OT – MDR for Operational Technology

Operational Technology Enables Modern Society – What You Need To Know To Start Detecting Breaches
What Is OT (Operational Technology)?
Imagine you’re in a factory, a power plant, or even controlling a train system. Operational technology (OT) is the technology that makes all of this work smoothly. OT environments are integral to our industries and societies, managing everything from manufacturing processes to critical infrastructure. Consequently, these systems are facing an increasing threat from sophisticated cyber attacks.
Why We Need Managed Detection and Response (MDR) for OT
Securing Operational Technology, or OT, systems requires a unique approach, quite different from what we usually do for regular IT systems. Imagine OT systems as the engines of critical facilities like factories or power plants. You can’t simply turn them off with a “kill switch” like you might with a computer. These systems are not just complex; they’re essential and must be watched over every minute.
Now, here’s where things get interesting. To keep these systems safe from cyber threats, you need more than just your standard security measures. This is where Managed Detection and Response, or MDR, comes into play. MDR isn’t your average security guard; it’s more like a highly skilled team that’s always on duty monitoring these mission-critical systems in real time. They’re always watching, ready to spring into action the moment they detect something fishy.
That’s why MDR services are vital in the OT world – they’re tailored to meet the unique needs of these complex systems. Think of MDR as a vigilant protector, constantly scanning for threats and ready to respond swiftly to keep everything safe. But MDR doesn’t just stop at security. It also plays a crucial role in ensuring these systems work efficiently and without interruptions.
In essence, MDR’s dual role is what makes it so crucial for OT systems. It’s not just about putting up a shield against cyber threats; it’s also about ensuring that these critical systems continue to do their job effectively.
Imagine OT systems as the engines of critical facilities like factories or power plants. You can’t simply turn them off with a “kill switch” like you might with a computer.
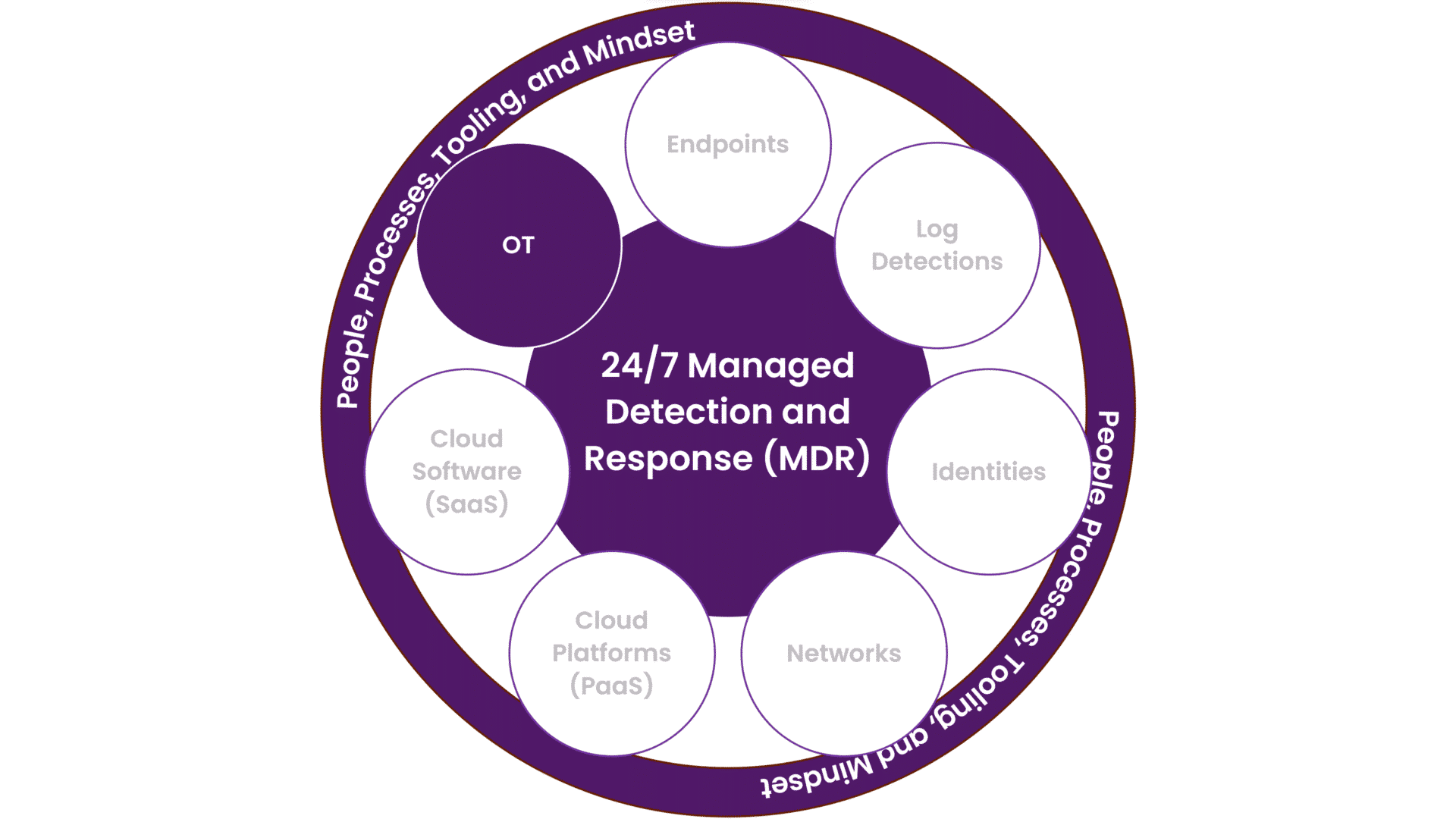
Securing OT, ICS, and SCADA With MDR
There are basically two ways of deploying MDR for Operational Technology:
- A network sensor that listens on a mirrored port to avoid disturbing operations.
- Installing an agent on the OT device.
