Cloud-Powered MDR Deployment: Monitoring PaaS and SaaS Services Across Diverse IT Setups
Breach Monitoring on
PaaS and SaaS
TL;DR on monitoring PaaS
You’ve got MDR up and running, and you’re feeling secure, like a knight in shining armor. But here’s the catch: Your internally developed SaaS apps are more like dragons with a personality – no two are alike. And one thing needed is monitoring your PaaS services.
It’s unique, and so are its vulnerabilities and usage patterns. That’s where custom application alerting comes in. Custom alerting is like giving your security system a personalized GPS to navigate the twists and turns of your code. Without it, you might miss the subtle signs of trouble that only someone who knows your app inside out could spot. Don’t leave your defenses up to chance!
Also, please note that this page talks about how to do things with Microsoft technology. The same thinking works with other vendors. We just used Microsoft to explain our point (and not make this page even more complex with multiple vendors).
Introduction
In this article, we embark on an in-depth exploration of Managed Detection and Response (MDR) deployment. We will do that using three hypothetical yet realistically constructed organizations as our case studies.
These organizations, though entirely fictitious, are designed to closely mirror real-world IT environments and challenges. Each organization showcases different aspects and potential complexities in the implementation of MDR solutions.
Our discussion will not only focus on the technical sides of deploying MDR but also on understanding how these deployments can be tailored to meet the needs of different organizational structures and operational scales. Each of the three organizations has been created, drawing inspiration from actual case studies and industry experiences, to present a comprehensive and practical guide to MDR deployment. This approach allows us to address a wide array of scenarios, from small-scale setups to complex, multi-layered IT ecosystems. And provide valuable insights for a diverse range of IT professionals and organizations seeking to enhance their security posture with MDR.
Please note that the descriptions and solutions are illustrative; the explanations do not explain all the ins and outs of the company’s IT structures. These are created to describe a few different scenarios without going into all the details. Therefore, there are a lot of things in each company that are not explained.
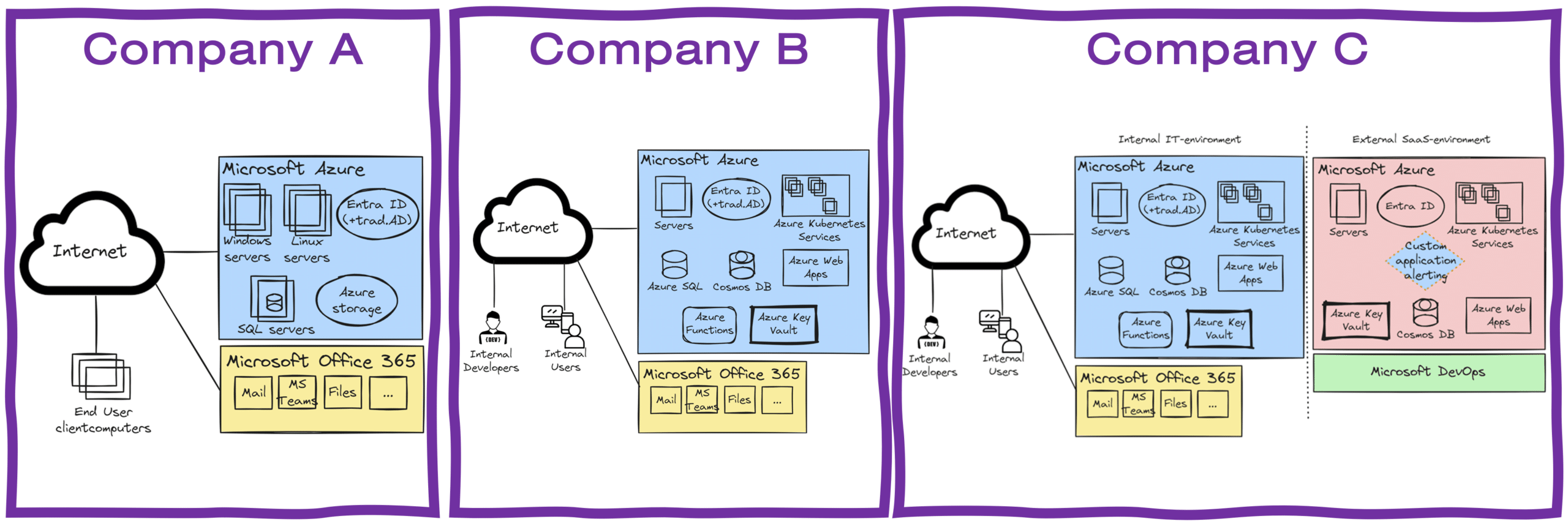
Short Descriptions of the Different Companies
| Company A | IT runs servers, applications, and databases in Azure, managed clients, and Microsoft 365. |
| Company B | Same as Company A, but also has internal development of one or more applications that are exclusively for internal use. These internal applications uses a variety of cloud services (Kubernetes, web apps, Cosmos DB and so on), and are a important part of the software stack and workflows within the company, creating a need to monitoring the PaaS services used. |
| Company C | Same as Company B, but the internal development also delivers a software solution that is delivered as a software-as-a-service (SaaS) to their customers. This software could, for example, be a platform for data analytics, an online ordering system, a customer relationship management (CRM), or other industry-specific solutions. |
Why so Focused on Microsoft here?
In this article, we’ve chosen to focus on Microsoft as the primary example for clarity and brevity. While there are many excellent providers out there, our aim is to simplify the discussion without delving into comparisons or rankings. This choice is not an endorsement of Microsoft over others; rather, it’s a way to provide a cohesive, understandable guide to Managed Detection and Response (MDR) within a familiar framework.
Company A – Traditional IT in a Microsoft Environment
Short Description (Low to medium need for monitoring PaaS)
Company A operates within a traditional IT framework, predominantly utilizing a range of Microsoft products. The core of their IT infrastructure revolves around Windows and Linux servers. In addition to this, Company A has integrated Microsoft 365 into its operational model. This integration is not just for leveraging the comprehensive suite of Office 365 applications. It is also for the licensing benefits Microsoft 365 offers to Windows clients, streamlining their software management process.
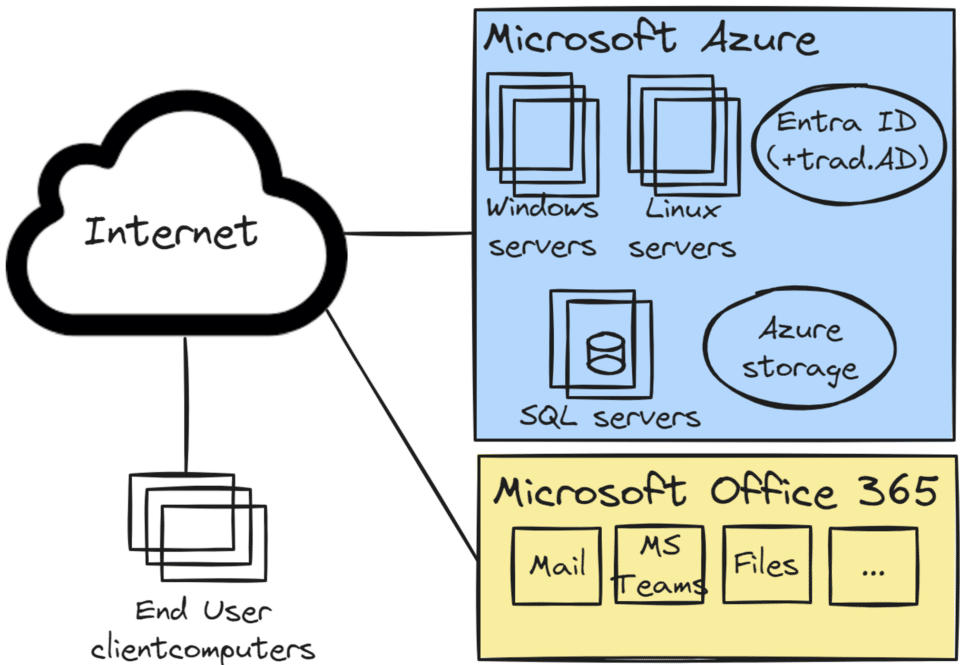
Given this alignment with Microsoft technologies, it was a strategic decision for Company A to select Microsoft Azure as their public cloud provider. This choice underscores a seamless compatibility with their existing Microsoft-centric ecosystem. They have moved all the servers to Microsoft Azure (a lift and shift migration).
