LAPS – Local Administrator Password Solution
Viktor Hedberg Senior Technical Architect

What is the Local Administrator Password Solution?
Local Administrator Password Solution (LAPS) is a feature in Microsoft Windows that allows you to assume control over a local account password on each Active Directory or Entra ID joined device. This helps you to move away from the legacy approach of having the same credentials for all devices in Active Directory, and Entra ID, enabling the possibility of using Just-in-Time admin access for installing software or managing the operating system.
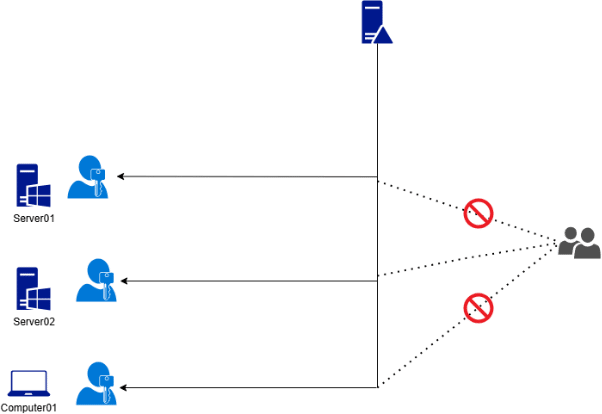
One of the main benefits of LAPS is that we can configure strict Access Control Lists (ACLs) on which user or group can access which computer local administrator password, significantly increasing the security regarding the different systems in Active Directory.
LAPS also helps with preventing the possibility of performing lateral movements in an organization, since if you only use the LAPS managed account for interactive administration (for instance via RDP), that account is local to the system and cannot therefore be used on another system.
Microsoft LAPS vs Windows LAPS
In the past, when we talked about LAPS, we meant Microsoft LAPS which required an MSI package to be installed on the systems you were targeting with LAPS to enable this feature. With Windows Server 2019 and upward, there is no longer a need to install that MSI file on the system to get it to work with LAPS, the same is applied for Windows 10.
Windows LAPS, however, can do more than “just” managing the local administrator password on the computers and servers in Active Directory. It can also be used in a cloud-native environment, with Entra ID Joined devices, you can also backup the DSRM password for Active Directory Domain Controllers via Windows LAPS.
Deployment of LAPS
The deployment of Windows LAPS and Microsoft LAPS in an Active Directory environment is quite straightforward, it consists of applying a Group Policy Object with the LAPS settings on the target Organizational Units.
The delegation is quite straightforward as well, since both LAPS solutions have a PowerShell module coupled with them allowing for a smooth enabling of LAPS and delegation of permissions to LAPS passwords.
Working with LAPS
Traditional IT Administration has been performed by using a privileged Active Directory account, logging in interactively via Remote Desktop Protocol to administer a server. This way of working is exposing your credentials to potential credential theft. As this connection is made, a hash of your password is stored on the system you are connecting to in the working memory of that system.
Meaning that if you sign in via native RDP to a member server using Domain Admin credentials, your Domain Admin password hash is stored on the member server, allowing any user with administrative privileges on that server to dump the Local Security Authority Subsystem Service (LSASS) and harvest your credentials to perform a pass-the-hash lateral movement.
By working with a LAPS managed account instead of your Active Directory account, we are minimizing the blast radius of an account compromise. If the LAPS account for your file server is compromised, it means that the blast radius is contained to that file server. Since the LAPS account is a local account, it cannot be used for pass-the-hash types of attacks.
You need to adapt the way you are managing your IT-infrastructure when using LAPS. Instead of relying on traditional ways of working, you only use the LAPS account for RDP connections, this leads to a higher security posture throughout the environment, and when LAPS is in full effect coupled with Active Directory Tiering, the environment contains enough speed bumps to halt an attackers progress throughout the environment, forcing them to become more visible and noisy, allowing the detection capabilities to spawn alerts, and highlight the fact that an active actor is in the environment.
How to Use LAPS in Day-to-Day Operations
Microsoft LAPS (Legacy LAPS)
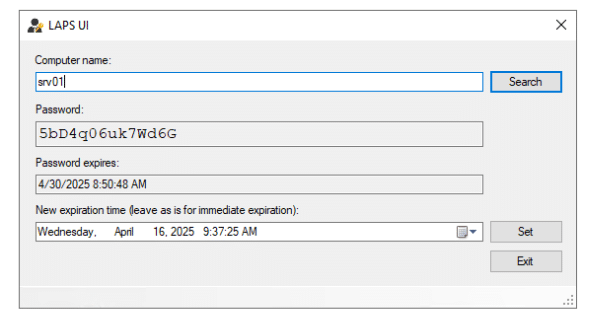
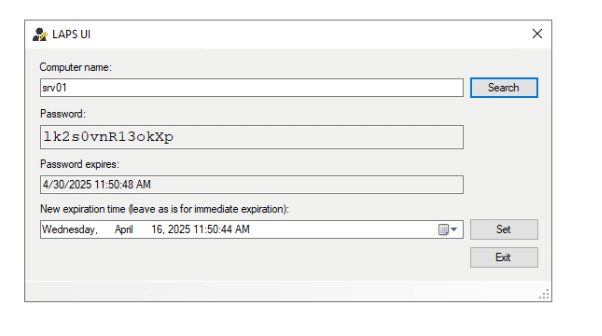
In Microsoft LAPS, we can use a native tool called LAPS UI, to simply search for a system, and get presented with the LAPS password, and the expiration of said password. We copy this, and logon to the server.