Each option has its pros and cons; however, our experience indicates that the first is more commonly used in OT environments.
By deploying a sensor (hardware or virtualized) and mirroring the traffic on the OT network, there’s no additional load on the OT devices. Essentially, this approach requires no changes or configurations to the OT devices. Instead, the sensor is connected to a span-configured network port, enabling it to listen to all traffic sent in that network. The sensor then performs deep-packet inspection (DPI) that understands industrial protocols.
Alternatively, installing an agent on the OT device is more closely related to how EDR agents are deployed and monitored in IT environments. The upside is that IT departments often have the processes and knowledge to do this; the downside is that it requires the actual installation of software on the devices, and that, in some cases, can affect the performance and/or guarantees from suppliers.
The Rising Threat Landscape in OT, ICS, and SCADA
OT has been around for decades now – it’s not new technology. What’s happened is that the systems are becoming more and more connected to the rest of the world (via the internet or other networks) and are no longer their own world. Undeniably, Industrial Control Systems (ICS) and Supervisory Control And Data Acquisition (SCADA) systems are integral parts of our society.
Our increasing reliance on these systems, coupled with their growing interconnectivity, creates greater opportunities for threat actors to disrupt systems. In the worst cases, they can make changes to systems that affect water, electricity, or other critical infrastructure within our society.
“Recognition of the cyber threat to industrial control systems (ICS) and operational technology (OT) systems has grown over the last decade. Until recently, this has been largely a theoretical threat founded on the danger of what could happen rather than what is happening. This is changing, and the threat to ICS/OT is now real and ongoing.”
Kevin Townsend – Securityweek.com
Capabilities and Questions Answered by MDR for Operational Technology
As IT and OT are converging, the different worlds have to coexist and work together. With that, there are also many common questions for IT personnel that are now also applicable to OT, such as:
- What OT devices do I have?
- How are the OT devices connected?
- What vulnerabilities do I have?
- How do I prioritize mitigation?
- Are there any active threats, and how do I stop them?