The servers in Microsoft Azure run various applications and systems including Microsoft SQL server and other third-party off-the-shelf products.
How To Deploy Managed Detection and Response
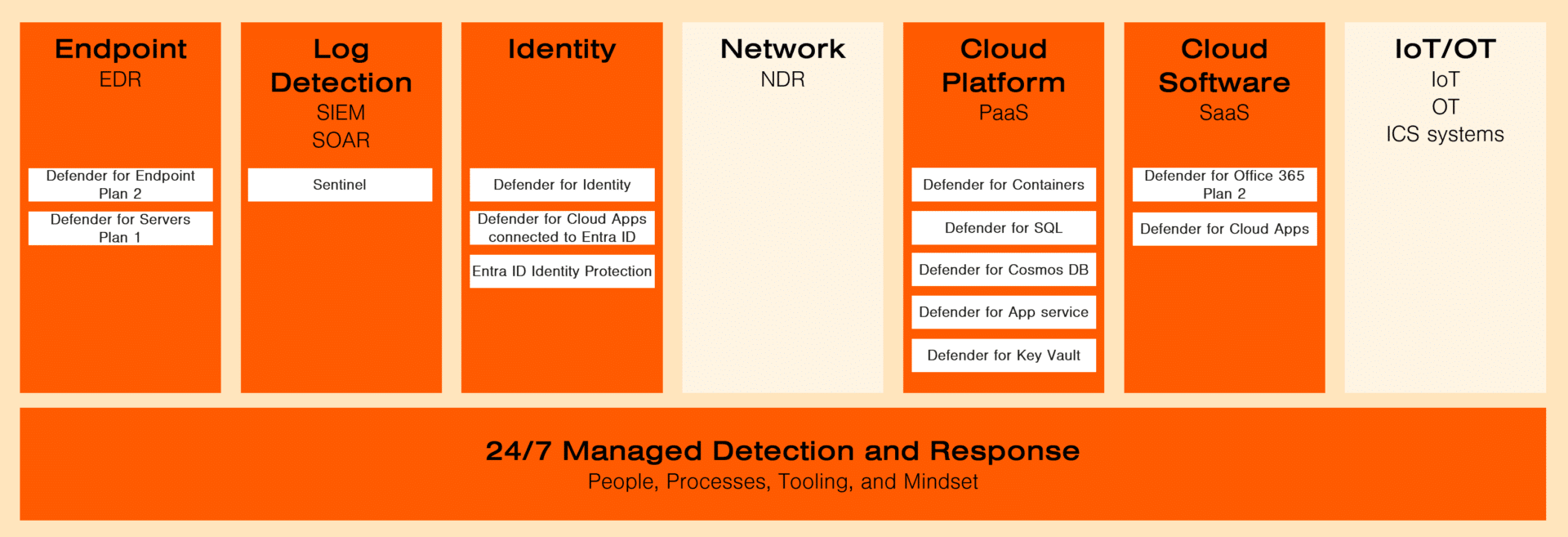
In the Truesec Managed Detection and Response service, we have one base module and seven additional modules.
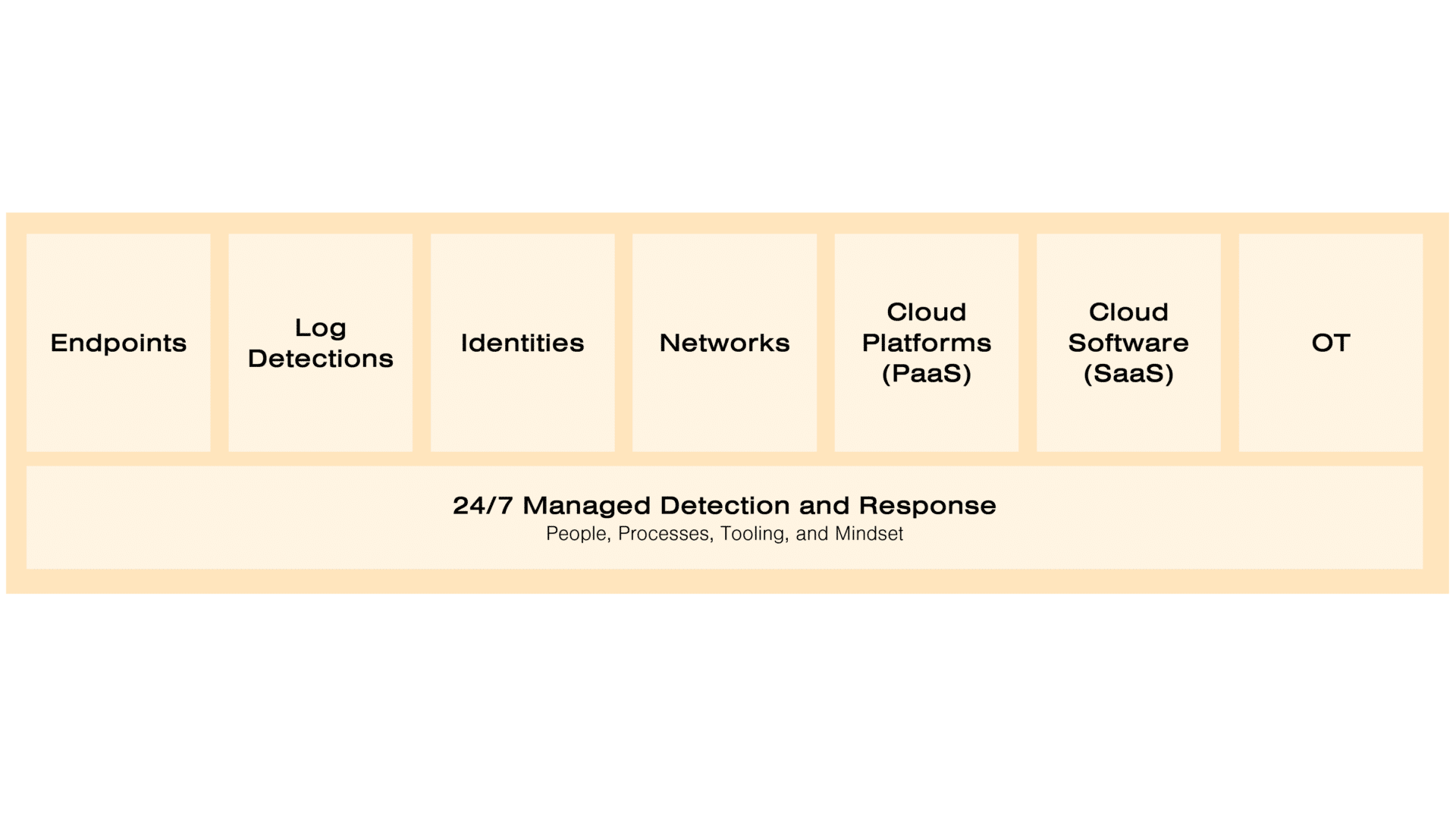
The “24/7 Managed Detection and Response” module provides all the people and processes for how to do MDR, Truesec custom tooling, and the assumed breach mindset of our SOC personnel.
