SIEM/SOAR – MDR With Log Detections

Understanding Managed Detection and Response With Log Detection
Log Detection Explained
Over the years, the capabilities of SIEM have matured beyond log management into a security information and event management (SIEM) solution. Today, SIEM offers advanced user and entity analytics and is enabled to harness the power of AI. Understandably, SIEM has become a quintessential solution for many CISOs worldwide.
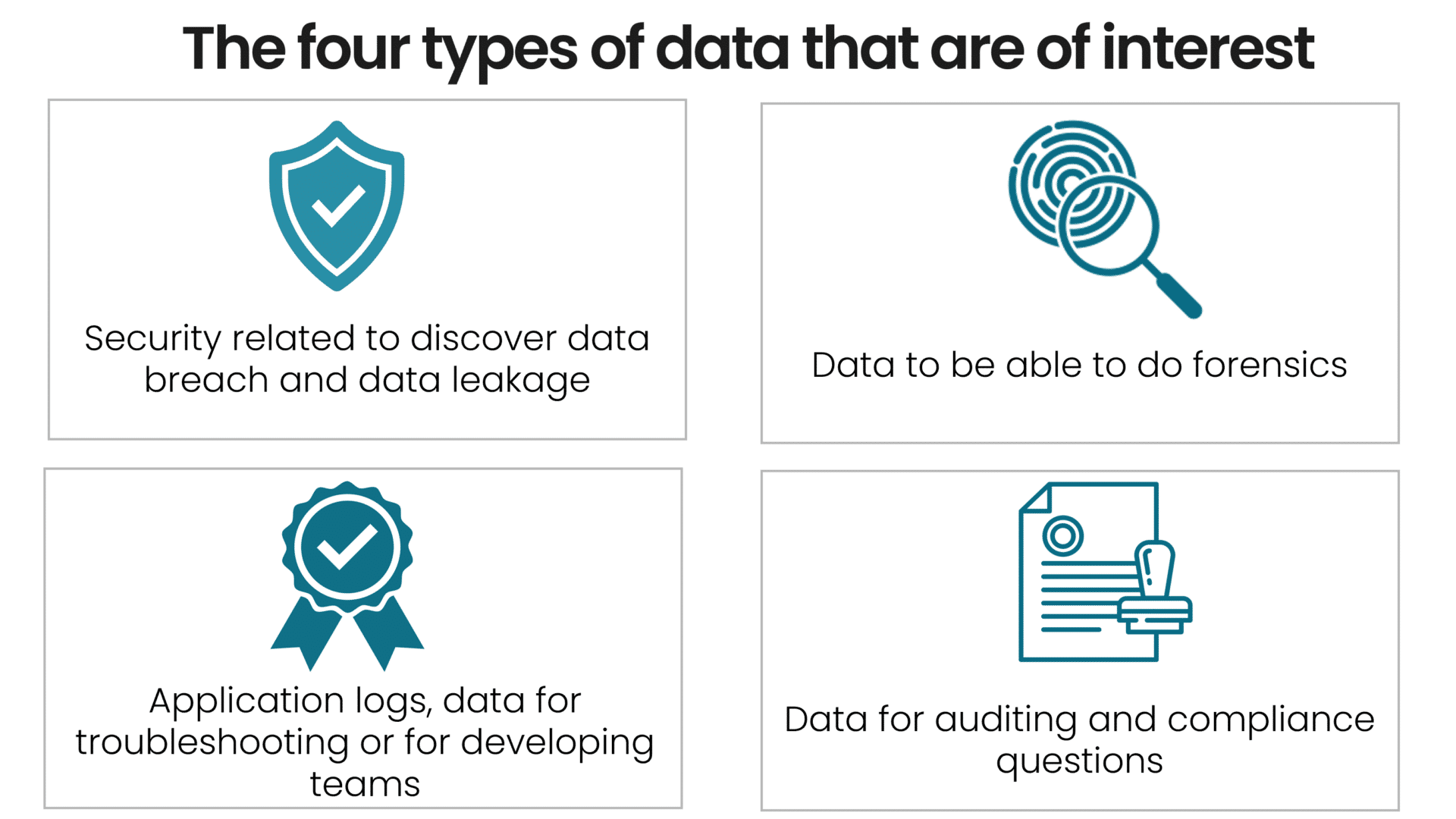
SIEM systems show significant variations among different vendors. However, they commonly incorporate data to deliver four essential use cases:
- Data used to detect data breaches and data leaks (this is the primary focus of our MDR service).
- Logs with information used for forensic investigations (e.g., to assist in cases involving intellectual property theft, forgeries, employment disputes, or incident response investigations).
- IT operations or development activiteies use application logs and data for continuous quality improvement.