- Where is the unexpected packet flood coming from?
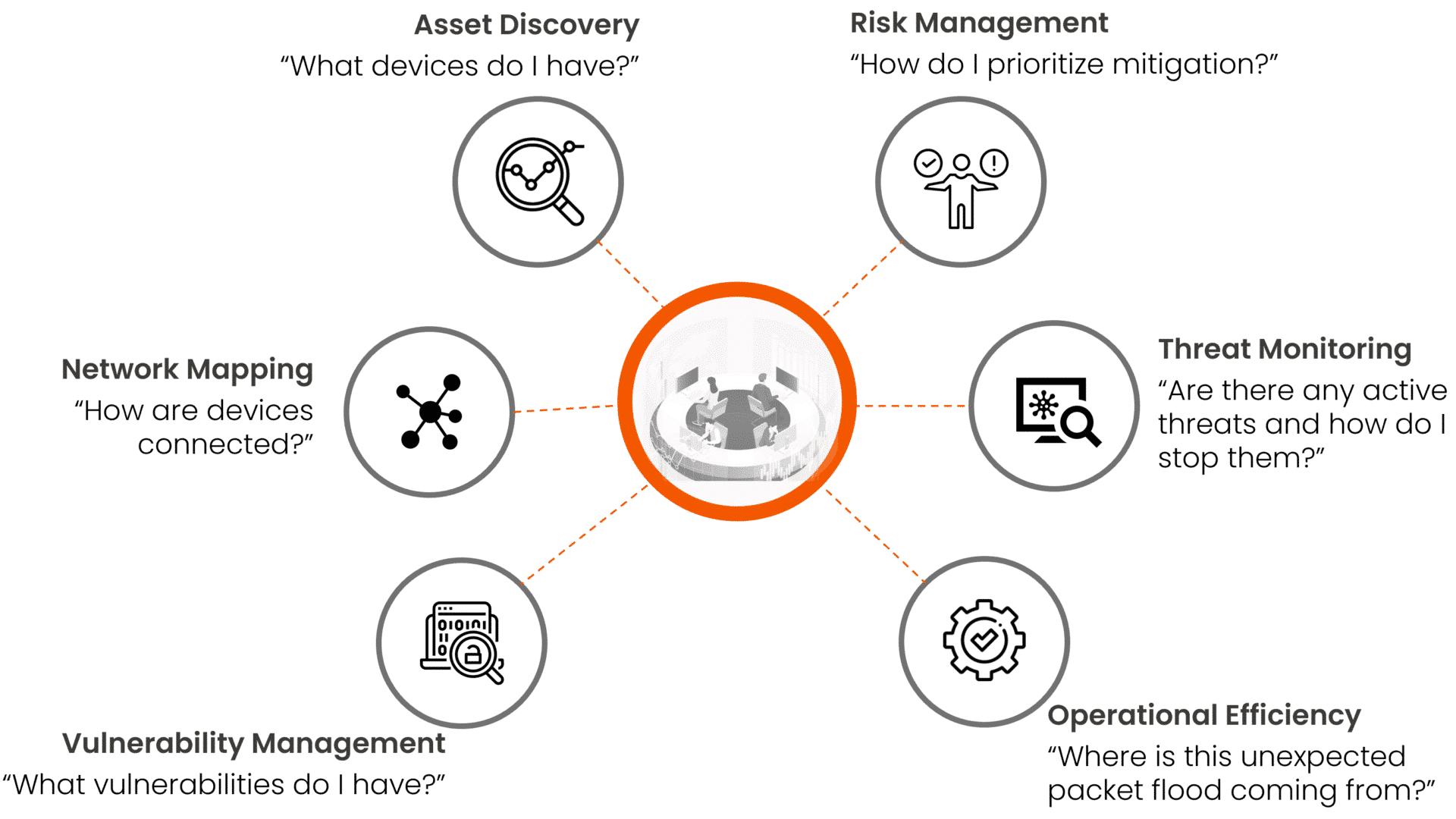
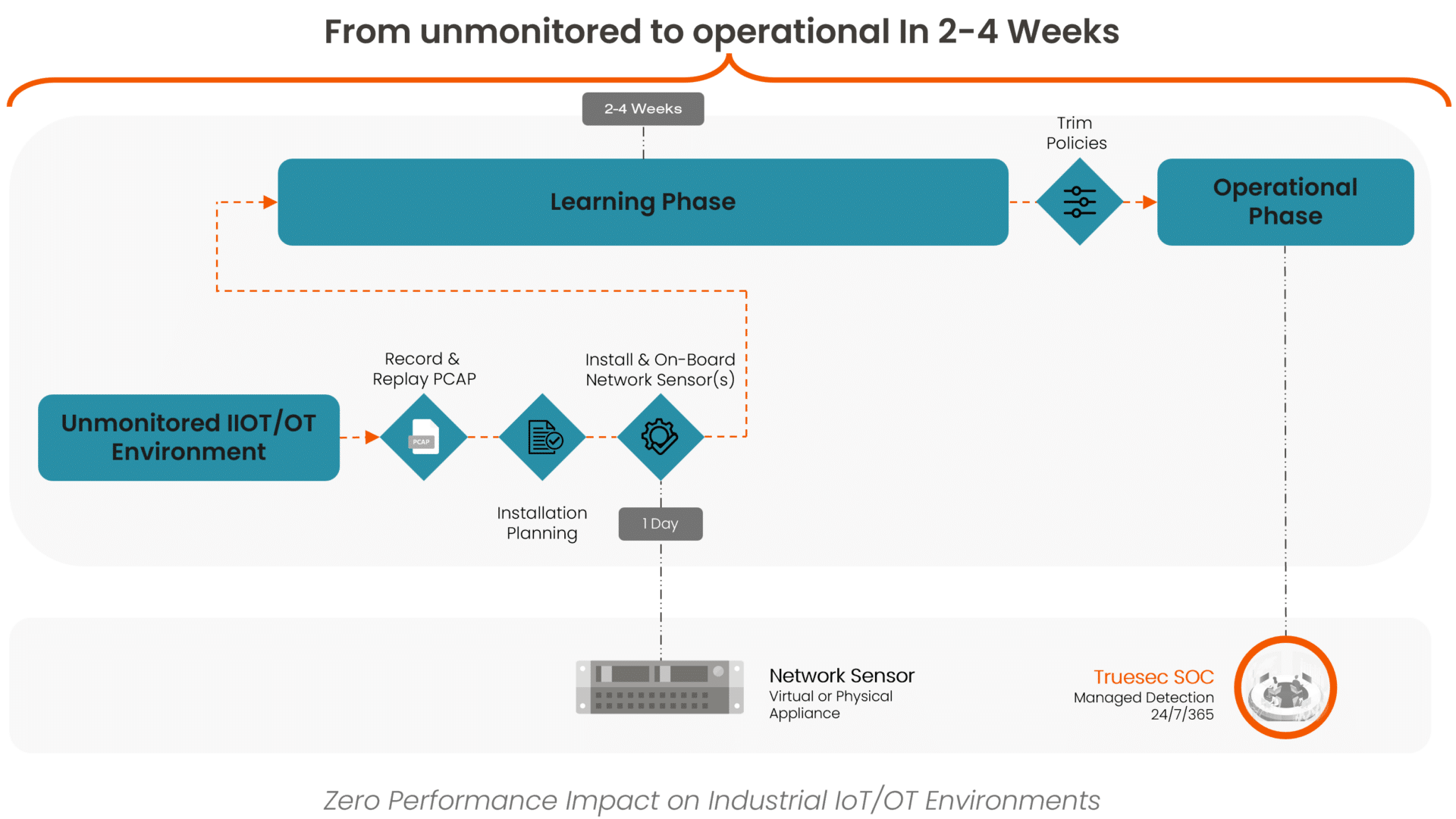
What the Deployment Journey Looks Like
As OT and IT converge, the most effective SOC solutions monitor both environments holistically. Firstly, this approach enables deeper analysis of cross-environment alerts, improving accuracy. Secondly, it also facilitates threat hunting across IT and OT boundaries, which is crucial for detecting lateral movements like ransomware attacks.