Our recommended way to monitor Company A would then be based on existing licensing and investments. It would leverage the inherent strengths of their established Microsoft-centric ecosystem. This approach would involve integrating our MDR solutions with their current Azure infrastructure and Microsoft 365 suite, allowing for a seamless and efficient monitoring process. Additionally, we will customize our response strategies to align with Company A’s specific operational needs and threat landscape. This approach ensures a robust and proactive security posture.
Company A has invested in Microsoft 365 E3 licenses and added the Microsoft 365 E5 security add-on license to that.
This combination provides us with:
- Microsoft Defender for Endpoint (to monitor threats on end-user client computers).
- Microsoft Defender for Office 365 (to monitor threats in Office 365).
- Microsoft Defender for Cloud Apps (to monitor Office 365 and other SaaS applications).
- Microsoft Defender for Identity (to monitor identities in the traditional Active Directory).
- Entra ID, with ID protection (to monitor identity-based risks in Entra ID)
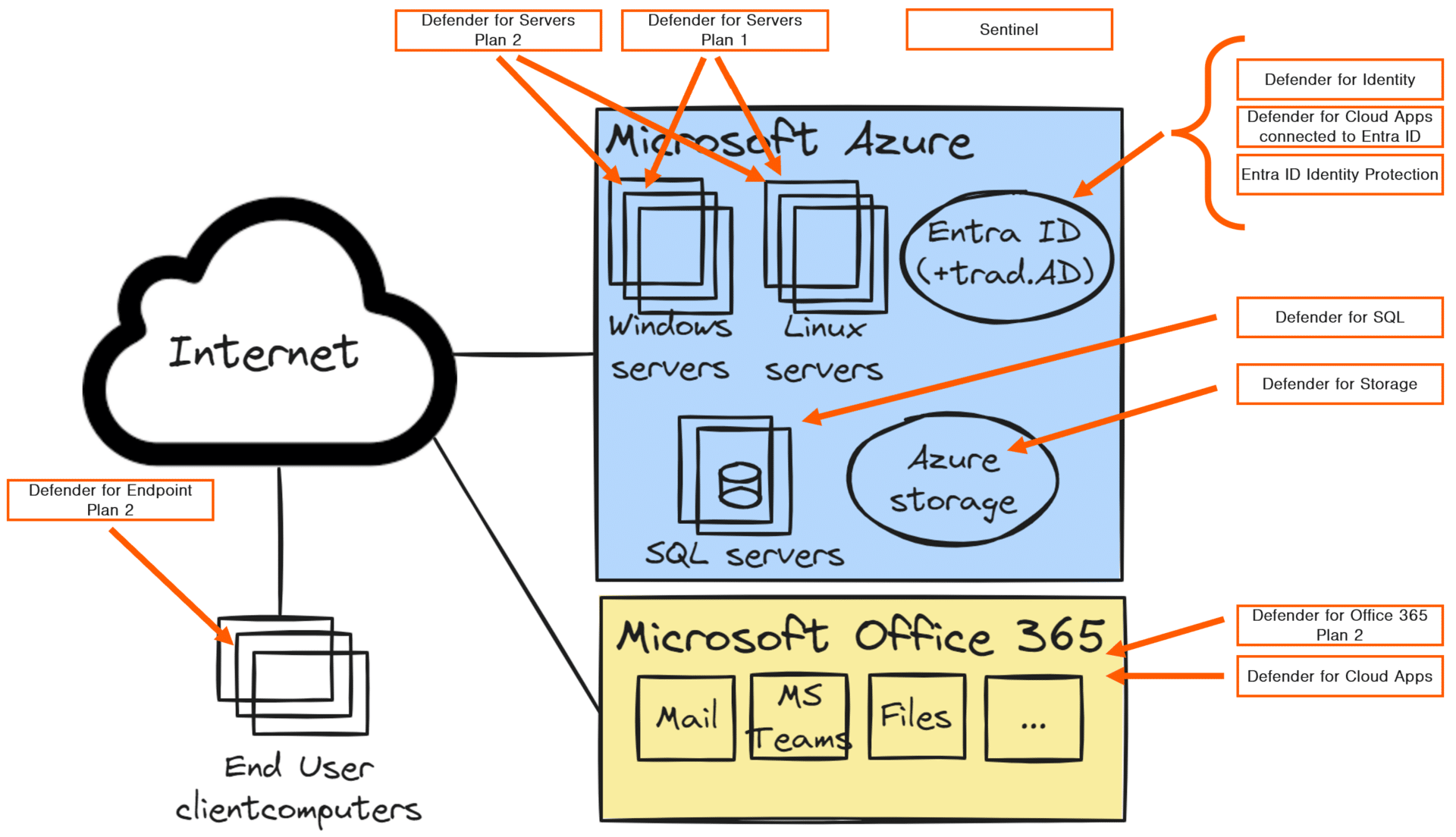
We collaborated closely with Company A to thoroughly review their IT environment. This evaluation identified potential attack vectors and pinpointed high-value targets within the infrastructure. Together, we have assessed that we use the SIEM functionality in Microsoft Sentinel for log detections and alert routing. Moreover, this strategy provides Company A with a strong platform to maintain compliance standards. It also enables adherence to regulatory requirements and enhances overall security governance.
During the review, we also identified that Company A uses a third-party application that is business critical. This application is installed on a few application servers. All of Company A’s servers will be monitored with Microsoft Defender for Server. Also, for the business-critical servers, we have decided to upgrade to the Plan 2 license. This also provides the operations team access to the Qualys vulnerability scanner. The database server will also be monitored by Microsoft Defender for SQL to provide an extra protection and detection layer. This includes suspicious data activities, potentially harmful access attempts, SQL injection attacks, anomalous database access, and query patterns.
Conclusion
Company A is set to receive an extensive detection capability that covers its entire IT infrastructure. This includes the six key MDR modules, each paired with corresponding Microsoft products.