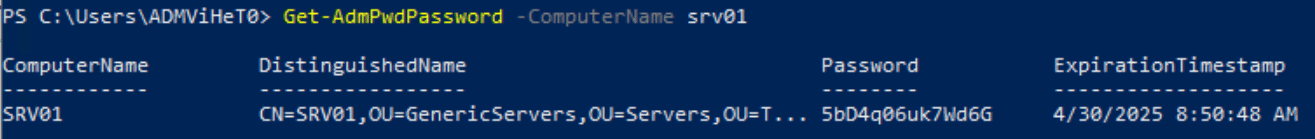
We can also leverage the PowerShell module for Microsoft LAPS to get the LAPS password by running the “Get-AdmPwdPassword” cmdlet.
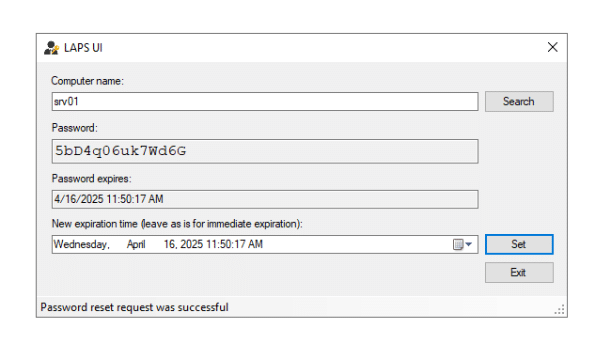
Once the work is completed, we can leverage the LAPS UI to force a reset of the password by leaving the timestamp as is and clicking “Set”. We could also specify that the password will be reset at a specific time, allowing the technician to complete their task prior to the reset.
To validate the password change, we once again search for the computer object in the UI and are greeted with the new password.
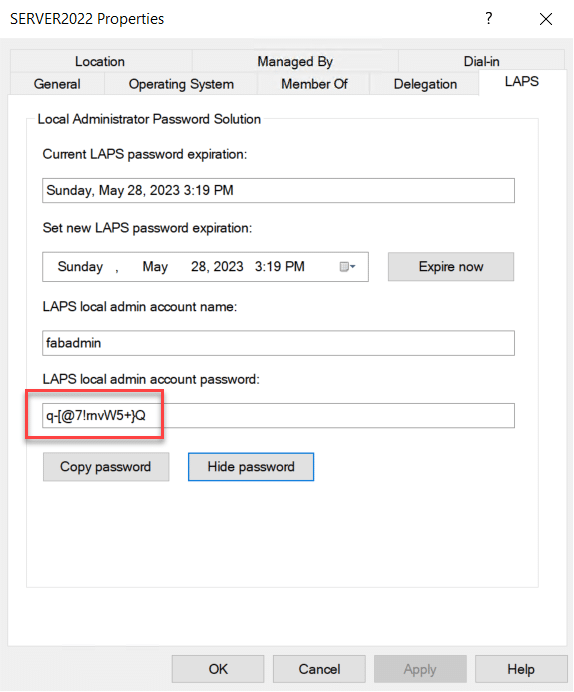
Windows LAPS
For Windows LAPS, we can look directly at the Active Directory object by simply searching for the system in Active Directory Users and Computers (ADUC) or Active Directory Administrative Center (ADAC).
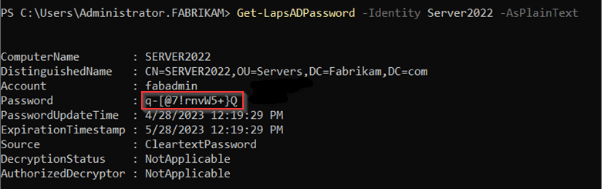
Windows LAPS also of course supports the use of PowerShell, but with a new cmdlet called “Get-LapsADPassword”.
The same modus for forcing a reset of the password is in place for Windows LAPS.
Windows LAPS in Entra ID
If you are storing your computer’s LAPS password in Entra ID, we need to use the LAPS feature there to get ahold of the password. This requires API permissions in Entra ID, and one thing to be wary of in this setup is that you cannot be as granular as in on-premises when delegating permissions to read LAPS passwords. You can either read all the LAPS passwords, or none.
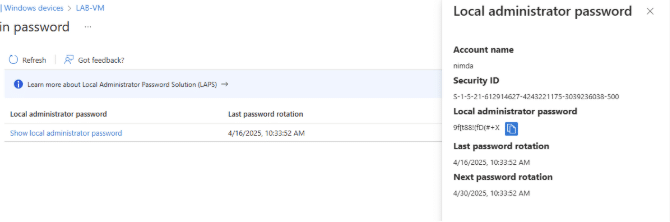
In Entra ID, we do not have an option to force a reset once the password has been used. However, the policy in Entra allows for an immediate password reset once the managed account signs out from the device.
Drawbacks with using LAPS
The biggest drawback when using LAPS is that you lose tracability on who grabbed the local password, as the auditing in both Active Directory and Entra ID does not register these events. Which could lead to difficulties in determining which user used the password and performed actions on a managed system.
But with that drawback in mind, using LAPS still reduces the blast radius significantly in the event of account compromise.
Summary
LAPS is an efficient and effective tool to prevent accidental spread of sensitive credentials on systems joined to Active Directory.
While the issue of lateral movement does not exist in the same manner in Entra ID, the feature is still a good option to pursue if you want to limit your end-users from being local administrators on their own devices.