In our experience with diverse industrial clients in the Nordics, we understand the uniqueness of each customer’s needs in this emerging field. At the same time, we advocate a step-by-step deployment strategy, emphasizing close collaboration for optimal implementation.
- Define what key sites to start with to do a Proof of Value (PoV) and enable some key learnings.
- Apply the learnings beyond to implement the solution at scale across sites.
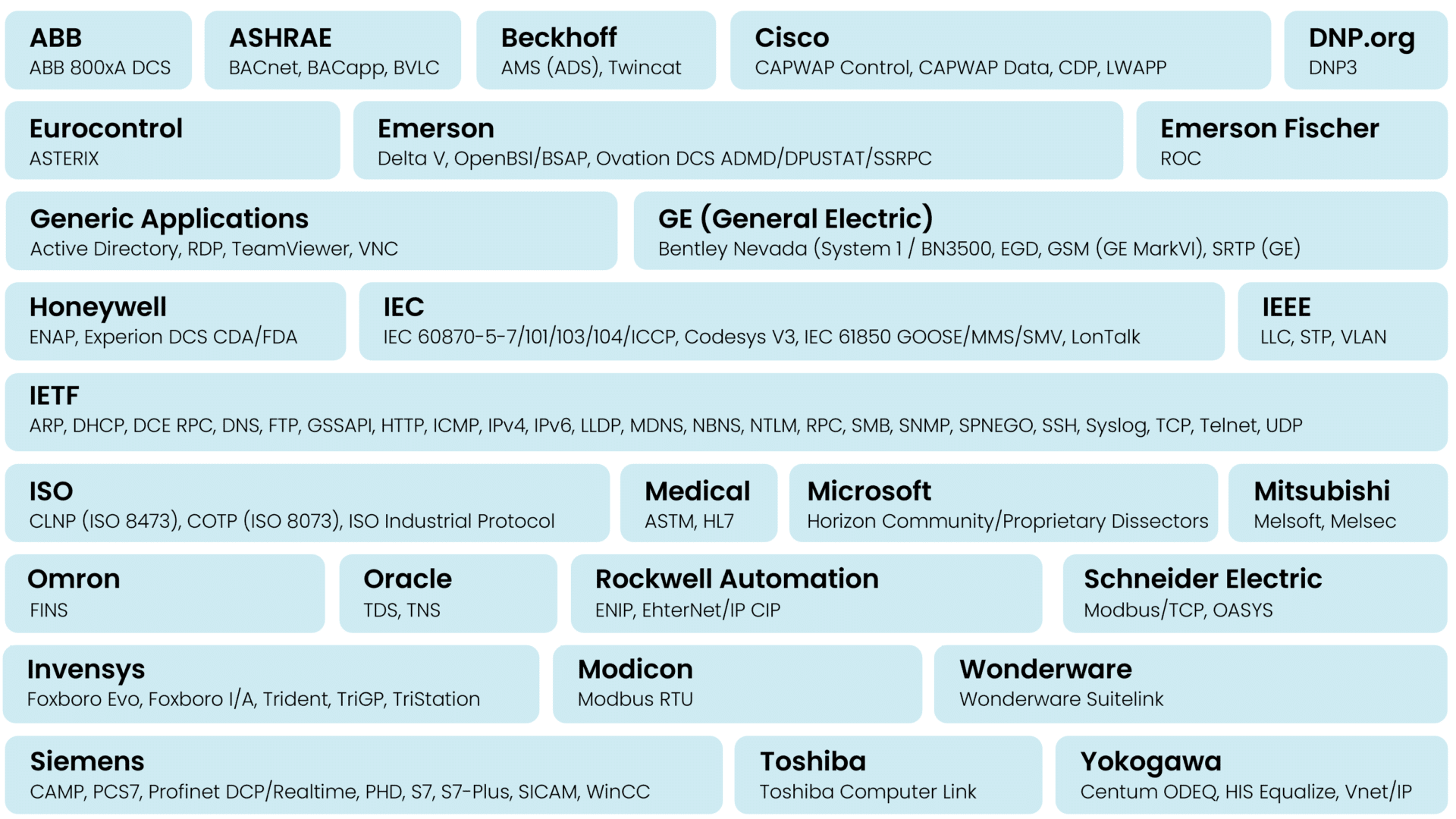
Broad Support for OT Protocols
IT and OT network protocols differ significantly in purpose and design. Generally, IT protocols, like TCP/IP, HTTP, and FTP, focus on rapid data exchange and are essential for data management and internet communications. They emphasize speed, efficiency, and scalability, catering to a wide range of industries. On the contrary, OT protocols, such as Modbus, DNP3, and PROFIBUS, are critical in industrial control systems. They prioritize reliability, safety, and real-time control, ensuring uninterrupted operation and control of physical processes in constrained environments.
The tools for monitoring OT environments are maturing and evolving, meaning that support for new protocols and new hardware are continually being added. The following are examples of protocols that are currently supported:
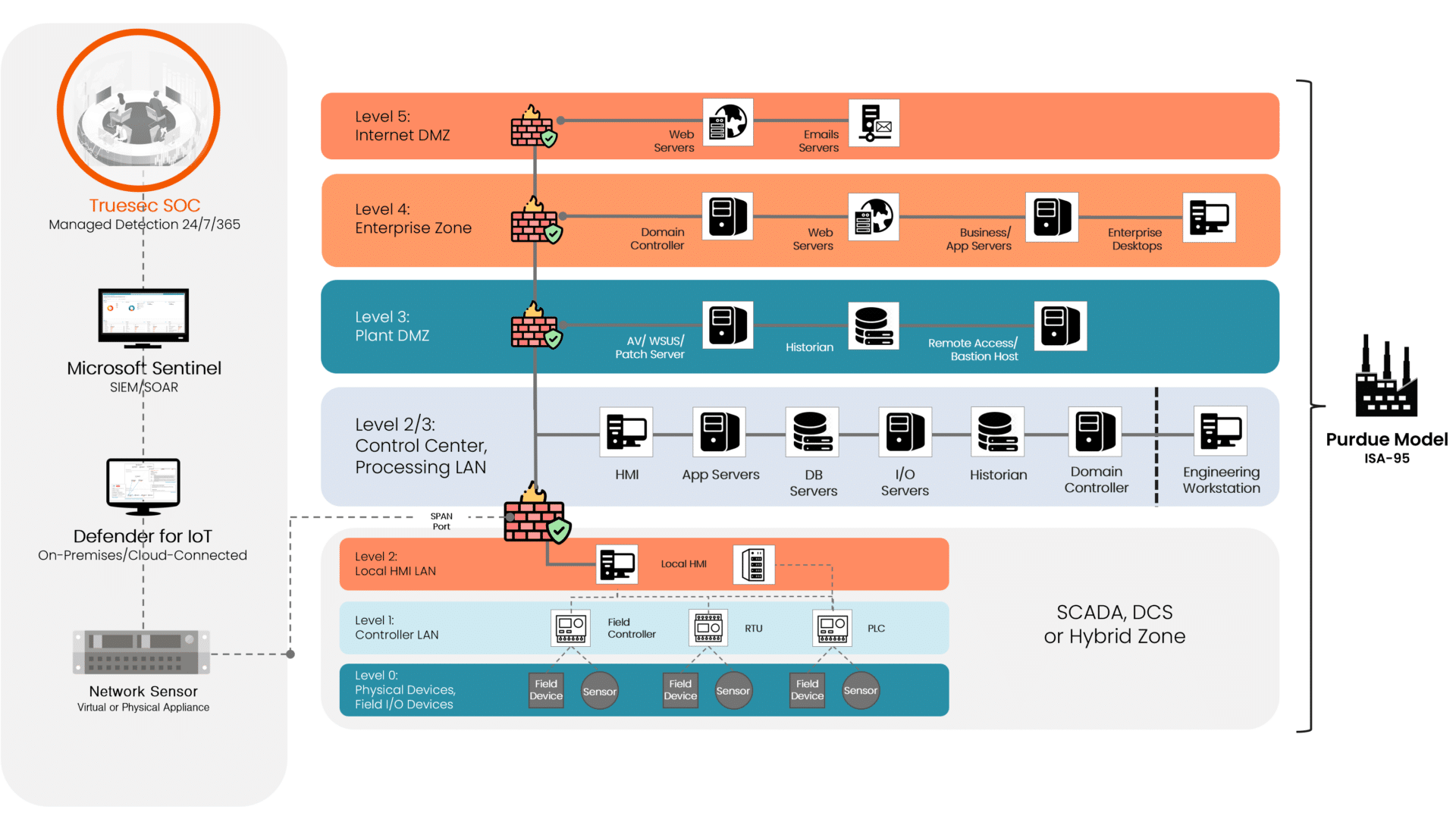
Network Architecture To Implement MDR for OT