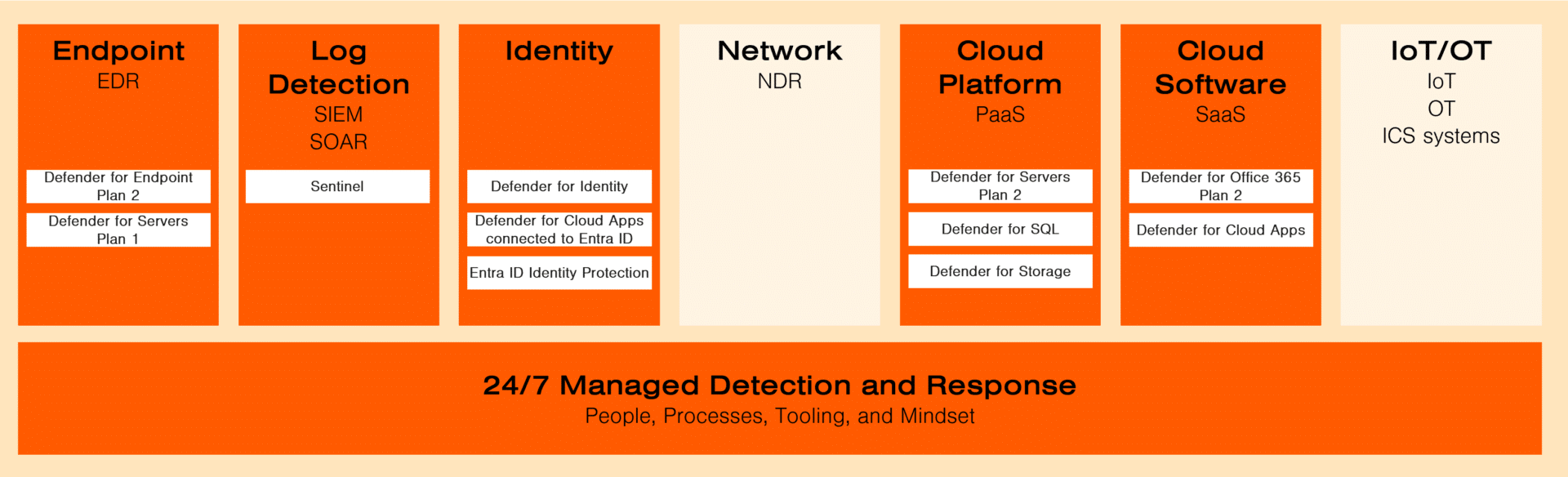
These tools will significantly bolster the detection capabilities of Company A’s IT operations team.
They will also be equipped to enhance their preventive measures, starting with vulnerability detection. Relevant resources for understanding vulnerability detection include articles and tools found at CSO Online, OWASP, and Truesec Vulnerability Management Service or Vulnerability Management – From Detection to Mitigation page. Next, the operations team at Company A can begin working with cloud security posture management (CPSM) as an added capability. A more in-depth exploration of this functionality is available here.
This will establish a multi-layered security framework that addresses immediate threats. It also proactively identifies and mitigates potential vulnerabilities before they can be exploited. This comprehensive approach safeguards Company A’s digital assets against evolving cyber threats. Finally, it also aligns with industry best practices and regulatory requirements
Company B – Hybrid IT with Cloud Integrations
Short Description (Medium to high need to monitoring PaaS)
Company B is an organization that is blending traditional IT practices with advanced cloud-based solutions. They have a team of internal developers dedicated to creating specialized integrations and applications for internal use. This highlights their commitment to tailored technological advancements. Initially, these applications were deployed on traditional servers, providing a reliable and time-tested base for their IT operations.
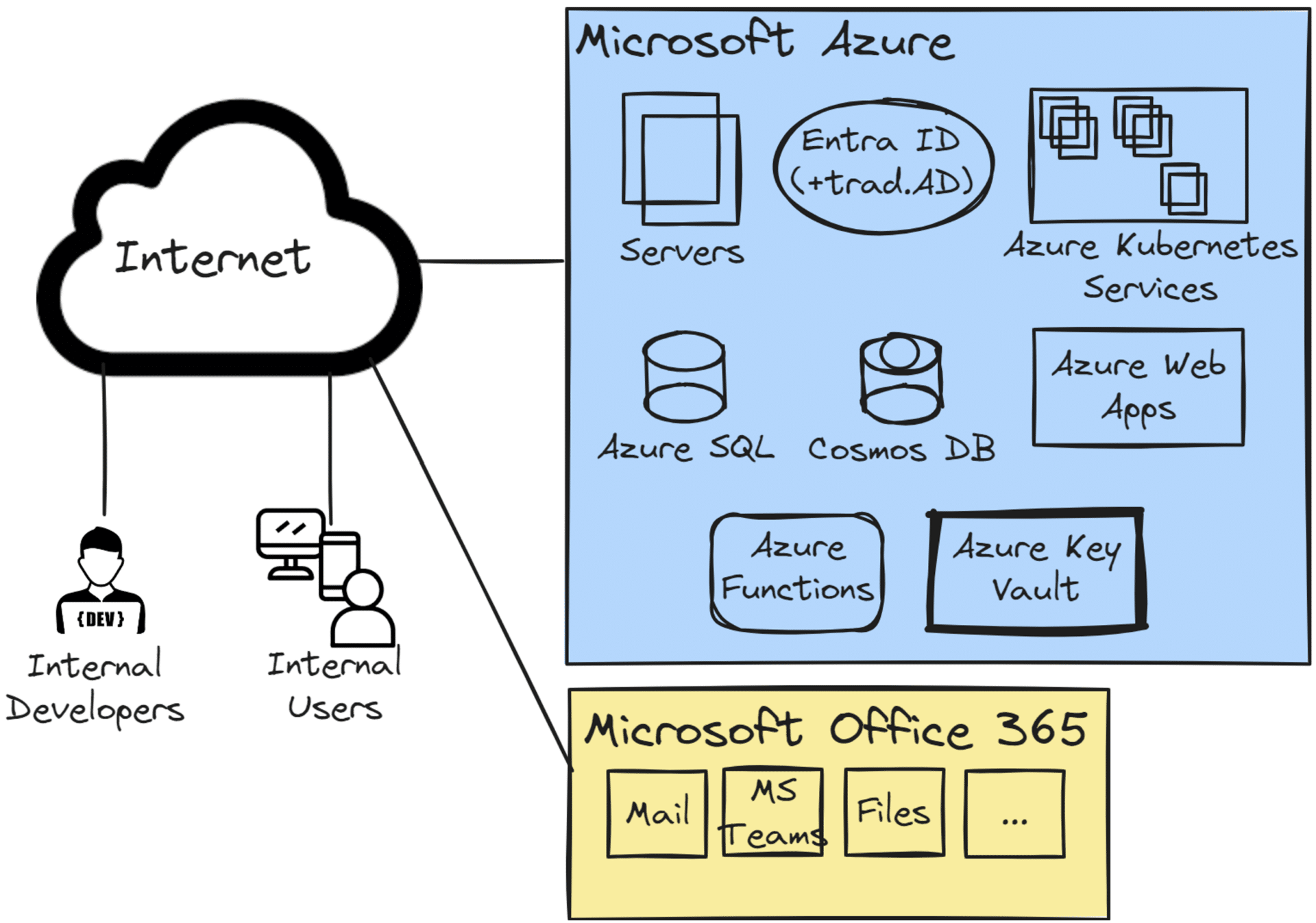
In its journey towards a more agile and scalable IT infrastructure, Company B has increasingly integrated Microsoft Azure’s platform-as-a-service (PaaS) offerings, and therefore have a higher need for monitoring PaaS services for breaches than Company A. This integration includes Azure App Service for hosting internal web applications, Azure SQL Database for advanced and scalable database management, and Azure Functions for streamlined serverless computing to automate internal operations and system integrations. Additionally, they utilize Azure Key Vault for secure management of keys, tokens, and secrets, Azure Kubernetes Service (AKS) for efficient container orchestration, enhancing their application development and deployment processes, and Cosmos DB for globally distributed, multi-model database services, ensuring high availability and performance for their diverse data needs.