- The organization uses data and reporting for auditing and compliance to ensure adherence to external rules, regulations, policies, and customer requirements.
How Truesec Uses SIEM
Truesec’s primary focus is to prevent cybercrime, so we concentrate on helping our clients detect and prevent attacks in real time, 24/7, from our SOC.
Consequently, our focus for the capabilities in a SIEM solution is geared towards detection, response, and attack prevention. Notably, a SIEM is an excellent tool for incident response (IR), conducting forensic investigations, quality monitoring and troubleshooting, and auditing and compliance requirements.
Log Detection vs. SIEM vs. SOAR? What’s the Difference?
As is very common in IT, and maybe even worse in the cybersecurity world, there are many words that are used without any explanations. So, let’s try to correct that.
All in all, Log detection, SIEM, and SOAR are all pivotal in cybersecurity but serve different functions.
Log Detection
Log detection involves identifying and analyzing log files for security threats. It is basically about conducting threat detection on log information. Security information and event management (SIEM) systems are the preferred choice for log detection due to their specialized security data analysis and aggregation capabilities. While syslog has been used in the past, experts like Truesec do not recommend it for security detection. Syslog, effective in various other applications, lacks the specific design for security threat detection, a gap that SIEM systems fill effectively with advanced security monitoring features.
SIEM (Security Information and Event Management)
SIEM goes further by aggregating and analyzing data from various sources for real-time security monitoring and incident response. A SIEM system can ingest data and logs from many types of systems and applications and can, therefore, be a very versatile tool in the cybersecurity toolbox.
SOAR (Security Orchestration, Automation, and Response)
SOAR focuses on automating and managing complex security operations and workflows. Understanding their unique roles helps in creating a comprehensive cybersecurity strategy. SOAR systems are very often used in combination with SIEM systems. SIEM systems are used to detect threats, and SOAR systems are then used to respond to and mitigate threats.
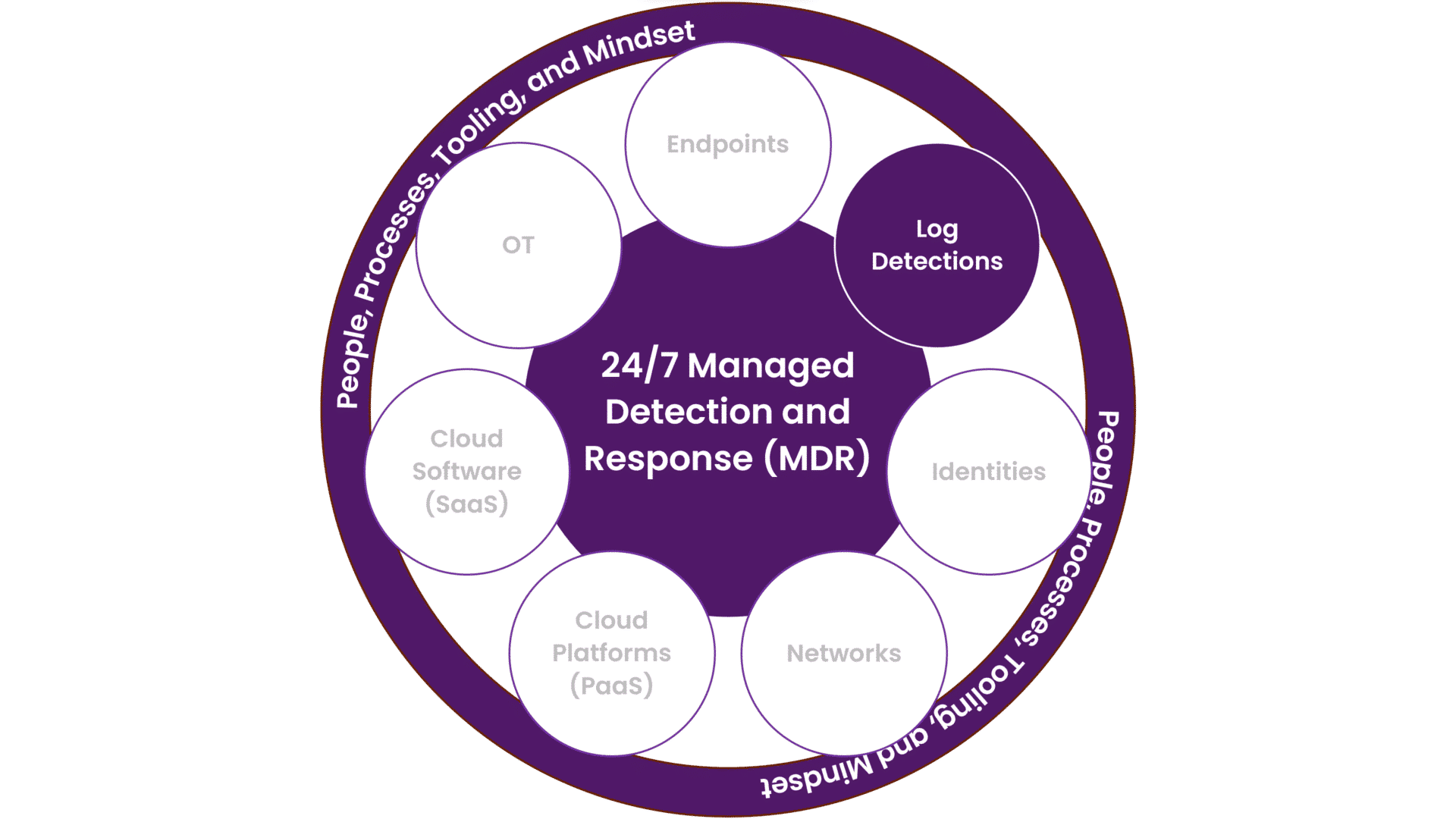
Where Detection on Log Data Really Shines
SIEM is particularly suitable for systems where EDR/XDR technologies cannot be deployed. SIEM detection capabilities will augment our SOC delivery and complement other relevant security technologies to strengthen cyber resilience and increase your detection and analytical capabilities.