To deploy MDR for OT using the Purdue Model, the process integrates with the existing network’s layered structure. With its hierarchical levels, the Purdue Model allows for strategic placement of MDR systems at critical points. This ensures effective monitoring and response across different network layers, from the enterprise level down to industrial control systems. The approach tailors security measures to the unique needs of each layer, enhancing overall network security in the OT environment.
FAQ – Common Questions Regarding MDR for OT
We at Truesec’s Security Operations Center (SOC) actively pursue continuous improvement and quality control. We regularly assess new products and rigorously monitor existing ones to ensure they meet the demands of a modern SOC. This process guarantees that our capabilities remain at the forefront of cybersecurity excellence. We currently use Microsoft Defender for IoT.
No, that’s impossible because the network sensor only listens to port-mirrored traffic; it’s a one-way communication.
A note here is that the network switch or router to which the network sensor is connected must have available capacity. So before connecting the network sensor or configuring mirroring, CPU usage must be checked. What could happen otherwise is that if the switch was close to its maximum capacity before, then it might start to drop network packages. This is a short check before configuring the mirroring, but a step that should not be forgotten.
The service provides comprehensive protocol support. In addition to embedded protocol support, it’s possible to analyze proprietary and custom protocols or protocols that deviate from any standard. Developers can use the Horizon Open Development Environment (ODE) SDK to create dissector plugins that decode network traffic based on defined protocols. Use Horizon to:
– Expand visibility and control without the need to upgrade to new versions.
– Secure proprietary information by developing on-site as an external plugin.
– Localize text for alerts, events, and protocol parameters.
This unique solution for developing protocols as plugins doesn’t require dedicated developer teams or version releases in order to support a new protocol. Developers, partners, and customers can securely develop protocols and share insights and knowledge using Horizon.
Microsoft Defender for IoT, designed for NDR, offers flexible deployment options. You can install it on both physical hardware and virtual machines. This versatility allows it to adapt to various network environments. See Microsoft’s documentation on certified physical appliances at https://docs.microsoft.com/en-us/azure/defender-for-iot/organizations/ot-pre-configured-appliances and for certified virtual appliances at https://docs.microsoft.com/en-us/azure/defender-for-iot/organizations/ot-virtual-appliances
The sensors and agents continue to run and store data as long as the device is running. When the device regains connectivity, security messages resume sending.
Defender for IoT enters this mode while actively learning your network activity. This activity becomes your network baseline. Defender for IoT remains in learning mode for a predefined period after installation. Activity that deviates from learned activity after this period will trigger Defender for IoT alerts.