The strategic adoption of Azure PaaS services optimizes Company B’s deployment methodologies. It also ensures seamless integration with their current infrastructure. This approach reflects Company B’s commitment to staying ahead in technology. In essence, it equips its internal operations with the latest tools to improve efficiency and adaptability in a rapidly evolving digital environment.
How To Deploy Managed Detection and Response
We’ll focus on implementing detection and response for the parts of the environment used by the internal development team (in other words, the things that differ from Company A). Like Company A, Company B will use endpoint detection for servers and client computers.
As before, we will use the “24/7 Managed Detection and Response” module to provide everyone with the processes on how to do MDR, Truesec custom tooling, and the assume breach mindset of our SOC personnel.

After evaluating Company B’s blend of traditional and cloud-based IT, we’re aligned with their needs. Microsoft Defender for Cloud would greatly enhance their security monitoring and their capability to securing the PaaS services. Especially since it is aligned with their existing Azure infrastructure.
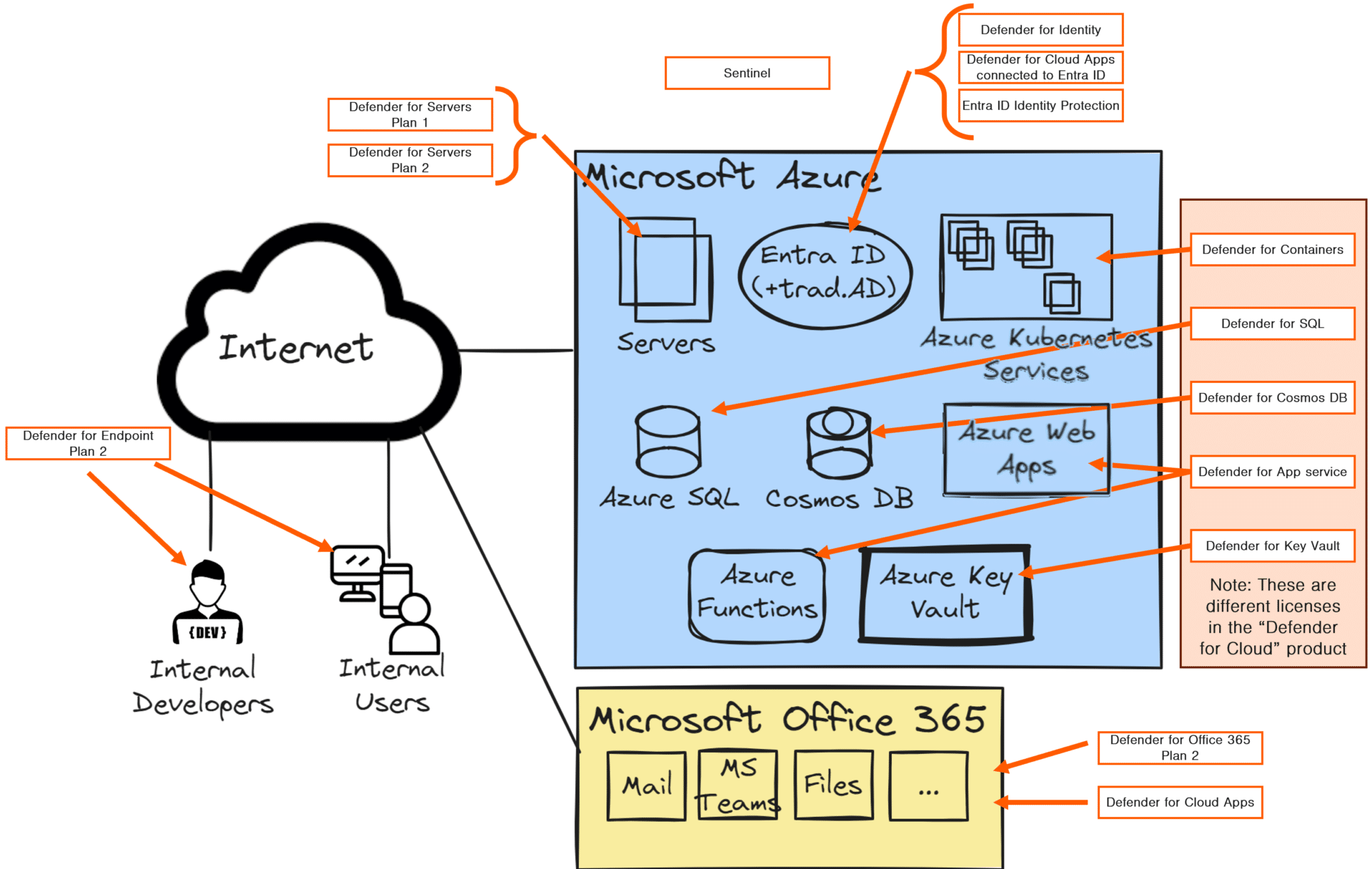
Servers, endpoints, Microsoft 365, and identities will be monitored in the same way as for Company A (Defender for Servers, Defender for Endpoints, Defender for Office 365, and Defender for Identity + Entra ID identity protection (Part of Entra ID Plan 2 license). In this case, Microsoft Sentinel will also be used for log detections and alert routing.
Then, to monitor the PaaS services, the Defender for Cloud Suite will be used. There are numerous different licenses depending on what PaaS services are used. But in this particular case, the applicable ones are Defender for Containers, Defender for Databases, Defender for App service, and Defender for Key Vault.
Conclusion – How to secure and monitor the entire Company B, including PaaS services
From the perspective of the Managed Detection and Response service delivered by Truesec, the delivery for Company B is very similar to the one for Company A.
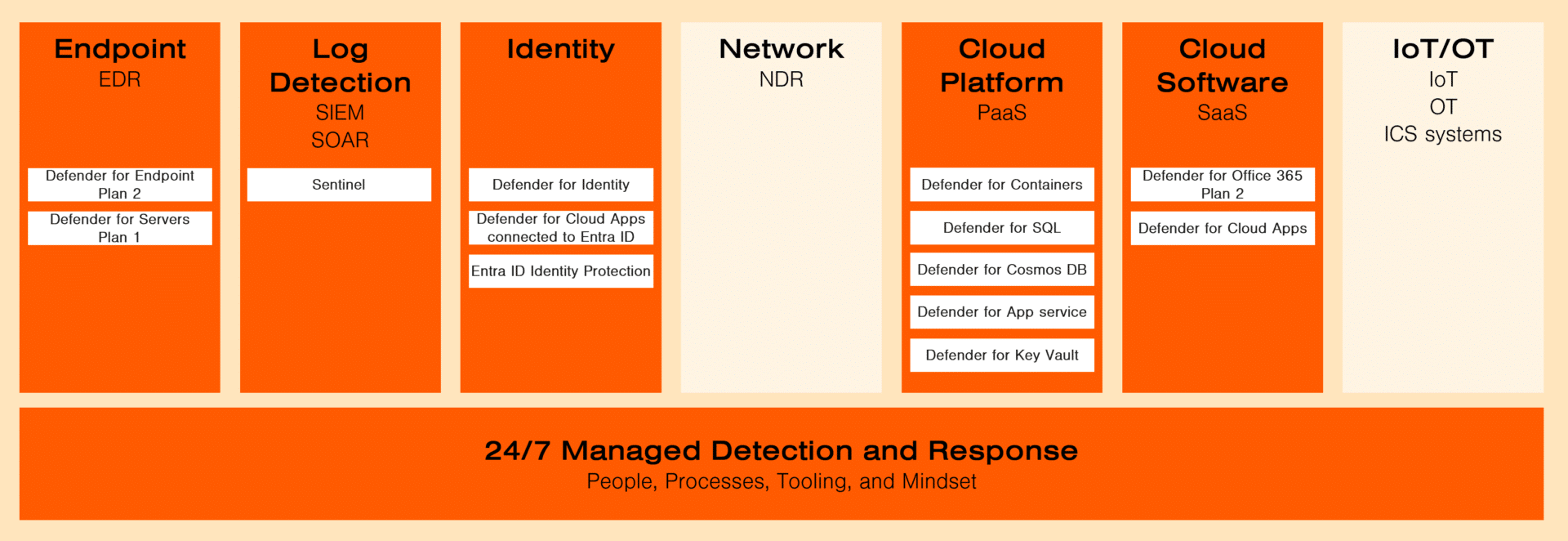
We use the same modules in the service (Endpoint, Log Detection, Identity, Cloud Platform, Cloud Software, and 24/7 Managed Detection and Response).