Log detection is also, in many cases, a good addition when using other managed detection and response approaches like cloud platforms, identity, or network detection. The log detection solution can collect information from other sources, enhance the detection capability of the SOC, and provide insights into different perspectives of what’s happening in the environment.
We actively augment our use cases and rulesets with a blend of internal and external data. This includes insights from Truesec’s incident response investigations, threat intelligence, red team exercises, infrastructure insights, and findings from our Managed Detection and Response customers. Additionally, we incorporate information from external sources, ensuring our detection capabilities are up-to-date and relevant to the latest cybersecurity challenges.
With our MDR service, Truesec will assist your organization in deploying the detection capabilities in your SIEM platform and help you prioritize the log sources you’ll need to build an effective cyber defense. We’ll maintain and enhance your detection capabilities and use cases relevant to your environment today and tomorrow.
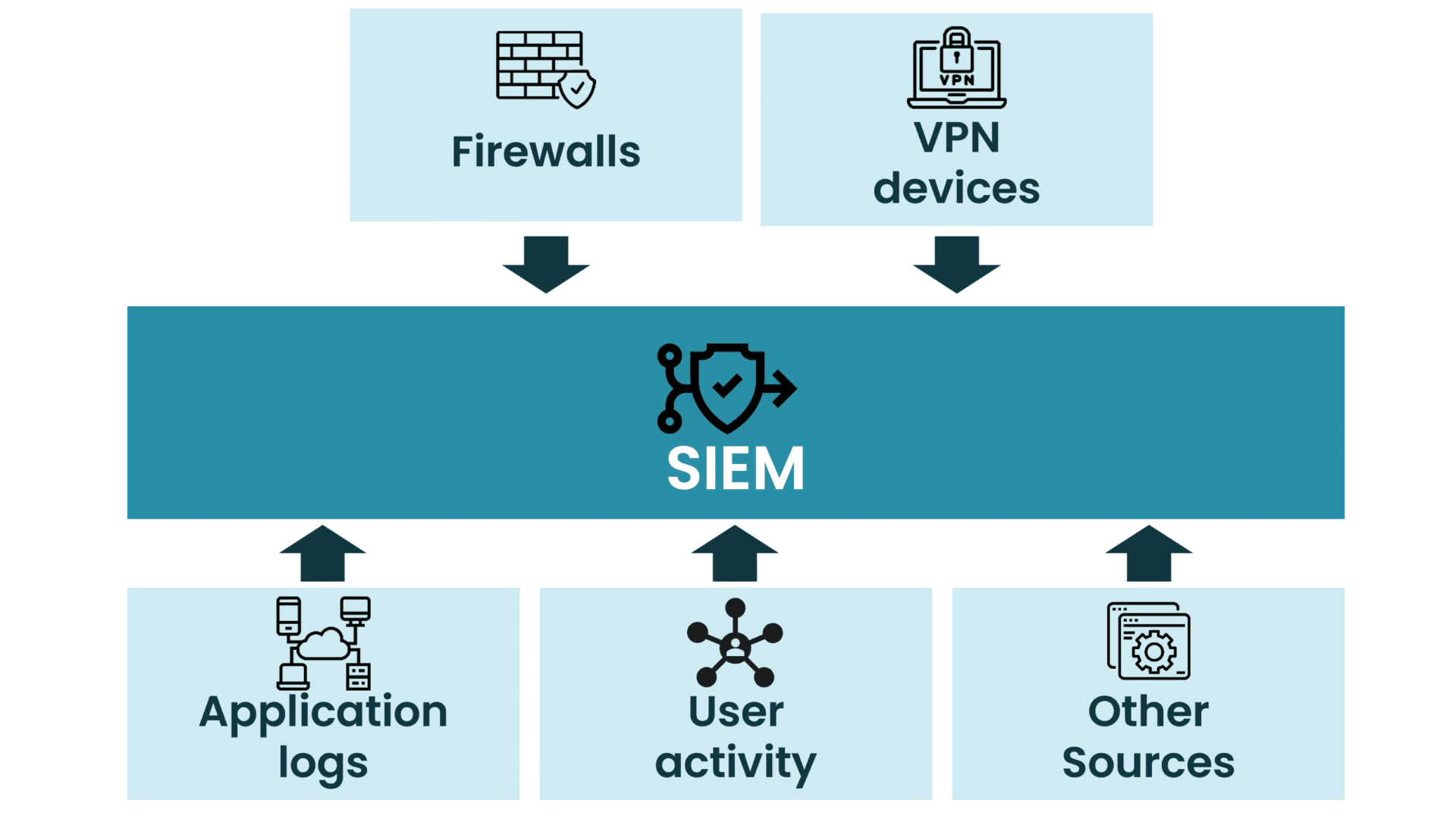
Commonly Used Log Sources
There are massive amounts of logs in most IT environments. To store all logs is not economically justifiable. At Truesec, we focus on threat detection; therefore, some of the most commonly used sources are:
- Firewalls
- VPN Devices
- Application Logs
- User Activity
- Other Sources

Platforms
Our SOC supports the following SIEM solutions:
- Microsoft – Sentinel
- CrowdStrike – Falcon LogScale/Humio
- Splunk – Splunk Enterprise
- Google – Chronicle SIEM
Log Detection vs. Log Management
In our managed service for log detection, we’ll ensure that the detection for breaches and data leaks is updated and monitored.
At the same time, as noted previously, there are many different uses for logs and log data. The flow of log data can be handled in many different ways, and we usually work with the customer to ensure we understand the business needs and requirements.
When hiring a consultant to set up a log management environment, you’ll get the expertise to help you design and implement a system that suits your specific needs. This includes setting up the infrastructure to collect, store, and analyze logs from various sources across your environment, such as servers, applications, and network devices. Also, since there are different data consumers and different usage patterns, the implementation of log management considers who should access what and when. Also, when working with compliance, we often help create or validate compliance reports.
