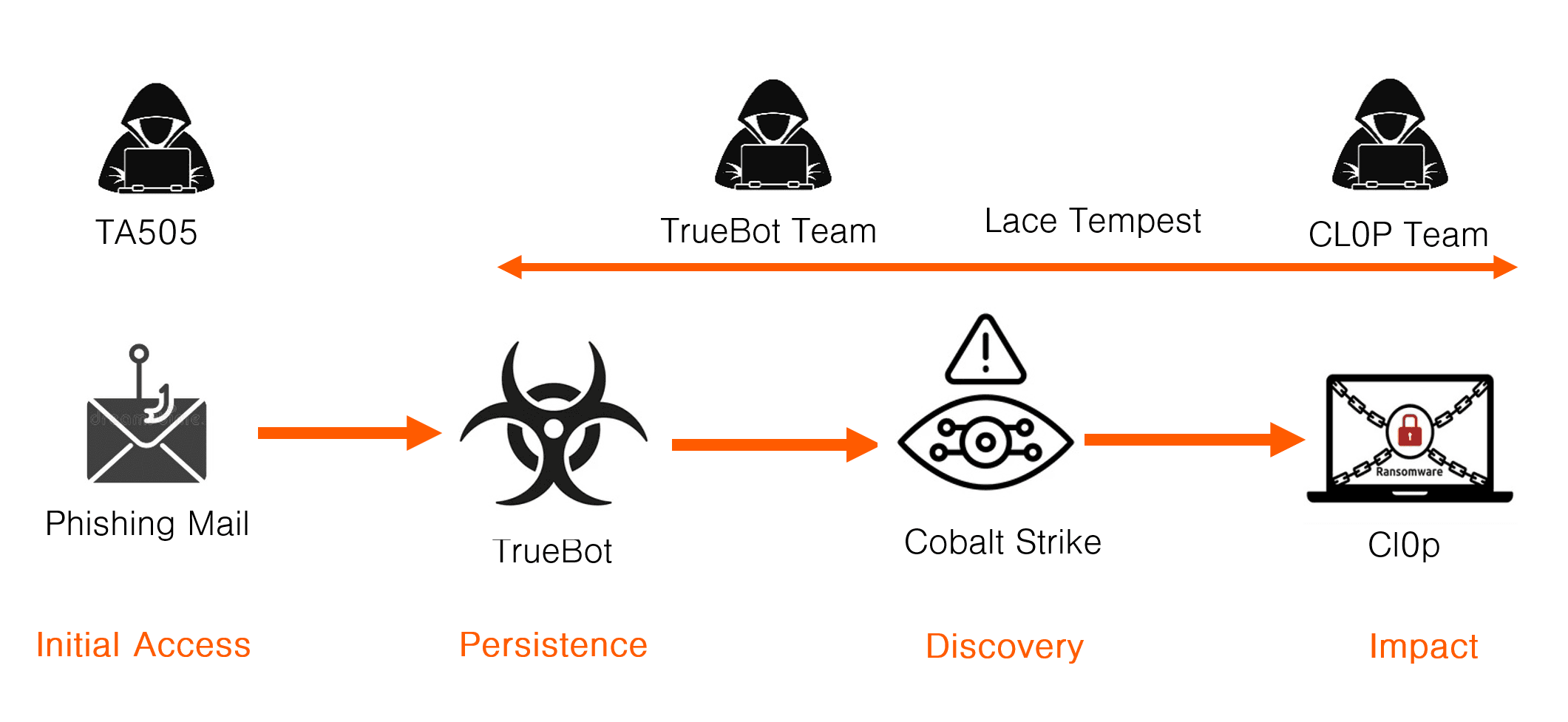
This is an incident where a spear phishing campaign leads to the CL0P ransomware. It represents the typical Modus Operandi for CL0P prior to their recent exploitation of the MOVEit vulnerability CVE-2023-34362. The tools used in the cyber kill chain are:
- Access: Phishing mail
- Persistence: TrueBot
- Discovery: Cobalt Strike
- Impact: Clop ransomware
First identified by Proofpoint, the threat actor TA505 have for long been associated with the Necurs and Neutrino botnets. TA505 has operated this botnet and rented it to send phishing mail for other threat actors. The Necurs botnet was taken down in March 2020 and it’s not known if TA505 have reconstituted the Necurs botnet since then or if they have replaced it with a new botnet, but they have apparently continued their operations.
TA505 doesn’t sell access to their botnet’s victims, like the IAB Emotet, instead they use their botnet, to distribute malware for other cybercrime groups via phishing mail. They essentially appear to be a phishing-as-a-service group. Instead of loading their customer’s RAT via their own RAT/bot, they their customer’s RAT into a phishing mail and send it from their bot. This is then the cyber kill chain:
- TA505 creates a botnet for their phishing-as-a-service.
- TA505 send a phishing mail that infects the victim with TrueBot.
- The TrueBot team of CL0P use the access to deploy Cobalt Strike for discovery and privilege escalation.
- The TrueBot team hands over to the CL0P ransomware team that conducts data theft, destroys backup and finally deploys the CL0P ransomware.
The fact that TA505 operates a phishing-as-a-service for other cybercrime groups has led to some confusion in attribution. For example, TA505 have been reported to deploy various ransomware. This is strictly speaking not true. TA505 sends phishing mail that may lure the recipient to download a RAT used by a ransomware group, but TA505 is not part of the ransomware attack, they just perform a service for the ransomware group.
Recently TA505 have reportedly partnered primarily with the CL0P ransomware group. This has led some analyst to assume that TA505 may even be part of the CL0P syndicate. While it is possible that TA505 may have entered into a semi-permanent partnership with the CL0P group, like the Emotet group did with Pistachio Tempest (Ryuk/Conti) I believe that it’s appropriate to treat them as separate threat actors, barring further evidence.
When a group like TA505 have been around for over 10 years and consistently used their botnet to deliver phishing mail or even spam for different threat actors over time, I believe it is clear that their main service to other cybercrime groups is to deliver phishing mail and that other cybercrime groups, like the Lace Tempest/CL0P syndicate, are their customers.
Annex – List of Common Tools in Ransomware Attacks
Below is a list of common tools used in ransomware attacks. The list is far from being exhaustive. This is just a sample of well known RATs and ransomware used in ransomware attacks. Knowing which type of malware being used can be a good indicator for what kind of threat actor is involved in an attack.
List of some common ransomware that are used in ransomware-as-a-service operations:
- LockBit
- Black Cat/AlphV
- Hive
- Black Byte
- Yanluowang
- Quilin
List of some common ransomware that are used by groups that don’t use ransomware-as-a-service:
- Black Basta
- Akira
- CL0P
- Cuba
- Ragnar Locker
- BianLian
List of some common ransomware where the source code is leaked so multiple threat actors can use them under different names:
- Conti
- Babuk
List of some commercially available RATs, that any threat actor can use:
- Agent Tesla
- Lokibot
- Async RAT
- njRAT
List Of some common RATs that are propretiary to a group that are the sole operator:
- TrickBot
- QBot
- IcedID
- TRueBot
- FakeUpdater
- Ursnif
- RomCom RAT
Stay ahead with cyber insights
Newsletter
Stay ahead in cybersecurity! Sign up for Truesec’s newsletter to receive the latest insights, expert tips, and industry news directly to your inbox. Join our community of professionals and stay informed about emerging threats, best practices, and exclusive updates from Truesec.