The difference here is that there are more components that are monitored under the Cloud Platform.
Notably, when deploying/activating the different parts of Defender for Cloud, not all resources in all PaaS services are equal. It’s usually beneficial to classify different resources based on the type of information they contain. Additionally, consider the business impact of each component.
This approach ensures that important areas are properly monitored. Lastly, it also helps allocate resources like time and money correctly.
Company C – SaaS Provider with Advanced Security Needs
Short Description (High to very high need for monitoring PaaS)
Just as in previous example, in Company C there are internal developers who are creating integrations and applications for the internal organization. But the big difference is that they also creates a software solution that delivered as a Software-as-a-Service (SaaS) to their customers. This software could for example be a platform for data analytics, customer relationship management (CRM), or other industry-specific solutions. This SaaS offering is hosted in a multi-tenant environment within Azure, leveraging advanced cloud services such as Kubernetes for container orchestration, Azure DevOps for continuous integration and deployment (CI/CD), and Cosmos DB for scalable, distributed databases.
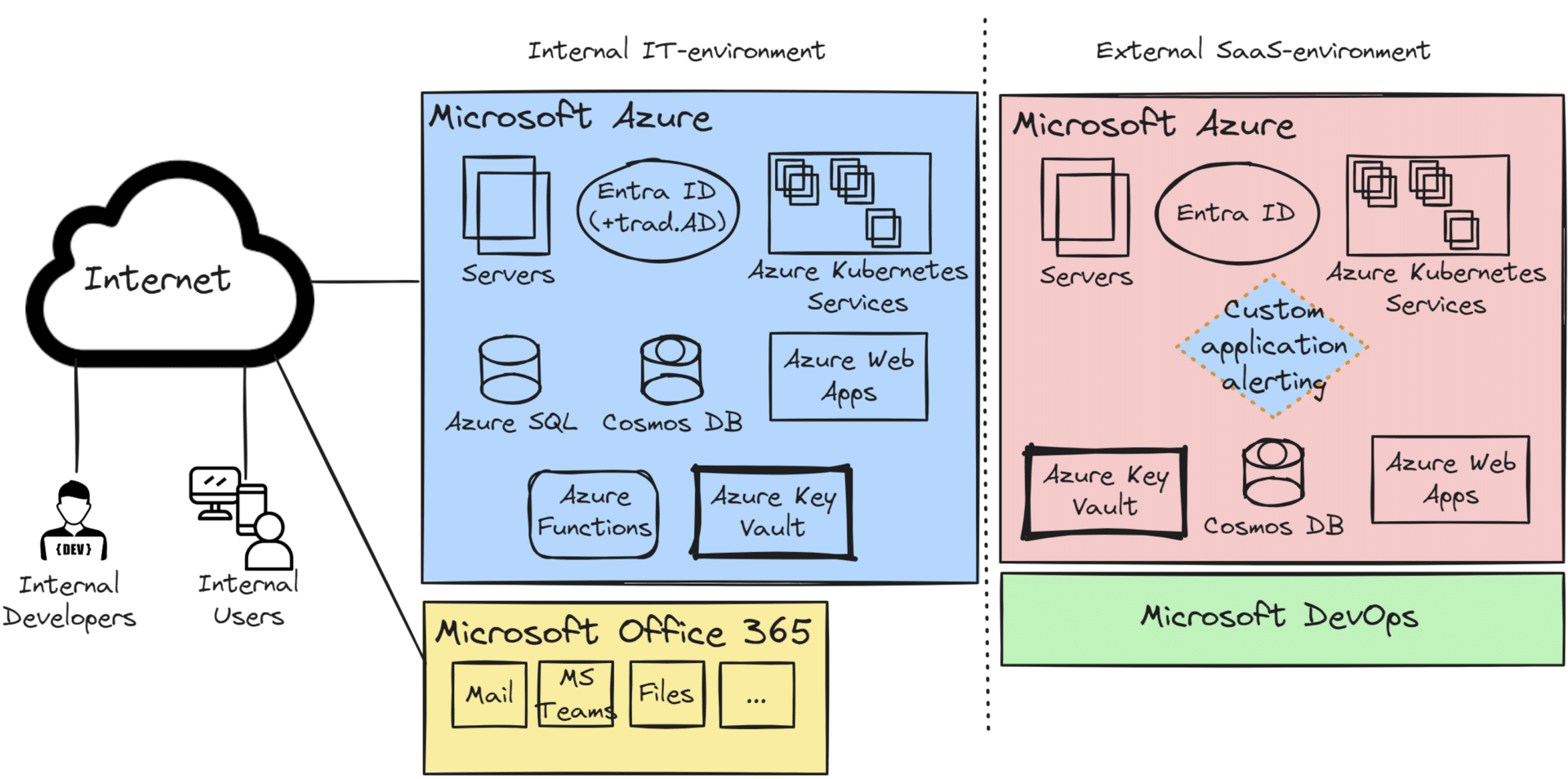
Due to the nature of delivering SaaS, Company C must also adhere to stringent security and compliance requirements. This includes ensuring data protection across all customer environments. This involves implementing robust identity and access management (IAM) protocols and encryption at rest and in transit. Regular security assessments and audits are also conducted to mitigate potential vulnerabilities.
Additionally, Company C has established a dedicated DevSecOps team to integrate security practices throughout the development lifecycle. This team collaborates closely with developers to prioritize security from the initial design phase. They ensure security remains a focus through deployment and ongoing maintenance. Automated security testing tools are used to identify and fix vulnerabilities before code is released into production. This is a key part of the process.
Furthermore, Company C’s operations team must maintain high availability and disaster recovery plans, ensuring that the SaaS solution is resilient against disruptions. This includes using Azure’s global presence for geo-redundancy and failover capabilities. Regular backup and recovery drills are also conducted to validate the effectiveness of these measures.
In summary, Companies A and B concentrate on internal IT infrastructure and custom applications. Company C takes it a step further by offering a commercial SaaS product. This adds complexity, especially in security, compliance, and operational excellence. Their software must meet internal business needs while delivering a secure, reliable, and compliant solution to customers.