The primary difference between these two is ownership and responsibility. In log management consulting, the consultant helps you build your own system and processes, but your team is ultimately responsible for running and maintaining it. We then use that system to deploy the log detection capability.
Other Log Sources That Are Often Used
As mentioned multiple times, the number of log sources is practically endless.
We commonly observe certain logs in various deployments that are particularly useful for forensic analysis. It’s important to note that many of these logs don’t necessarily require integration into a SIEM solution. Other log management systems are often sufficient and can be more cost-effective, depending on the specific use case.
- Active Directory (e.g., via Defender for Identity)
- Any local logs on non-standard OS devices (e.g., factory machine X)
- Application Logs (especially for internet-facing or sensitive applications)
- Azure Active Directory Audit Logs
- Azure Active Directory Sign-in
- Azure Activity Logs (Monitoring, e.g., who modified a virtual machine)
- Azure AD Connect Health Logging (incl. for AD FS)
- Azure Identity Protection Logs (risky user/sign-in)
- Azure Privileged Identity Management Audit Logs/History
- Azure Storage Account Logs
- Backup Logs
- Central Management Systems (e.g., SSCM)
- Container Logs
- Container Management Systems (Kubernetes, OpenShift, Docker, etc.)
- Database Logs
- DHCP Logs
- DNS Logs
- Facility-Access Control Systems
- Firewall
- GCP (configured according to best practice)
- Identity Management Logs
- Load Balancers
- Logs Associated With Code Management (e.g., Git Repository Logs)
- Logs/Data From Vulnerability Scanners or Other Types of Scanners (e.g., Asset Management)
- Mobile Device Management (MDM) Logs (e.g., Intune – Avoid MFA on Registering Their Device)
- Network Management System Logs
- Office365 Unified Audit Logs
- Proxys
- Remote Access/Remote Desktop (e.g., Citrix, Zscaler, NetScaler, RDGW, Windows 365)
- Storage Logs (e.g., NAS)
- System Management System Logs (e.g., Lansweeper)
- Virtualization Layer Logs
- VPN
- Web Application Firewall (WAF)
- Webserver Logs
- Wifi
This is a very long list, and not all are usable by everyone. Please contact our team to discuss your specific use case and the problem you need to solve. Together, we’ll find an effective solution that meets your needs.