How To Deploy Managed Detection and Response
The implementation of MDR (Managed Detection and Response) in Company C would be pretty much the same as in Company B.
When you have an externally published application, especially one delivered as a SaaS, it becomes more susceptible to misuse and attacks. Unlike internally published applications, these external applications face threats that are not always considered. Examples of this are hacking attacks, DDOS, account takeover attacks, API abuse, API exploitation, and so on.
The company providing the PaaS services, in this case, Microsoft, is responsible for securing the PaaS service. They also ensure that it performs as expected.
Custom Application Alerting
Company C is responsible for configuring the PaaS services and coding the entire system in a secure way. Since they deliver their application as a SaaS application, it is also Company C that is responsible for creating any sort of alerting in their application to detect miss-use or potential security breaches. This includes setting up monitoring and alerting mechanisms to detect unusual activity, such as spikes in traffic that could indicate a DDoS attack, suspicious login patterns that might suggest an account takeover attempt or abnormal API calls that could be signs of API abuse or exploitation. Custom Application Alerting is essential for monitoring the application as a whole system. It ensures that security is not limited to individual service components.
Since they deliver their application as a SaaS application it is also Company C that is responsible to create any sort of alerting in their application to detect miss-use or potential security breaches.
The security alerts that Company C creates in their application are then sent to Microsoft Sentinel. This allows them to be integrated into the Managed Detection and Response (MDR) chain.
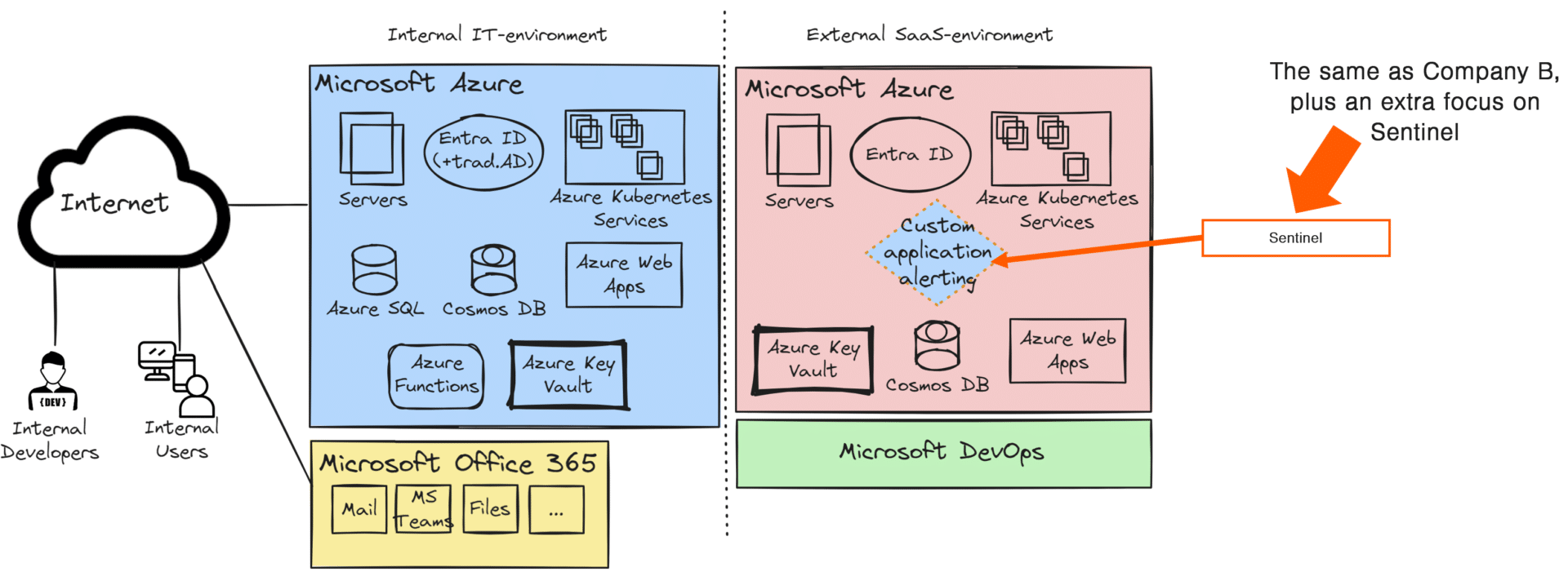
The illustration above is to highlight the thing that is most often misunderstood, and that needs to be aligned between the organization delivering the SaaS application and the organization doing the security monitoring.
Microsoft created tailored detection capabilities for Office 365 with Defender for Office 365. Similarly, SaaS providers need to develop custom detection mechanisms that are specifically designed for their unique applications. These are applications specific, and the only one that knows your application (your SaaS-application) is that ones that created it.
With this said the development team does get quite a lot of help from the different defenders for cloud products. Especially in detecting malicious behavior or the use of PaaS services. Only the team that created the application can detect misuse or patterns intended to break or breach it. This responsibility lies with those who understand the application best.
Let’s illustrate how to deploy monitoring
To clarify what we mean by “pretty much the same as Company B,” here is an illustration of how the entire environment could be monitored and protected. It is the same as the previous illustration but with all the other licenses added.
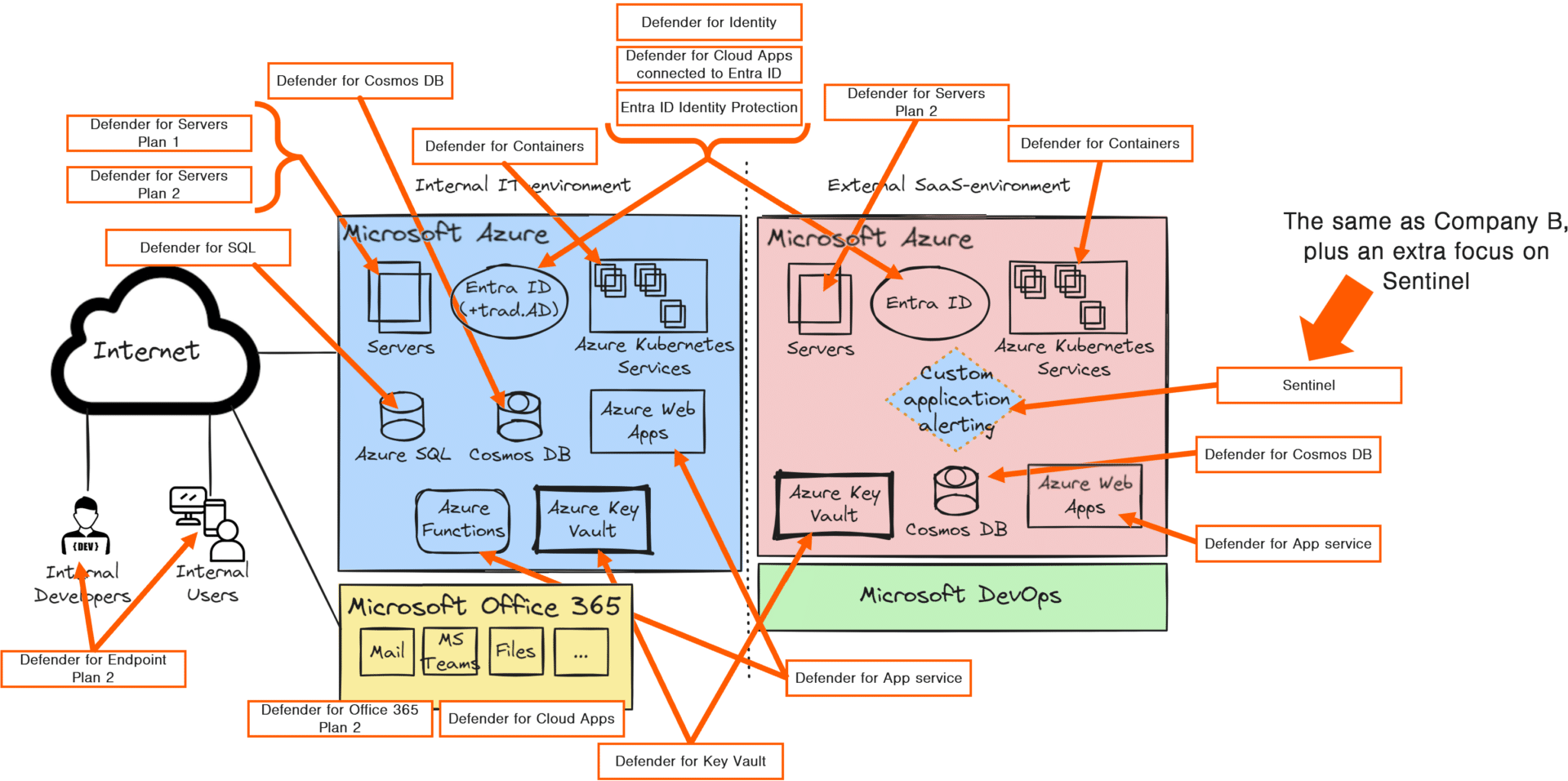
Conclusion
What we’ve observed in our discussions with customers is that while there’s a strong trust in Defender for Cloud products to protect their systems, there is sometimes an overestimation of its ability to fully understand the nuances of their specific applications. Microsoft created tailored detection capabilities for Office 365 with Defender for Office 365. Similarly, SaaS providers need to develop custom detection mechanisms that are specifically designed for their unique applications.
General errors and broad-spectrum threats are often effectively identified by tools like Defender for Cloud. However, the specific complexities and unique behaviors of your application are something that requires deeper insight. Your development team plays a crucial role in this process. By working closely with security experts, they design and implement bespoke detection strategies. These strategies are finely tuned to the unique aspects of your application.
But with this said, if we have a look into how the MDR service then is delivered, it is VERY similar to the one for Company B. From an MDR perspective, it is actually the same.
The difference is that the number of resources in each module is probably higher. This is due to the fact that the environment that’s monitored is larger.
To emphasize this once more, collaboration between the SaaS application developers and the MDR team is essential. They work together to define the necessary custom application alerts. They also determine how to investigate these alerts and decide on actions to take if a breach is detected. That collaboration is critical to make this sort of security monitoring successful.
Key Takeaways
Deploying Managed Detection and Response (MDR) solutions across varying organizational structures –such as those illustrated in Companies A, B, and C – demonstrates the versatility and scalability of MDR services. Each scenario, while rooted in similar foundational security principles, highlights the nuanced approaches required to address different operational environments and technological frameworks.
Alignment With Existing Infrastructure
How to monitor Company A
- Leveraged its existing Microsoft-centric ecosystem, integrating MDR solutions directly with Microsoft 365 and Azure. This streamlined approach maximizes existing investments and enhances security without introducing unnecessary complexity.
What to focus on in Company B
- Adapted the MDR framework to monitor a hybrid environment, combining traditional IT with advanced Azure PaaS services. The focus was on ensuring comprehensive coverage across both legacy systems and modern cloud services.
Company C also requires a higher degree of collaboration
- Emphasized the need for custom security monitoring due to its SaaS delivery model. This approach required a deeper collaboration between developers and security teams to craft bespoke detection strategies tailored to their unique application environment.
Custom Application Alerting
- Critical for SaaS Providers
As demonstrated in Company C’s case, the necessity of developing custom detection mechanisms for internally developed SaaS applications is paramount. These mechanisms should be designed to capture and respond to specific threats that are unique to the application beyond what general security tools can detect.
- Collaboration is Key
Effective security monitoring for SaaS offerings demands close cooperation between the development and security teams. This ensures that the application’s detection and response capabilities are aligned with both its operational intricacies and potential threat vectors.
Scalability and Flexibility
- MDR Solutions
The MDR approach remains consistent across different organizational sizes and complexities, allowing for scalable solutions that can be tailored to fit small businesses or large enterprises alike.
- Resource Allocation
Properly classifying resources based on their importance and business impact, as seen in Companies B and C, is crucial to ensure that critical assets receive the appropriate level of monitoring and protection.
Regulatory Compliance
- Meeting Industry Standards
Across all three companies, MDR solutions play a vital role in helping organizations maintain compliance with industry regulations. This is especially crucial for companies like Company C, which must adhere to strict security and compliance standards due to their SaaS model.
Continuous Improvement
- Proactive Security Posture
The scenarios underscore the importance of continuously refining and enhancing security measures. By regularly reviewing and updating detection capabilities (this also ties into detection engineering) and response strategies, organizations can stay ahead of evolving threats.
Lastly
In summary, successful MDR deployment hinges on understanding and adapting to the unique characteristics of each organization’s IT environment. Whether it’s leveraging existing infrastructure, integrating new cloud services, or creating bespoke security measures, the key is to build a flexible, scalable, and proactive security framework. Continuous collaboration and alignment between security operations and development teams are crucial to maintaining a robust security posture, particularly for companies delivering complex solutions like SaaS.
FAQ
The core MDR deployment for all three companies is similar, using modules like Endpoint Detection, Log Detection, Identity Protection, and 24/7 monitoring. However, the key differences lie in their IT environments. Company A uses a traditional IT framework integrated with Microsoft Azure and 365, while Company B expands this by incorporating Azure PaaS services for internal development. Company C further complicates the scenario by delivering a SaaS product to external customers, requiring custom application alerting to detect unique threats specific to their software.
Custom application alerting is essential for Company C because their SaaS product is exposed to external threats that standard security tools may not fully detect. Since the SaaS application is unique, only the development team truly understands its potential vulnerabilities. Therefore, they must create bespoke detection mechanisms to identify and respond to threats like DDoS attacks, account takeovers, and API abuse, which might otherwise go unnoticed by general MDR tools.
The MDR service assists Company C in maintaining regulatory compliance by ensuring continuous monitoring and detection across their multi-tenant SaaS environment. This includes monitoring identity and access management, encryption practices, and detecting security breaches, all of which are vital for adhering to stringent security and compliance requirements. By integrating custom alerting into their security strategy, Company C can address specific regulatory demands related to their unique SaaS product.
No, general security tools, while effective at detecting broad-spectrum threats, are not tailored to the unique vulnerabilities of a custom-developed application. For applications like those developed by Company C, which are delivered as SaaS products, it’s crucial to implement custom application alerting. This ensures that specific, application-level threats are detected and mitigated effectively.
Developers are responsible for building the application securely and creating custom detection mechanisms for threats unique to the software. Security teams, on the other hand, focus on integrating these custom alerts with broader MDR strategies to ensure a comprehensive security posture. Collaboration between these teams is critical to ensure that the application is monitored effectively and any potential breaches are promptly addressed.